ccnp大型企业综合案例分析2
2017-08-24 15:01
369 查看
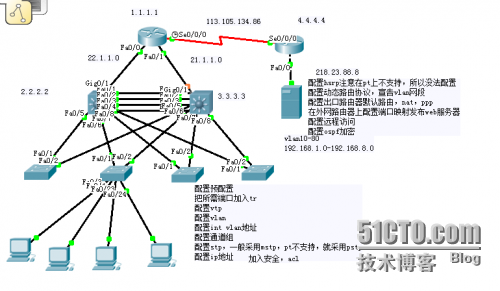
4)配置ospf协议Conf trouter ospf 1 router-id 2.2.2.2 log-adjacency-changes network 22.1.1.2 0.0.0.0 area 0 network 2.2.2.2 0.0.0.0 area 0 network 192.168.1.2 0.0.0.0 area 0 network 192.168.2.2 0.0.0.0 area 0 network 192.168.3.2 0.0.0.0 area 0 network 192.168.4.2 0.0.0.0 area 0 network 192.168.5.2 0.0.0.0 area 0 network 192.168.6.2 0.0.0.0 area 0 network 192.168.7.2 0.0.0.0 area 0 network 192.168.8.2 0.0.0.0 area 0 Iou2//把所需使用vtp协议的端口线路更改为trunk模式enconf tint rang f0/1-8sw tr en d //在pt中不需要,真实环境和iou中都要加sw mo tr//创建vtp并把这台交换机设为server模式 conf tvtp dom ccievtp mod servervtp pruning // //在pt中不支持这命令,真实环境和iou中都支持这样节省带宽开销End//创建管理地址,方便管理员管理conf tint vlan 100ip add 192.168.9.2 255.255.255.0no shutEnd//设置vtp版本密码(为了安全起见)conf tvtp pass lu@123vtp ver 2End//创建二层组,使用以太网端口聚合技术,实现高速负载分流conf tint rang f0/1-4Channel-protocol lacpchannel-g 1 mode activeend//Mst 是pvst 的升级版,通过不同实例给vlan 做冗余备分。创建了两个实例1 2,分别将vlan10-80加入到对应实例,并设置主从,实现不同实例的冗余备份 conf tspanning-tree mode mst //在pt中不支持mst,只能用rstp来实现了,现实生活和iou上都支持spanning-tree mst configuinstance 1 vlan 10,20,30,40revision 1instance 2 vlan 50,60,70,80revision 1exitspanning-tree mst 1 root primaryspanning-tree mst 2 root secondaryEnd EnConf tSpanning-tree mode rapspanning-tree vlan 50,60,70,80 root primaryspanning-tree vlan 10,20,30,40 root secondayEnd //为不同vlan划分网关,实现不同vlan基于三层交换机的路由互通conf tint vlan 10ip add 192.168.1.3 255.255.255.0no shutint vlan 20ip add 192.168.2.3 255.255.255.0no shutint vlan 30ip add 192.168.3.3 255.255.255.0no shutint vlan 40ip add 192.168.4.3 255.255.255.0no shutint vlan 50ip add 192.168.5.3 255.255.255.0no shutint vlan 60ip add 192.168.6.3 255.255.255.0no shutint vlan 70ip add 192.168.7.3 255.255.255.0no shutint vlan 80ip add 192.168.8.3 255.255.255.0no shutEnd//配置hsrp实现网关高可用性,sw1是vlan10,20,30,40-的主网关,是50,60,70,80 的备用网关。Sw2是vlan50,60,70,80的主网关,是10,20,30,40 的备网关。注意State is Active 为主网关State is Standby 为备网关conf tint vlan 10standby 10 ip 192.168.1.1standby 10 priority 105standby 10 preemptstandby 10 track g0/1endconf tint vlan 20standby 20 ip 192.168.2.1standby 20 priority 105standby 20 preemptstandby 20 track g0/1endconf tint vlan 30standby 30 ip 192.168.3.1standby 30 priority 105standby 30 preemptstandby 30 track g0/1endconf tint vlan 40standby 40 ip 192.168.4.1standby 40 priority 105standby 40 preemptstandby 40 track g0/1endconf tint vlan 50standby 50 ip 192.168.5.1standby 50 priority 100standby 50 preemptstandby 50 track g0/1endconf tint vlan 60standby 60 ip 192.168.6.1standby 60 priority 100standby 60 preemptstandby 60 track g0/1endconf tint vlan 70standby 70 ip 192.168.7.1standby 70 priority 100standby 70 preemptstandby 70 track g0/1endconf tint vlan 80standby 80 ip 192.168.8.1standby 80 priority 100standby 80 preemptstandby 80 track g0/1endwrite 5)配置dhcpip dhcp excluded-address 192.168.1.1ip dhcp