DNS高级应用:子域授权、转发和view的实现方法
2017-05-09 22:11
651 查看
DNS高级应用:子域授权、转发和view的实现方法
在上面的功能实现之前我们先来复习一下DNS 一些配置的基本格式:ACL:acl string {
address_match_element;
address_match_element;
... };ZONE :
#主服务器
zone string optional_class {
type master ;
file quoted_string;
...
};
#从服务器
zone string optional_class {
type slave ;
masters { MASTER_ADDRESS; }
file quoted_string;
...
};
#转发服务器
zone string optional_class {
type forward ;
forward {first|only};
forwarders { forward_address; }
...
};VIEW
# 一旦启动view,所有的zone只能定义在view中。
view string optional_class {
match-clients { address_match_element; ... };
match-destinations { address_match_element; ... };
zone string optional_class {
...
};访问控制指令:
allow-query { address_match_element; ... };
allow-transfer { address_match_element; ... };
allow-recursion { address_match_element; ... };
allow-update { address_match_element; ... };详情man named.conf子域授权:
环境:两台centos6.5IP1:192.168.1.16 , IP2:192.168.1.20实现方式:将IP1配置成DNS服务器,在其下配置一个以IP2为域名的DNS服务器(子域)。只需在IP1的解析库文件里定义一个子域即可。START:关闭防火墙和selinux首先配置IP1(192.168.1.16):
修改配置文件
# cat /etc/named.conf
options {
listen-on port 53 { 192.168.1.16; 127.0.0.1; };//or delete this line
// listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
recursion yes;
dnssec-enable no;
dnssec-validation no;
/* Path to ISC DLV key */
// bindkeys-file "/etc/named.iscdlv.key";
// managed-keys-directory "/var/named/dynamic";
};添加zone:# tail /etc/named.rfc1912.zones
zone "jiajie.com" IN {
type master;
file "jiajie.zone";
};配置解析库文件:# vim /var/named/jiajie.zone $TTL 1D @ IN SOA ns1.jiajie.com. jjzgood.126.com. ( 20170509 1H 10M 5D 1D ) IN NS ns1 IN NS ns2 ns1 IN A 192.168.1.16 ns2 IN A 192.168.1.17 www IN A 192.168.1.17 * IN A 192.168.1.16 #在解析库里定义一个字域 ops IN NS ns1.ops ops IN NS ns2.ops ns1.ops IN A 192.168.1.20 ns2.ops IN A 192.168.1.21修改权限和组:
#chmod 640 /var/named/jiajie.zone # chown :named /var/named/jiajie.zone # ll /var/named/jiajie.zone -rw-r----- 1 root named 292 5月 9 16:30 /var/named/jiajie.zone重启服务:
# service named restart查看端口号:
# ss -tlnp|grep :53验证:
# host -t a www.jiajie.com 192.168.1.16 Using domain server: Name: 192.168.1.16 Address: 192.168.1.16#53 Aliases: www.jiajie.com has address 192.168.1.173.配置子域(IP2:192.168.1.20)修改配置文件:
# cat /etc/named.conf
options {
listen-on port 53 { 192.168.1.16; 127.0.0.1; };//or delete this line
// listen-on-v6 port 53 { ::1; };
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
memstatistics-file "/var/named/data/named_mem_stats.txt";
allow-query { any; };
recursion yes;
dnssec-enable no;
dnssec-validation no;
/* Path to ISC DLV key */
// bindkeys-file "/etc/named.iscdlv.key";
// managed-keys-directory "/var/named/dynamic";
};添加ZONE:# tail /etc/named.rfc1912.zones
zone "ops.jiajie.com" IN {
type master;
file "ops.jiajie.com.zone";
};配置解析库文件:# vim /var/named/ops.jiajie.com.zone $TTL 1D @ IN SOA ns1.ops.jiajie.com. jjzgood.126.com. ( 20170509 1H 10M 5D 1D ) IN NS ns1 IN NS ns2 ns1 IN A 192.168.1.20 ns2 IN A 192.168.1.21 www IN A 192.168.1.20 * IN A 192.168.1.21修改权限和组:
