Linux安全1-用户密码被暴力破解
2017-05-16 16:56
716 查看
本人所用Linux为CentOS7,本文写于2017-05-16,请注意版本区别和时效性。
但是事情不能就这么过了,得刨根问底。
/var/log/boot.log:记录了系统在开机引导过程中(开机自检过程显示在屏幕上)发生的事件
/var/log/lastlog:记录最后一次用户成功登陆的时间、登陆IP等信息
/var/log/messages:记录Linux操作系统常见的系统和服务错误信息
/var/log/secure:Linux系统安全日志,记录用户和工作组变化情况、用户登陆认证情况
/var/log/btmp:记录系统登陆失败的用户、时间以及远程IP地址
/var/log/syslog:只记录警告信息,常常是系统出问题的信息,使用lastlog查看
/var/log/wtmp:该日志文件永久记录每个用户登录、注销及系统的启动、停机的事件,使用last命令查看
/var/run/utmp:该日志文件记录有关当前登录的每个用户的信息。如 who、w、users、finger等就需要访问这个文件
/var/log/syslog或/var/log/messages 存储所有的全局系统活动数据,包括开机信息。基于 Debian 的系统如 Ubuntu 在 /var/log/syslog中存储,而基于RedHat的系统如RHEL或CentOS 则在/var/log/messages 中存储。
/var/log/auth.log或/var/log/secure 存储来自可插拔认证模块(PAM)的日志,包括成功的登录,失败的登录尝试和认证方式。Ubuntu 和 Debian 在/var/log/auth.log 中存储认证信息,而RHEL或CentOS 则在/var/log/secure 中存储。
我们需要的,就是/var/log/btmp(系统才安装了3天,这个日志文件已经40多兆了,汗),部分截图如下:
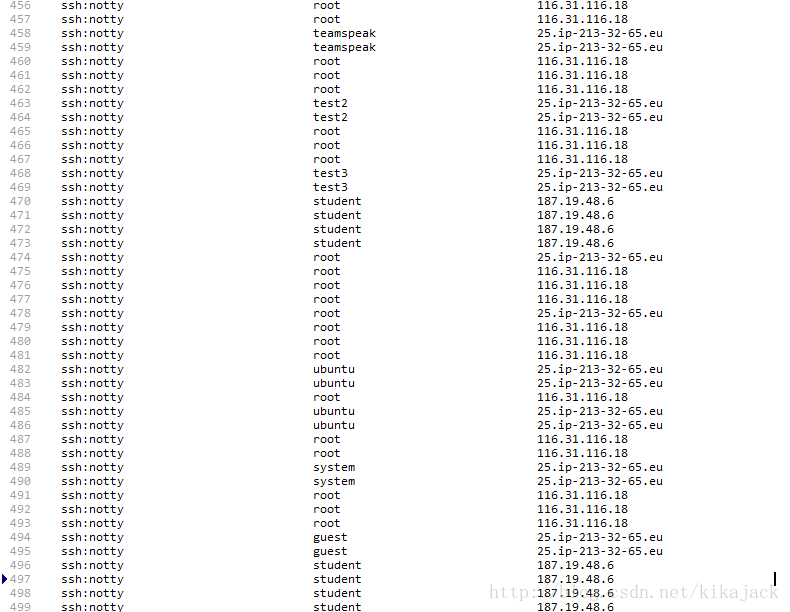
暴力破解的人,不停的尝试各种用户名+各种密码,看来是有一个字典库了。
数据:
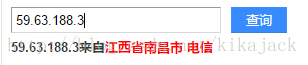
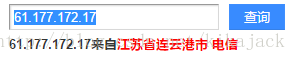
有几个IP攻击次数超多,查一下位置:
59.63.188.3 = 19359
61.177.172.17 = 18945
好吧,是中国的被控制的计算机。。。
有两个比较常用的软件,可以安装在服务器上:fail2ban(支持多种协议,登录失败N次后拉黑IP)和denyhosts(支持SSH,自动屏蔽非法IP连接)。两款软件的对比参考:https://serverfault.com/questions/128962/denyhosts-vs-fail2ban-vs-iptables-best-way-to-prevent-brute-force-logons。fail2ban更全面,那就安装fail2ban。wiki在此:https://en.wikipedia.org/wiki/Fail2ban。
http://www.cnblogs.com/jasmine-Jobs/p/5927968.html
在CentOS7中安装还是比较简单的,
测试服务可用性:
如果有响应:
测试暴力破解防护是否有效:用错误的密码来用SSH连接到服务器模拟一个暴力破解攻击
查看fail2ban日志:
哈哈,已经拉黑了3个IP。
每个IP在几次尝试后放弃,切换为其他IP(因为Linux有登录失败N次自动锁定当前用户的机制),所以这种防护效果有限,最好还是用证书登录。现实世界中一个IP代表一台主机,这么多机器,是怎么被人控制的呢?
