Understanding Blockchain Fundamentals, Part 2: Proof of Work & Proof of Stake
2018-03-01 09:16
573 查看
In part one, we discussed the Byzantine Generals Problem, how to achieve Byzantine Fault Tolerance, and how this all relates to blockchain.The algorithm in the previous article is in fact a solution which achieves Byzantine Fault Tolerance. However, that solution is not efficient enough, and its variations have constraints, namely that less than a third of the network is dishonest.

Running time of solving the Byzantine Generals Problem with the algorithm proposed by Lamport, Shostak and Pease (n = number of actors, m = number of traitors)That leads us to a classic question in Computer Science:Can we do better?The topic of the present article will discuss alternative algorithms which achieve Byzantine Fault Tolerance.Note: Please bear with any simplifications that I make. These algorithms have a lot of complex research behind them. I will be providing links as we proceed for the interested reader to do their own further research.Blockchains use consensus algorithms to elect a leader who will decide the contents of the next block.That leader is also responsible for broadcasting the block to the network, so that the other peers can verify the validity of its contents.
When given a solution to that problem it is easy to verify that it is correct
Whenever a new block is mined, that miner gets rewarded with some currency (block reward, transaction fees) and thus are incentivized to keep mining. In Proof of Work, other nodes verify the validity of the block by checking that the hash of the data of the block is less than a preset number.Due to the limited supply of computational power, miners are also incentivized not to cheat. Attacking the network would cost a lot because of the high cost of hardware, energy, and potential mining profits missed.The picture illustrates very well how Bitcoin, and any other coin that uses Proof of Work, discourages malicious behavior.
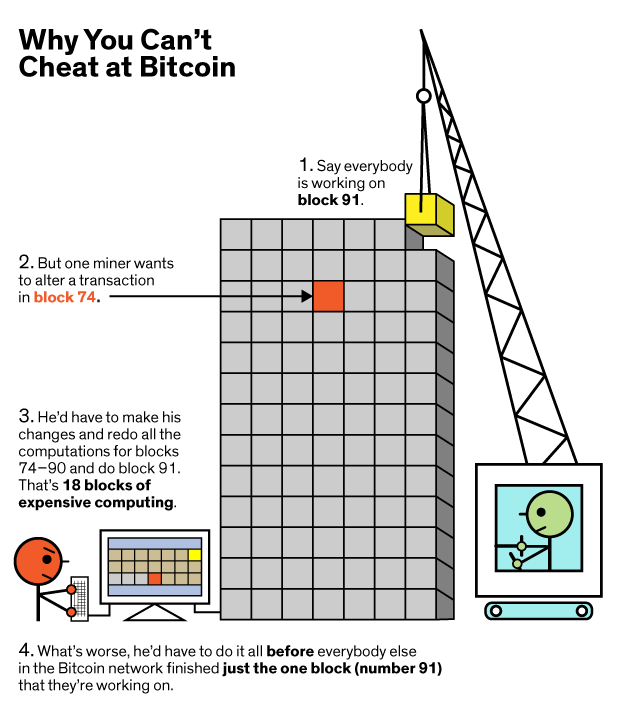
For the readers who are interested in how chain-splits (a.k.a. forks or chain reorganizations work in the case of a disagreement, I suggest this article.Proof of Work provides the needed security and has been proven to work pretty well so far. However, it is very energy consuming:
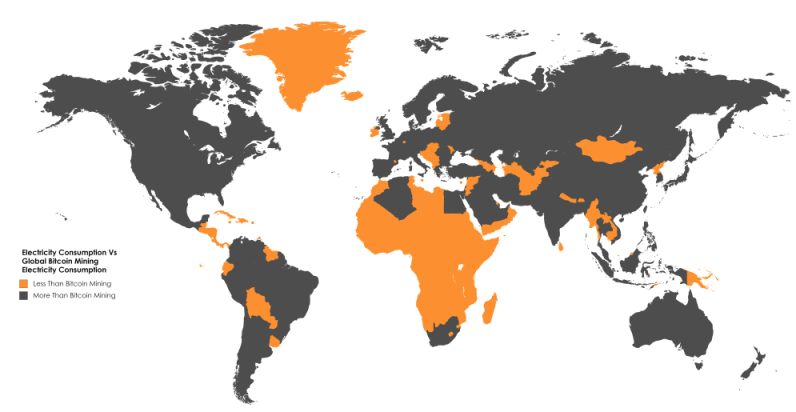
Almost all African countries (separately) consume less electricity than the Bitcoin Mining industry

