Nginx配置防盗链、Nginx访问控制、Nginx解析php相关配置
2018-01-04 17:46
1136 查看
Nginx配置防盗链
#vim /usr/local/nginx/conf/vhost/test.com.conf //写入如下内容
location ~* ^.+\.(gif|jpg|png|swf|flv|rar|zip|doc|pdf|gz|bz2|jpeg|bmp|xls)$
{
expires 7d;
valid_referers none blocked server_names *.test.com ; //定义referer白名单
if ($invalid_referer) {
return 403;
}
access_log off;
}# /usr/local/nginx/sbin/nginx -t //检测语法
#/usr/local/nginx/sbin/nginx -s reload //重新加载
#echo "1223" > /data/wwwroot/test.com/1.gif //将1223写入1.gif中
#curl -x127.0.0.1:80 -I test.com/1.gif //测试防盗链
HTTP/1.1 200 OK Server: nginx/1.12.1 Date: Thu, 04 Jan 2018 09:11:57 GMT Content-Type: image/gif Content-Length: 11 Last-Modified: Thu, 04 Jan 2018 09:08:11 GMT Connection: keep-alive ETag: "5a4deefb-b" Expires: Thu, 11 Jan 2018 09:11:57 GMT Cache-Control: max-age=604800 Accept-Ranges: bytes
# curl -e "http://www.baidu.com/1.txt" -x127.0.0.1:80 -I test.com/1.gif
HTTP/1.1 403 Forbidden Server: nginx/1.12.1 Date: Wed, 03 Jan 2018 04:19:13 GMT Content-Type: text/html Content-Length: 169 Connection: keep-alive
# curl -e "http://www.test.com/1.txt" -x127.0.0.1:80 -I test.com/1.gif
HTTP/1.1 200 OK Server: nginx/1.12.1 Date: Wed, 03 Jan 2018 04:19:32 GMT Content-Type: image/gif Content-Length: 11 Last-Modified: Wed, 03 Jan 2018 04:06:01 GMT Connection: keep-alive ETag: "5a4c56a9-b" Expires: Wed, 10 Jan 2018 04:19:32 GMT Cache-Control: max-age=604800 Accept-Ranges: bytes
说明防盗链配置成功了
Nginx访问控制
需求:访问/admin/目录的请求,只允许某几个IP访问,配置如下:
#vim /usr/local/nginx/conf/vhost/test.com.conf //写入如下内容
location /admin/
{
allow 192.168.37.1;
allow 127.0.0.1;
deny all;
}#mkdir /data/wwwroot/test.com/admin/ //创建目录
#echo “test,test”>/data/wwwroot/test.com/admin/1.html //写入测试语句
#/usr/local/nginx/sbin/nginx -t && -s reload //检测配置文件和重新加载
#curl -x127.0.0.1:80 test.com/admin/1.html -I //测试
HTTP/1.1 200 OK Server: nginx/1.12.1 Date: Wed, 03 Jan 2018 05:05:58 GMT Content-Type: text/html Content-Length: 6 Last-Modified: Wed, 03 Jan 2018 05:05:20 GMT Connection: keep-alive ETag: "5a4c6490-6" Accept-Ranges: bytes
#curl -x192.168.37.130:80 test.com/admin/1.html -I //测试能否访问
HTTP/1.1 403 Forbidden Server: nginx/1.12.1 Date: Wed, 03 Jan 2018 05:06:22 GMT Content-Type: text/html Content-Length: 169 Connection: keep-alive
将能上传的目录禁止解析php,防止发生别人根据目录能解析php代码上传木马文件
配置如下:
location ~ .*(upload|image)/.*\.php$
{
deny all;
}#/usr/local/nginx/sbin/nginx -t && -s reload //检测配置文件和重新加载
#mkdir /data/wwwroot/test.com/upload/ //创建upload目录
#echo "123" > /data/wwwroot/test.com/upload/1.php //编辑1.php文件
#curl -x127.0.0.1:80 test.com/upload/1.php -I //测试
HTTP/1.1 403 Forbidden Server: nginx/1.12.1 Date: Wed, 03 Jan 2018 05:27:09 GMT Content-Type: text/html Content-Length: 169 Connection: keep-alive
# curl -x127.0.0.1:80 test.com/upload/1.txt -I
HTTP/1.1 200 OK Server: nginx/1.12.1 Date: Wed, 03 Jan 2018 05:32:18 GMT Content-Type: text/plain Content-Length: 4 Last-Modified: Wed, 03 Jan 2018 05:32:11 GMT Connection: keep-alive ETag: "5a4c6adb-4" Accept-Ranges: bytes