http://www.freebuf.com/articles/system/113690.html
僵尸网络:黑客用一台台受控制的计算机(肉鸡)组成的网络。通过控制服务器(Command and Control Server,C&C,C2)可以操控每一个节点。数量巨大的节点同时访问指定服务器,即DDoS攻击(DDoS,Distributed Denial of Service)。
控制服务器是整个网络的核心,负责执行黑客的指令,控制肉鸡的行为。控制服务器与肉鸡之间通讯通常用IRC协议,这又是什么鬼?
so,控制服务器就是IRC服务器,每台肉鸡就是IRC客户端,登录的IRC服务器。黑客通过控制服务器向肉鸡下达指令。
每个肉鸡通常至少开两个线程:一个负责和IRC服务器通讯接受指令,另一个则通过端口扫描尝试感染其他机器。
常用的攻击方式是UDP攻击,它比TCP类型的攻击更难防,因为TCP是需要建立连接的,很容易被IDS/IPS设备RST,也很容易通过设置协议栈Syn Cookies屏蔽掉攻击包。——PS:这里暂时还不懂。。。
1.缘由
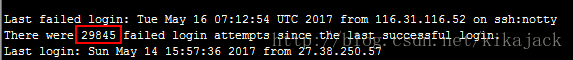
今天连接服务器时,发现有接近3万次的连接失败记录。抓紧查了查怎么回事,原来是被攻击了,可能是僵尸网络干的。大神们建议,root密码要保证足够复杂,如果用证书登录替换密码登录,更能保证安全。
但是事情不能就这么过了,得刨根问底。
2.查看Linux日志
1.首先要做的,先分析明白我们经历了什么。而这一切都在日志里。
Linux系统的日志,都保存在/var/log目录下:/var/log/boot.log:记录了系统在开机引导过程中(开机自检过程显示在屏幕上)发生的事件
/var/log/lastlog:记录最后一次用户成功登陆的时间、登陆IP等信息
/var/log/messages:记录Linux操作系统常见的系统和服务错误信息
/var/log/secure:Linux系统安全日志,记录用户和工作组变化情况、用户登陆认证情况
/var/log/btmp:记录系统登陆失败的用户、时间以及远程IP地址
/var/log/syslog:只记录警告信息,常常是系统出问题的信息,使用lastlog查看
/var/log/wtmp:该日志文件永久记录每个用户登录、注销及系统的启动、停机的事件,使用last命令查看
/var/run/utmp:该日志文件记录有关当前登录的每个用户的信息。如 who、w、users、finger等就需要访问这个文件
/var/log/syslog或/var/log/messages 存储所有的全局系统活动数据,包括开机信息。基于 Debian 的系统如 Ubuntu 在 /var/log/syslog中存储,而基于RedHat的系统如RHEL或CentOS 则在/var/log/messages 中存储。
/var/log/auth.log或/var/log/secure 存储来自可插拔认证模块(PAM)的日志,包括成功的登录,失败的登录尝试和认证方式。Ubuntu 和 Debian 在/var/log/auth.log 中存储认证信息,而RHEL或CentOS 则在/var/log/secure 中存储。
我们需要的,就是/var/log/btmp(系统才安装了3天,这个日志文件已经40多兆了,汗),部分截图如下:

暴力破解的人,不停的尝试各种用户名+各种密码,看来是有一个字典库了。
2.查看发起攻击的IP和攻击次数
Linux命令:cat /var/log/secure | awk '/Failed/{print $(NF-3)}' | sort | uniq -c | awk '{print $2" = "$1;}'数据:
101.200.1.126 = 3 101.95.184.150 = 3 103.207.36.69 = 1 103.207.39.37 = 5 103.207.39.38 = 9 106.57.36.158 = 6 106.75.35.108 = 12 109.163.234.4 = 2 109.163.234.9 = 2 111.73.1.31 = 6 112.101.170.251 = 6 112.126.89.5 = 11 113.122.41.161 = 6 113.123.34.205 = 6 113.195.145.21 = 2095 113.195.145.52 = 1109 113.69.26.141 = 6 114.141.132.53 = 6 115.209.234.171 = 6 116.252.34.161 = 6 116.31.116.11 = 2154 116.31.116.18 = 795 116.31.116.52 = 762 117.197.240.164 = 6 117.62.112.19 = 6 117.66.164.107 = 6 118.128.209.166 = 6 119.176.53.5 = 6 119.193.140.146 = 6 