excluded-address 192.168.1.2ip dhcp excluded-address 192.168.1.3 ip dhcp pool vlan10 network 192.168.1.0 255.255.255.0 default-router 192.168.1.1 dns-server 202.96.128.86Exit ip dhcp excluded-address 192.168.2.1ip dhcp excluded-address 192.168.2.2ip dhcp excluded-address 192.168.2.3 ip dhcp pool vlan20 network 192.168.2.0 255.255.255.0 default-router 192.168.2.1 dns-server 202.96.128.86exitip dhcp excluded-address 192.168.3.1ip dhcp excluded-address 192.168.3.2ip dhcp excluded-address 192.168.3.3ip dhcp pool vlan30 network 192.168.3.0 255.255.255.0 default-router 192.168.3.1 dns-server 202.96.128.86exitip dhcp excluded-address 192.168.4.1ip dhcp excluded-address 192.168.4.2ip dhcp excluded-address 192.168.4.3 ip dhcp pool vlan40 network 192.168.4.0 255.255.255.0 default-router 192.168.4.1 dns-server 202.96.128.86exitip dhcp excluded-address 192.168.5.1ip dhcp excluded-address 192.168.5.2ip dhcp excluded-address 192.168.5.3 ip dhcp pool vlan50 network 192.168.5.0 255.255.255.0 default-router 192.168.5.1 dns-server 202.96.128.86exitip dhcp excluded-address 192.168.6.1ip dhcp excluded-address 192.168.6.2ip dhcp excluded-address 192.168.6.3 ip dhcp pool vlan60 network 192.168.6.0 255.255.255.0 default-router 192.168.6.1 dns-server 202.96.128.86 ip dhcp excluded-address 192.168.7.1ip dhcp excluded-address 192.168.7.2ip dhcp excluded-address 192.168.7.3 ip dhcp pool vlan70 network 192.168.7.0 255.255.255.0 default-router 192.168.7.1 dns-server 202.96.128.86exitip dhcp excluded-address 192.168.8.1ip dhcp excluded-address 192.168.8.2ip dhcp excluded-address 192.168.8.3 ip dhcp pool vlan80 network 192.168.8.0 255.255.255.0 default-router 192.168.8.1 dns-server 202.96.128.86end
6)配置ospf协议Conf trouter ospf 1 router-id 2.2.2.2 log-adjacency-changes network 22.1.1.2 0.0.0.0 area 0 network 2.2.2.2 0.0.0.0 area 0 network 192.168.1.3 0.0.0.0 area 0 network 192.168.2.3 0.0.0.0 area 0 network 192.168.3.3 0.0.0.0 area 0 network 192.168.4.3 0.0.0.0 area 0 network 192.168.5.3 0.0.0.0 area 0 network 192.168.6.3 0.0.0.0 area 0 network 192.168.7.3 0.0.0.0 area 0 network 192.168.8.3 0.0.0.0 area 0 Iou3conf tint rang f0/1-2sw tr en dsw mo trendconf tvtp dom ccievtp mod cvtp pruningendconf tint vlan 100ip add 192.168.9.3 255.255.255.0no shutendconf tvtp pass lu@123vtp ver 2endwrite Iou4conf tint rang f0/1-2sw tr en dsw mo trendconf tvtp dom ccievtp mod cvtp pruningendconf tint vlan 100ip add 192.168.9.4 255.255.255.0no shutendconf tvtp pass lu@123vtp ver 2endwrite Iou5conf tint rang f0/1-2sw tr en dsw mo trendconf tvtp dom ccievtp mod cvtp pruningendconf tint vlan 100ip add 192.168.9.5 255.255.255.0no shutendconf tvtp pass lu@123vtp ver 2endwrite Iou6conf tint rang f0/1-2sw tr en dsw mo trendconf tvtp dom ccievtp mod cvtp pruningendconf tint vlan 100ip add 192.168.9.6 255.255.255.0no shutendconf tvtp pass lu@123vtp ver 2endwrite
