Mesos源码分析(3): Mesos Master的启动之二
2016-07-24 09:50
330 查看
2. process::firewall::install(move(rules));如果有参数--firewall_rules则会添加规则
对应的代码如下:
| // Initialize firewall rules. if (flags.firewall_rules.isSome()) { vector<Owned<FirewallRule>> rules; const Firewall firewall = flags.firewall_rules.get(); if (firewall.has_disabled_endpoints()) { hashset<string> paths; foreach (const string& path, firewall.disabled_endpoints().paths()) { paths.insert(path); } rules.emplace_back(new DisabledEndpointsFirewallRule(paths)); } process::firewall::install(move(rules)); } |
对应的命令行参数如下:
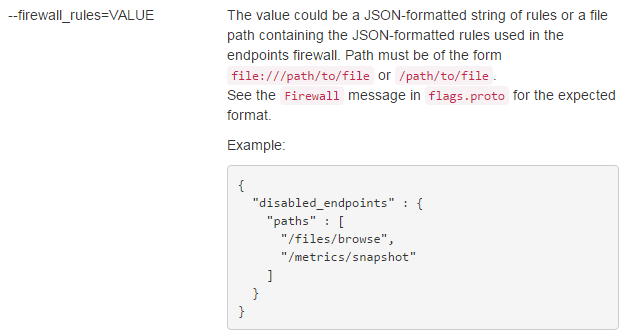
这个参数的主要作用为,并不是Mesos的每一个API都想暴露出来,disabled_endpoints里面就是不能访问的API。
上面的install的代码会做下面的事情


最终会放到环境变量firewallRules里面。
那这些firewall是什么事情起作用的呢?
在3rdparty/libprocess/src/process.cpp里面有函数

| synchronized (firewall_mutex) { // Don't use a const reference, since it cannot be guaranteed // that the rules don't keep an internal state. foreach (Owned<firewall::FirewallRule>& rule, firewallRules) { Option<Response> rejection = rule->apply(socket, *request); if (rejection.isSome()) { VLOG(1) << "Returning '"<< rejection.get().status << "' for '" << request->url.path << "' (firewall rule forbids request)"; // TODO(arojas): Get rid of the duplicated code to return an // error. // Get the HttpProxy pid for this socket. PID<HttpProxy> proxy = socket_manager->proxy(socket); // Enqueue the response with the HttpProxy so that it respects // the order of requests to account for HTTP/1.1 pipelining. dispatch( proxy, &HttpProxy::enqueue, rejection.get(), *request); // Cleanup request. delete request; return; } } } |
相关文章推荐
- 多异步按序执行
- Java遍历文件目录
- virtualenv 指定 python 解释器的版本
- Linux中TFTP使用详解
- git使用入门
- Java千百问_09基础类库(003)_java.math包有什么功能
- android之利用surfaceView实现自定义水印相机
- hdu 1685 Booksort (搜索)
- JavaScript学习小结之使用canvas画“哆啦A梦”时钟
- js之变量的定义
- 5、时间日期和数字
- python3.5类型示意
- javascript权威指南--对象到原始值的转换(未完成)
- servlet、session、jsp的生命周期
- POJ 3268
- Imgproc_1_图像滤波模块
- Scrapy入门
- mysql使用(3)
- 计算机;GPL等开源协议;Linux 哲学思想的炼成;MBR & GPT---fazion in magedu 20.July
- 校招季--献给前端求职路上的你们(H5+C3)