119.193.140.181 = 6 119.193.140.221 = 6 120.150.35.58 = 6 120.29.217.46 = 1 120.40.34.72 = 6 120.41.33.19 = 6 121.196.221.229 = 2 121.229.11.138 = 6 121.232.24.79 = 6 122.148.156.20 = 6 123.122.170.156 = 6 123.169.166.158 = 6 123.169.214.245 = 6 123.183.209.135 = 753 123.183.209.136 = 1487 123.56.132.58 = 11 123.57.4.140 = 13 123.59.182.186 = 6 123.96.174.180 = 6 124.131.155.214 = 6 125.227.128.173 = 6 139.162.122.110 = 1 139.219.232.36 = 9 139.219.235.146 = 13 139.219.235.98 = 5 155.4.230.97 = 6 158.69.220.200 = 12 162.247.72.7 = 1 163.172.136.101 = 1 163.172.67.180 = 1 163.21.78.25 = 6 166.70.207.2 = 1 168.83.7.251 = 3 171.25.193.131 = 1 176.10.104.240 = 1 176.10.104.243 = 2 177.93.167.109 = 6 178.217.187.39 = 2 179.40.238.233 = 6 179.63.253.13 = 6 180.102.200.218 = 6 181.20.189.125 = 6 181.211.159.53 = 6 181.211.180.64 = 6 181.211.199.223 = 6 181.21.12.211 = 2 181.22.28.254 = 6 181.26.150.10 = 36 181.26.182.140 = 6 181.26.191.51 = 6 181.26.48.16 = 6 181.64.95.109 = 6 182.243.78.23 = 6 182.44.33.54 = 6 182.70.182.28 = 6 182.92.67.157 = 8 183.146.233.37 = 6 183.93.223.119 = 6 183.93.252.190 = 6 183.95.168.180 = 6 185.165.29.57 = 1 185.188.205.2 = 14 185.29.8.132 = 1 185.31.161.102 = 1 185.8.82.133 = 1 186.121.240.62 = 9 186.130.168.36 = 24 186.130.57.186 = 6 186.133.191.187 = 6 186.178.172.137 = 6 186.24.37.180 = 9 187.45.8.221 = 6 188.16.106.158 = 6 188.19.104.117 = 6 190.13.15.48 = 6 190.141.173.171 = 1 190.174.157.194 = 6 190.174.33.175 = 6 190.214.14.230 = 9 190.214.195.186 = 6 190.225.94.63 = 6 190.238.246.220 = 6 190.42.34.248 = 6 191.232.191.58 = 18 191.80.65.143 = 6 192.36.27.4 = 1 192.36.27.6 = 4 192.36.27.7 = 1 193.107.3.242 = 6 193.107.85.62 = 2 193.70.89.20 = 1 193.90.12.88 = 1 195.154.251.25 = 3 197.231.221.211 = 1 201.178.35.152 = 24 201.179.13.161 = 6 201.230.25.236 = 6 202.194.81.24 = 341 207.244.70.35 = 2 209.126.108.73 = 65 209.222.77.220 = 4 210.94.133.146 = 6 212.237.20.206 = 13 212.251.54.10 = 1 213.32.65.25 = 35 216.218.222.12 = 2 218.244.128.200 = 145 222.101.189.85 = 6 222.186.134.179 = 4 222.220.98.76 = 6 222.73.37.31 = 6 223.3.39.9 = 6 27.155.99.168 = 3 27.38.250.57 = 3 31.207.47.36 = 69 37.122.73.220 = 6 37.204.10.173 = 6 40.71.203.189 = 61 42.159.145.29 = 12 43.255.191.37 = 9 45.76.191.120 = 8 46.148.26.108 = 1 46.166.139.71 = 2 46.183.221.231 = 2 49.228.64.111 = 6 49.77.229.186 = 12 51.15.40.233 = 1 51.37.30.50 = 6 5.196.1.129 = 2 54.172.31.75 = 28 54.209.44.102 = 3 59.63.188.3 = 19359 60.12.119.222 = 6 60.163.161.154 = 6 60.177.100.121 = 6 60.205.190.89 = 9 61.163.2.10 = 6 61.163.44.98 = 2 61.177.172.17 = 18945 65.19.167.130 = 2 65.19.167.132 = 2 74.208.158.11 = 2 77.109.139.87 = 1 77.170.230.163 = 2 77.247.181.165 = 1 77.81.225.199 = 21 78.109.23.1 = 2 78.56.143.236 = 6 79.129.105.92 = 5 79.165.246.184 = 6 8.26.21.62 = 79 83.0.246.106 = 30 85.244.194.63 = 6 85.248.227.163 = 2 87.106.16.173 = 12 87.118.122.51 = 1 87.253.24.58 = 6 89.114.125.31 = 6 89.234.157.254 = 3 89.248.166.157 = 1 89.254.229.100 = 6 91.197.232.103 = 69 92.222.69.25 = 2 93.197.75.211 = 6 93.56.12.164 = 9 94.177.175.71 = 1 94.236.193.244 = 2 94.51.138.168 = 6 95.68.183.161 = 6
有几个IP攻击次数超多,查一下位置:
59.63.188.3 = 19359
61.177.172.17 = 18945


好吧,是中国的被控制的计算机。。。
3.安装软件保护自己
如果你用证书登录,那啥都不用安装。密码登录的,还是安全第一。有两个比较常用的软件,可以安装在服务器上:fail2ban(支持多种协议,登录失败N次后拉黑IP)和denyhosts(支持SSH,自动屏蔽非法IP连接)。两款软件的对比参考:https://serverfault.com/questions/128962/denyhosts-vs-fail2ban-vs-iptables-best-way-to-prevent-brute-force-logons。fail2ban更全面,那就安装fail2ban。wiki在此:https://en.wikipedia.org/wiki/Fail2ban。
1.fail2ban安装配置教程:
https://linux.cn/article-5067-1.htmlhttp://www.cnblogs.com/jasmine-Jobs/p/5927968.html
在CentOS7中安装还是比较简单的,
yum install fail2ban即可。然后配置,把自己的规则放在/etc/fail2ban/jail.local 里以覆盖/etc/fail2ban/jail.conf 里的默认配置。配置摘要如下:
在针对服务的监狱区(在[DEFAULT]区后面的地方),你需要定义一个[ssh-iptables]区,这里用来定义SSH相关的监狱配置。真正的禁止IP地址的操作是通过iptables完成的。
[DEFAULT] # 以空格分隔的列表,可以是 IP 地址、CIDR 前缀或者 DNS 主机名 # 用于指定哪些地址可以忽略 fail2ban 防御 ignoreip = 127.0.0.1 172.31.0.0/24 10.10.0.0/24 192.168.0.0/24 # 客户端主机被禁止的时长(秒) bantime = 86400 # 客户端主机被禁止前允许失败的次数 maxretry = 5 # 查找失败次数的时长(秒) findtime = 600 mta = sendmail [ssh-iptables] enabled = true filter = sshd action = iptables[name=SSH, port=ssh, protocol=tcp] sendmail-whois[name=SSH, dest=your@email.com, sender=fail2ban@email.com] # Debian 系的发行版 logpath = /var/log/auth.log # Red Hat 系的发行版 logpath = /var/log/secure # ssh 服务的最大尝试次数 maxretry = 3