The main issue with PoS is the so-called nothing-at-stake problem. Essentially, in the case of a fork, stakers are not disincentivized from staking in both chains, and the danger of double spending problems increase. More on that here.In order to avoid that, hybrids consensus algorithms appeared, such as the PoW-PoS combination used by Decred. Active research towards a secure and decentralized Proof of Stake protocol is being done by the Ethereum Foundation with Casper The Friendly Ghost and Casper The Friendly Finality Gadget.
原文: https://blog.cosmos.network/the-internet-of-blockchains-how-cosmos-does-interoperability-starting-with-the-ethereum-peg-zone-8744d4d2bc3f

Running time of solving the Byzantine Generals Problem with the algorithm proposed by Lamport, Shostak and Pease (n = number of actors, m = number of traitors)That leads us to a classic question in Computer Science:Can we do better?The topic of the present article will discuss alternative algorithms which achieve Byzantine Fault Tolerance.Note: Please bear with any simplifications that I make. These algorithms have a lot of complex research behind them. I will be providing links as we proceed for the interested reader to do their own further research.Blockchains use consensus algorithms to elect a leader who will decide the contents of the next block.That leader is also responsible for broadcasting the block to the network, so that the other peers can verify the validity of its contents.
Proof of Work (PoW)
This is the most popular algorithm being used by currencies such as Bitcoin and Ethereum, each one with its own differences.Before continuing, for the non-technical readers:A hash function is any function that can be used to map data of arbitrary size to data of fixed size¹.If a hash function is secure, its output is indistinguishable from random.Example:
keccak256("hello") = 1c8aff950685c2ed4bc3174f3472287b56d9517b9c948127319a09a7a36deac8
keccak256("hello1") = 57c65f1718e8297f4048beff2419e134656b7a856872b27ad77846e395f13ffeIn Proof of Work, in order for an actor to be elected as a leader and choose the next block to be added to the blockchain they have to find a solution to a particular mathematical problem.Let that mathematical problem be:Given data X, find a number n such as that the hash of n appended to X results is a number less than Y.Example - hash is a hypothetical hash function that has the outputs listed as below Y = 10, X = 'test'
hash(X) = hash('test') = 0x0f = 15 > 10
hash(X+1) = hash('test1') = 0xff = 255 > 10
hash(X+2) = hash('test2') = 0x09 = 9 < 10 OK, Solved.Given that the hash function used is cryptographically secure [1,2], the only way to find a solution to that problem is by bruteforce (trying all possible combinations). In other words, probabilistically speaking, the actor who will solve the aforementioned problem first the majority of the time is the one who has access to the most computing power. These actors are also called miners.It has been widely successful primarily due to its following properties:It is hard to find a solution for that given problemWhen given a solution to that problem it is easy to verify that it is correct
Whenever a new block is mined, that miner gets rewarded with some currency (block reward, transaction fees) and thus are incentivized to keep mining. In Proof of Work, other nodes verify the validity of the block by checking that the hash of the data of the block is less than a preset number.Due to the limited supply of computational power, miners are also incentivized not to cheat. Attacking the network would cost a lot because of the high cost of hardware, energy, and potential mining profits missed.The picture illustrates very well how Bitcoin, and any other coin that uses Proof of Work, discourages malicious behavior.