根据user_agent限制
if ($http_user_agent ~ 'Spider/3.0|YoudaoBot|Tomato')
{
return 403;
}#/usr/local/nginx/sbin/nginx -t && -s reload //检测配置文件和重新加载
#curl -A "Tomatoshshd" -x127.0.0.1:80 test.com/upload/1.txt -I //加上user_agent来进行测试
HTTP/1.1 403 Forbidden Server: nginx/1.12.1 Date: Wed, 03 Jan 2018 05:49:14 GMT Content-Type: text/html Content-Length: 169 Connection: keep-alive
查案日志就可以看到信息
127.0.0.1 - [03/Jan/2018:13:49:14 +0800] test.com "/upload/1.txt" 403 "-" "Tomatoshsh"
Nginx解析php相关配置
nginx没有做配置来解析php,当解析php的代码时,会直接将代码显示出来
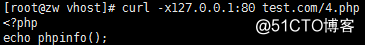
此时更改配置文件
#vim /usr/local/nginx/conf/vhost/test.com.conf //写入配置文件
配置如下:
location ~ \.php$
{
include fastcgi_params;
fastcgi_pass unix:/tmp/php-fcgi.sock; //监听地址写错会出现502
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME /data/wwwroot/test.com$fastcgi_script_name;
}然后再来访问刚刚的php文件 #curl -x127.0.0.1:80 test.com/4.php //此时能正常解析
#fastcgi_pass 用来指定php-fpm监听的地址或者socket,在/usr/local/php-fpm/etc/php-fpm.conf中的配置文件的监听地址和nginx的虚拟主机配置文件监听地址必须是一样的,否则会出现502问题
location ~ \.php$
{
include fastcgi_params;
# fastcgi_pass unix:/tmp/php-fcgi.sock;
fastcgi_pass 127.0.0.1:9000; //此处要和php-fpm配置文件里的监听地址一样
fastcgi_index index.php;
fastcgi_param SCRIPT_FILENAME /data/wwwroot/test.com$fastcgi_script_name;
}/usr/local/php-fpm/etc/php-fpm.conf中的监听权限,当php-fpm的配置文件中的监听权限不定义时,会出现502的问题
#vim /usr/local/php-fpm/etc/php-fpm.conf //编辑php-fpm服务的配置文件内容 [global] //定义全局参数 pid = /usr/local/php-fpm/var/run/php-fpm.pid //定义它的pid error_log = /usr/local/php-fpm/var/log/php-fpm.log [www] //模块名 listen = /tmp/php-fcgi.sock //监听 #listen = 127.0.0.1:9000 //监听本机ip和端口 listen.mode = 666 //监听权限,监听socket时不定义会出现502 user = php-fpm group = php-fpm pm = dynamic pm.max_children = 50 pm.start_servers = 20 pm.min_spare_servers = 5 pm.max_spare_servers = 35 pm.max_requests = 500 rlimit_files = 1024
当php的资源耗尽时也会出现访问502的问题
相关文章推荐
- Nginx防盗链、访问控制、Nginx解析PHP相关配置、Nginx代理
- 【LNMP】Nginx防盗链、Nginx访问控制、Nginx解析php相关配置和Nginx代理
- LNMP架构 (4) 之 Nginx的防盗链、访问控制、解析php相关配置
- linux的Nginx防盗链、Nginx访问控制、Nginx解析php相关配置、Nginx代理介绍
- 12.13 Nginx防盗链 12.14 Nginx访问控制 12.15 Nginx解析php相关配置 12.16 Nginx代理
- linux学习第四十六篇:Nginx防盗链,Nginx访问控制,Nginx解析php相关配置,Nginx代理
- 十二周四次课 2018.01.05 Nginx防盗链、Nginx访问控制、Nginx解析php相关配置、Nginx代理
- LNMP(nginx防盗链,访问控制,解析php相关配置,Nginx代理,常见502问题)
- Nginx防盗链,Nginx访问控制,,Nginx解析php相关配置,Nginx代理
- 详解Nginx防盗链和Nginx访问控制与Nginx解析php的配置
- Nginx防盗链、Nginx访问控制、Nginx解析php相关配置
- Nginx防盗链、Nginx访问控制、Nginx解析php的配置
- Nginx防盗链,Nginx访问控制, Nginx解析php相关配置, Nginx代理
- Nginx防盗链、Nginx访问控制、Nginx解析php相关配置、Nginx代理
- Nginx防盗链、Nginx访问控制、Nginx解析php相关配置、Nginx代理
- Nginx防盗链 Nginx访问控制 Nginx解析php相关配置 Nginx代理
- Nginx防盗链、访问监控、解析php相关配置,Nginx代理
- Nginx防盗链,Nginx访问控制,Nginx解析PHP的相关配置,Nginx代理
- nginx防盗链+访问控制+限制指定目录运行php+解析支持php+现在user_agent