7)出口配置动态路由协议让全网互通,配置nat让公司内部可以上网RIEnConf tinterface Loopback0 ip address 1.1.1.1 255.255.255.255No shutinterface FastEthernet0/1 ip address 21.1.1.1 255.255.255.0duplex full speed autoNo shutinterface FastEthernet0/0 ip address 22.1.1.1 255.255.255.0 duplex full speed autoNo shutinterface Serial0/0/0 ip address 113.105.134.85 255.255.255.0 clock rate 64000No shutEndConf trouter ospf 1 router-id 1.1.1.1 network 21.1.1.1 0.0.0.0 area 0 network 22.1.1.1 0.0.0.0 area 0 network 113.105.134.85 0.0.0.0 area 0 network 1.1.1.1 0.0.0.0 area 0 default-information originateEndConf tip route 0.0.0.0 0.0.0.0 Serial0/0/0 配置natEndConf tEnConf tInt f0/0Ip nat insideInt f0/1Ip nat insideInt s0/0/0Ip nat outsideExitAccess-list 1 permit 192.168.1.0 0.0.0.255Access-list 1 permit 192.168.2.0 0.0.0.255Access-list 1 permit 192.168.3.0 0.0.0.255Access-list 1 permit 192.168.4.0 0.0.0.255Access-list 1 permit 192.168.5.0 0.0.0.255Access-list 1 permit 192.168.6.0 0.0.0.255Access-list 1 permit 192.168.7.0 0.0.0.255Access-list 1 permit 192.168.8.0 0.0.0.255Ip nat inside source list 1 int s0/0/0 overloadEndwrite 8)在出口路由器和分公司路由器上走ppp协议实现全网互通R1配置EnConf tUsername r2 password ciscoInt s0/0/0Encapsulation pppPpp authentication chapendwriteR2配置EnConf tUsername r1 password ciscoInt s0/0/0Encapsulation pppPpp authentication chapEndConf tinterface Loopback0 ip address 4.4.4.4 255.255.255.255No shutinterface Serial0/0/0Clock rate 64000 ip address 113.105.134.86 255.255.255.0No shutinterface FastEthernet0/0 ip address 218.23.88.1 255.255.255.0 duplex auto speed autoNo shutWrite
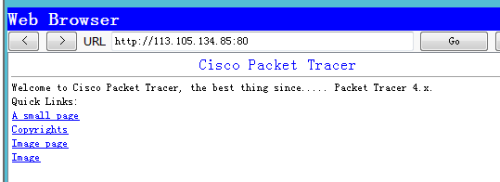
9)将公司内部接入层交换机端口加入到对应的vlan,把电脑连接上交换机,整个项目完成!实例:将iou3当做人事办公室,配置如下Iou3上EnConf tInt rang f0/3-24Sw mo accSw acc vlan 10EndWrite 10)发布web服务器出去让外网用户能够访问到公司利用web服务器发布的消息在出口路由器上配置EnConf tIp nat inside source static tcp 192.168.2.5 80 113.105.134.85 80Access-list 1 permit 192.168.2.0 0.0.0.255EndWrite验证结果如下:
11)配置acl8.0网段的用户只能访问公司ftp服务器,各vlan部分之间不能互访,但是网管1点段可以访问任意内外网方便管理,公司ftp是可以让任何人都访问到使用,web服务器除了8.0的用户其他用户都可以访问得到,公司除了8.0网段的用户,其他用户都可以访问web服务器和ftp服务器以及外网,只是不能访问到其他内部部门网段而已。备注:真实环境和iou都是两边路由器配置一模一样,在pt中因为没有做hsrp,所以在调用acl时候,sw1分别只调用int vlan30 -40 而在sw2上只调用50-80access-list 100 deny ip 192.168.8.0 0.0.0.255 192.168.2.5 0.0.0.0access-list 100 permit ip any anyInt vlan 80ip access-group 100 in sw1(config)#access-list 101 deny ip 192.168.3.0 0.0.0.255 192.168.4.0 0.0.0.255sw1(config)#access-list 101 deny ip 192.168.3.0 0.0.0.255 192.168.5.0 0.0.0.255sw1(config)#access-list 101 deny ip 192.168.3.0 0.0.0.255 192.168.6.0 0.0.0.255sw1(config)#access-list 101 deny ip 192.168.3.0 0.0.0.255 192.168.7.0 0.0.0.255sw1(config)#access-list 101 deny ip 192.168.3.0 0.0.0.255 192.168.8.0 0.0.0.255sw1(config)#access-list 101 permit ip any any sw1(config)#access-list 102 deny ip 192.168.4.0 0.0.0.255 192.168.3.0 0.0.0.255sw1(config)#access-list 102 deny ip 192.168.4.0 0.0.0.255 192.168.5.0 