For the readers who are interested in how chain-splits (a.k.a. forks or chain reorganizations work in the case of a disagreement, I suggest this article.Proof of Work provides the needed security and has been proven to work pretty well so far. However, it is very energy consuming:

Almost all African countries (separately) consume less electricity than the Bitcoin Mining industry
Proof of Stake (PoS)
Before continuing, let me make the analogy of the leader election (the actor who will select the next block) as a lottery:In a lottery, probabilistically, if Bob has more tickets than Alice, he is more likely to win.In a very similar manner:In Proof of Work, if Bob has more computational power and energy than Alice — and thus can output more work — he is more likely to win (mine the next block).Similarly, yet again:In Proof of Stake, if Bob has more stake than Alice, he is more likely to win (“mine” the next block).Proof of Stake takes away the energy and computational power requirement of PoW and replaces it with stake. Stake is referred to as an amount of currency that an actor is willing to lock up for a certain amount of time. In return, they get a chance proportional to their stake to be the next leader and select the next block. There are various existing coins which use pure PoS, such as Nxt and Blackcoin.
The main issue with PoS is the so-called nothing-at-stake problem. Essentially, in the case of a fork, stakers are not disincentivized from staking in both chains, and the danger of double spending problems increase. More on that here.In order to avoid that, hybrids consensus algorithms appeared, such as the PoW-PoS combination used by Decred. Active research towards a secure and decentralized Proof of Stake protocol is being done by the Ethereum Foundation with Casper The Friendly Ghost and Casper The Friendly Finality Gadget.
Conclusion
In this article, we discussed Proof of Work & Proof of Stake, which are currently the consensus algorithms that achieve Byzantine Fault Tolerance and are practically used in today’s blockchain systems.Other consensus algorithms such as Practical Byzantine Fault Tolerance (Tendermint) or Distributed Byzantine Fault Tolerance (NEO) exist. A great comparison between PBFT and Casper can be found here.原文: https://blog.cosmos.network/the-internet-of-blockchains-how-cosmos-does-interoperability-starting-with-the-ethereum-peg-zone-8744d4d2bc3f
相关文章推荐
- How to Build Your Own Blockchain Part 4.1 — Bitcoin Proof of Work Difficulty Explained
- How to Build Your Own Blockchain Part 4.2 — Ethereum Proof of Work Difficulty Explained
- Understanding Blockchain Fundamentals, Part 1: Byzantine Fault Tolerance
- SmartClient Software factory中的Composite UI Application Block(Cab)技术了解(二):WorkItem&SmartPart
- Proof of work - 工作量证明
- 2016_S&P_Hawk:The Blockchain Model of Cryptography and Privacy-Preserving Smart Contracts
- javax.management.MalformedObjectNameException: Invalid character '' in value part of property ,Oracle 驱动包的错误
- 《大话设计模式》--加薪非要老总批--职责链模式<Chain Of Responsibility>(24)
- Photoshop Skill III: The second part of Sharpen's Tips 锐化的技巧之二
- C++ AMP: restrict(amp) restrictions part 2 of N – compound types
- web app & part of the design for a german corp
- (Boolan)C++设计模式 <十一> ——组合模式(Composite)、迭代器(Iterator)和责任链(Chain of Resposibility)
- 使用Parity建立Proof-of-Authority (PoA) Ethereum Chain5分钟快速从无到有建立Ethereum联盟链
- Understanding Platform Invocation Services(Chapter 1 of COM and .NET Interoperability) part1
- Documentaries & Blockchain Art & Explorers
- Creating Your First Blockchain with Java. Part 1.
- DirectoryNotFoundException: Could not find a part of the path "……"
- 对比特币以及Proof-Of_Work的理解
- Blockchain的鱼和熊掌系列(1)Performance Issues of the Blockchain
- Creating Your First Blockchain with Java. Part 2 — Transactions.