根据上述配置,fail2ban会自动禁止在最近10分钟内有超过3次访问尝试失败的任意IP地址。一旦被禁,这个IP地址将会在24小时内一直被禁止访问 SSH 服务。这个事件也会通过sendemail发送邮件通知。
2.重启fail2ban服务,测试是否可用
重启:systemctl restart fail2ban
测试服务可用性:
fail2ban-client ping
如果有响应:
Server replied: pong,表示成功。
测试暴力破解防护是否有效:用错误的密码来用SSH连接到服务器模拟一个暴力破解攻击
查看fail2ban日志:
tail -f /var/log/fail2ban.log
3.查看fail2ban当前活动的监狱列表:
fail2ban-client status
4.查看fail2ban指定监狱状态(例如ssh-iptables):
fail2ban-client status ssh-iptables
Status for the jail: ssh-iptables |- Filter | |- Currently failed: 1 | |- Total failed: 92 | `- File list: /var/log/secure `- Actions |- Currently banned: 3 |- Total banned: 3 `- Banned IP list: 116.31.116.52 113.195.145.52 192.99.210.174
哈哈,已经拉黑了3个IP。
5.设置 Fail2ban 自动启动
systemctl enable fail2ban
每个IP在几次尝试后放弃,切换为其他IP(因为Linux有登录失败N次自动锁定当前用户的机制),所以这种防护效果有限,最好还是用证书登录。现实世界中一个IP代表一台主机,这么多机器,是怎么被人控制的呢?
3.僵尸网络(Botnet,Robot network)
从FreeBuf上看到一篇文章,把我给科普了一下,链接如下:http://www.freebuf.com/articles/system/113690.html
僵尸网络:黑客用一台台受控制的计算机(肉鸡)组成的网络。通过控制服务器(Command and Control Server,C&C,C2)可以操控每一个节点。数量巨大的节点同时访问指定服务器,即DDoS攻击(DDoS,Distributed Denial of Service)。
控制服务器是整个网络的核心,负责执行黑客的指令,控制肉鸡的行为。控制服务器与肉鸡之间通讯通常用IRC协议,这又是什么鬼?
4.IRC协议
IRC(Internet Relay Chat)是一种互联网聊天协议,速度快,带宽占用小,用户可以在频道(Channel)群聊(需要服务器)或直接一对一聊天(可以不经过服务器)。so,控制服务器就是IRC服务器,每台肉鸡就是IRC客户端,登录的IRC服务器。黑客通过控制服务器向肉鸡下达指令。
每个肉鸡通常至少开两个线程:一个负责和IRC服务器通讯接受指令,另一个则通过端口扫描尝试感染其他机器。
常用的攻击方式是UDP攻击,它比TCP类型的攻击更难防,因为TCP是需要建立连接的,很容易被IDS/IPS设备RST,也很容易通过设置协议栈Syn Cookies屏蔽掉攻击包。——PS:这里暂时还不懂。。。
5.总结一下
有一部分人专门做这种生意:控制大批计算机,同时访问某服务器导致其瘫痪或暴力破解各种密码。有些攻击是有针对性的,有些完全是随机的端口扫描。现在只能束手无策。。。待我好好研究研究再说。相关文章推荐
- Linux安全--防范用户密码被暴力破解
- Linux用户管理安全宝典:密码防破解与帐号文件保护(一)
- Linux用户管理安全宝典:密码防破解与帐号文件保护(二)
- Linux用户管理安全宝典:密码防破解与帐号文件保护(1)
- Linux用户管理安全宝典:密码防破解与帐号文件保护
- Linux用户管理安全宝典:密码防破解与帐号文件保护
- Linux用户管理安全宝典:密码防破解与帐号文件保护
- 字典法暴力破解Linux用户密码
- Linux用户管理安全宝典:密码防破解与帐号文件保护 推荐
- 防止Linux暴力ssh破解密码方法denyhosts工具
- FREEBSD密码破解(单用户模式未设置安全)
- root用户密码暴力破解
- linux单用户密码破解
- linux root用户密码破解
- linux实现ssh密码暴力破解
- linux认证:ASP提权暴力破解MSSQL用户密码
- FREEBSD密码破解(单用户模式未设置安全)
- 用denyhosts防SSH暴力破解用户密码
- Linux单用户模式修改root密码or禁止单用户模式增强系统安全
- Linux 下的根用户安全管理策略及实践,第 2 部分: 权限安全使用和密码管理