0.0.0.255sw1(config)#access-list 102 deny ip 192.168.4.0 0.0.0.255 192.168.6.0 0.0.0.255sw1(config)#access-list 102 deny ip 192.168.4.0 0.0.0.255 192.168.7.0 0.0.0.255sw1(config)#access-list 102 deny ip 192.168.4.0 0.0.0.255 192.168.8.0 0.0.0.255sw1(config)#access-list 102 permit ip any any sw1(config)#access-list 103 deny ip 192.168.5.0 0.0.0.255 192.168.4.0 0.0.0.255sw1(config)#access-list 103 deny ip 192.168.5.0 0.0.0.255 192.168.3.0 0.0.0.255sw1(config)#access-list 103 deny ip 192.168.5.0 0.0.0.255 192.168.6.0 0.0.0.255sw1(config)#access-list 103 deny ip 192.168.5.0 0.0.0.255 192.168.7.0 0.0.0.255sw1(config)#access-list 103 deny ip 192.168.5.0 0.0.0.255 192.168.8.0 0.0.0.255sw1(config)#access-list 103 permit ip any any sw1(config)#access-list 104 deny ip 192.168.6.0 0.0.0.255 192.168.4.0 0.0.0.255sw1(config)#access-list 104 deny ip 192.168.6.0 0.0.0.255 192.168.5.0 0.0.0.255sw1(config)#access-list 104 deny ip 192.168.6.0 0.0.0.255 192.168.3.0 0.0.0.255sw1(config)#access-list 104 deny ip 192.168.6.0 0.0.0.255 192.168.7.0 0.0.0.255sw1(config)#access-list 104 deny ip 192.168.6.0 0.0.0.255 192.168.8.0 0.0.0.255sw1(config)#access-list 104 permit ip any any sw1(config)#access-list 103 deny ip 192.168.7.0 0.0.0.255 192.168.4.0 0.0.0.255sw1(config)#access-list 103 deny ip 192.168.7.0 0.0.0.255 192.168.3.0 0.0.0.255sw1(config)#access-list 103 deny ip 192.168.7.0 0.0.0.255 192.168.6.0 0.0.0.255sw1(config)#access-list 103 deny ip 192.168.7.0 0.0.0.255 192.168.5.0 0.0.0.255sw1(config)#access-list 103 deny ip 192.168.7.0 0.0.0.255 192.168.8.0 0.0.0.255sw1(config)#access-list 103 permit ip any any sw1(config)#access-list 104 deny ip 192.168.8.0 0.0.0.255 192.168.4.0 0.0.0.255sw1(config)#access-list 104 deny ip 192.168.8.0 0.0.0.255 192.168.5.0 0.0.0.255sw1(config)#access-list 104 deny ip 192.168.8.0 0.0.0.255 192.168.3.0 0.0.0.255sw1(config)#access-list 104 deny ip 192.168.8.0 0.0.0.255 192.168.7.0 0.0.0.255sw1(config)#access-list 104 deny ip 192.168.8.0 0.0.0.255 192.168.6.0 0.0.0.255sw1(config)#access-list 104 permit ip any any Int vlan 20到80之间分别调用acl命令如下;因为这里需要vlan10和所有人通讯,服务器是管理员在管理,并且所有人都可以访问它,所以并没有写入acl,实际上也是这样,当然你可以精确到哪个ip地址,写法完全一样ip access-group 101 inip access-group 102 inip access-group 103 inip access-group 104 in-----------------------end---------------------------------此致为止公司内部网络就完全配置完毕,接下来等同学们学完网络安全后再配置***部分,谢谢大家的耐心听课
相关文章推荐
- ccnp大型企业综合案例分析1
- BI案例:某通信企业综合报表和决策分析系统实施案例
- 读书笔记之 大型网站技术架构(核心原理与案例分析)
- DHCP DNS 综合案例分析
- 大型网站技术架构-核心原理与案例分析-阅读笔记02
- 大型网站技术架构-核心原理与案例分析-阅读笔记4
- office企业办公应用技巧与综合案例操作
- 2013下半年(11月)信息系统项目管理师考试题型分析(综合知识、案例分析、论文)
- 大型企业网络安全性分析
- 大型网站技术架构:核心原理与案例分析阅读笔记之三
- state框架分析,多态,接口,综合案例
- 学习笔记8:《大型网站技术架构 核心原理与案例分析》之 随需应变:网站的可扩展架构
- 企业核心网络设计分析――从EIGRP网络迁移到BGP核心网络实施案例
- 第104讲: Spark Streaming电商广告点击综合案例需求分析和技术架构
- 某大型互联网企业用户上网行为日志分析系统——云计算项目实战
- 大型企业网络安全性分析
- 大型企业网络系统传输负载测试及分析
- [读书笔记]:大型网站技术架构——核心原理与案例分析