# chmod 640 /var/named/ops.jiajie.com.zone # chown named /var/named/ops.jiajie.com.zone重启服务:
# service named restart查看端口号:
# ss -tlnp|grep :53验证:
# host -t a www.ops.jiajie.com 192.168.1.20 Using domain server: Name: 192.168.1.20 Address: 192.168.1.20#53 Aliases: www.ops.jiajie.com has address 192.168.1.20 # host -t a ftp.ops.jiajie.com 192.168.1.20 Using domain server: Name: 192.168.1.20 Address: 192.168.1.20#53 Aliases: ftp.ops.jiajie.com has address 192.168.1.21 -------------------------------------------- #注意上下两个使用的dns服务器是不同的 --------------------------------------------- # host -t a www.ops.jiajie.com 192.168.1.16 Using domain server: Name: 192.168.1.16 Address: 192.168.1.16#53 Aliases: www.ops.jiajie.com has address 192.168.1.20 [root@test1 ~]# host -t a ftp.ops.jiajie.com 192.168.1.16 Using domain server: Name: 192.168.1.16 Address: 192.168.1.16#53 Aliases: ftp.ops.jiajie.com has address 192.168.1.21由上可以看出如果用父域来解析子域的地址是可以的,但是如果使用子域去解析父域的是解析不出来的(如下图)。此时我们可以在子域上设置一个转发服务器来解决上面的尴尬状况。如下图:
# host -t a ftp.jiajie.com 192.168.1.20 Using domain server: Name: 192.168.1.20 Address: 192.168.1.20#53 Aliases: Host ftp.jiajie.com not found: 3(NXDOMAIN)
转发服务器
注意:本实验是基于上面的实验进行的。首先在IP2(192.168.1.20)服务器上增加一个转发区域:# tail /etc/named.rfc1912.zones
zone "jiajie.com" IN {
type forward;
forward only;
forwarders { 192.168.1.16; };
};重新加载配置服务:# rndc reload此时我们就可以在子域上解析父域的地址了:
# host -t A ftp.jiajie.com 192.168.1.20 Using domain server: Name: 192.168.1.20 Address: 192.168.1.20#53 Aliases: ftp.jiajie.com has address 192.168.1.16转发分为全局转发和区域转发
全局转发:凡是非本机所负责的解析区域的,统统转发给指定服务器。
option {
forward {first|only};
forwarders { address; }
};区域转发:只转发对特定区域的请求到指定服务器
zone {
type forward;
forward {first|only};
forwarders { address; }
};智能view的实现:
本实验是在上面两个实验的基础上进行修改的。注意一旦启用view,所有的zone都能定义在view中一个bind可以定义多个view,每个view中可以定义一个或者多个zone。
多个view内可能需要对同一个区域进行解析,但使用不同的区域解析文件。
客户端请求到达时是自上而下检查view的。
配置:配置IP1(192.168.1.16)1.首先先把
/etc/named.conf中的根区域移到
/etc/named.rfc1912.zones文件中。
# vim /etc/named.conf
zone "." IN {
type hint;
file "named.ca";
};2.在/etc/named.conf文件首部添加一个acl
#vim /etc/named.conf
acl in_net {
192.168.1.16;
192.168.1.10;
127.0.0.0/24;
};3.添加两个view,注意第一个view将文件中的zone都圈起来,第二个view添加在文件的底部。#将匹配acl内的IP
# vim /etc/named.rfc1912.zones
view innet {
match-clients { in_net; };
allow-recursion { in_net; };
zone ...
...
};
};
#匹配acl以外的IP
view outnet {
match-clients { any; };
zone "jiajie.com" IN {
type master;
file "jiajie.com.out";
allow-update { none; };
};
};4.cp /var/named/jiajie.zone /var/named/jiajie.com.out -a5.编辑
/var/named/jiajie.zone.out
# vim /var/named/jiajie.com.out $TTL 1D @ IN SOA ns1.jiajie.com. jjzgood.126.com. ( 20170509 1H 10M 5D 1D ) IN NS ns1 IN NS ns2 ns1 IN A 192.168.1.16 ns2 IN A 192.168.1.17 www IN A 2.2.2.2 * IN A 2.2.2.36.运行
# rndc reload7.验证:
#基于IP1(192.168.1.16)平台验证 # host www.jiajie.com 192.168.1.16 Using domain server: Name: 192.168.1.16 Address: 192.168.1.16#53 Aliases: www.jiajie.com has address 192.168.1.17 #基于IP2(192.168.1.20)平台验证 # host www.jiajie.com 192.168.1.16 Using domain server: Name: 192.168.1.16 Address: 192.168.1.16#53 Aliases: www.jiajie.com has address 2.2.2.2windows平台验证:
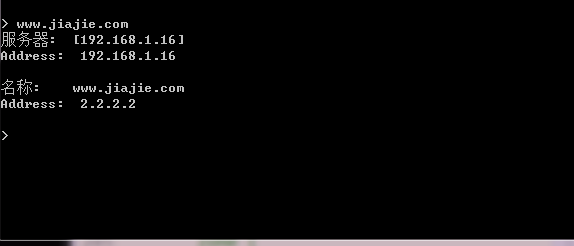
由上面可以看出你虽然是访问同一个域名,但是如果你的IP地址不同,将会返回给你不同的地址,这样就实现了智能化。2017/5/9 22:04:59
相关文章推荐
- DNS服务器系列之二:高级配置之-DNS子域授权、区域转发、acl列表及view 推荐
- Linux之DNS正向反向解析以及主从复制、子域授权、转发和view功能
- Linux DNS服务系列之主从复制、子域授权和转发、view配置详解
- DNS--bind 实现主从复制、子域授权、反向区域及区域转发
- DNS的子域授权、转发以及view
- DNS高级配置原理及配置、子域授权、view智能解析(二)
- bind实现DNS子域授权及转发2/3
- DNS:正反向解析,主从配置,子域授权,转发机制,view
- Linux DNS服务系列之主从复制、子域授权和转发、view配置详解
- linux下DNS主从复制,view视图,转发,子域授权
- DNS的子域授权和转发机制,view设置
- DNS高级配置原理及配置、子域授权、view智能解析(二)
- DNS子域授权及视图view功能的应用
- 使用bind自建DNS服务,实现双DNS服务器主从复制、子域授权、转发、智能解析等效果
- CenOS6服务管理之DNS-子域授权和区域转发及DNS视图功能实现
- RHEL6.3 DNS高级技术三 通过rsync实现DNS View访问列表文件同步
- BIND之子域授权、区域转发、view
- DNS部署(2)----------子域授权与子域转发
- BIND 子域授权的实现和区域转发实现
- 实现DNS子域授权和分离解析
