Linux下https的搭建总结
2016-03-09 09:56
399 查看
一:CA服务器的搭建
[root@ www.linuxidc.com ~]# yum installopenssl*
[root@ www.linuxidc.com ~]# cd /etc/pki/
[root@ www.linuxidc.com pki]# vimtls/openssl.cnf
45dir =/etc/pki/CA
88countryName = optional
89stateOrProvinceName = optional
90organizationName =optional
136countryName_default = CN 一些默认选项
141stateOrProvinceName_default = beijing 一些默认选项
144localityName_default = beijing一些默认选项
[root@ www.linuxidc.com pki]# cd CA
[root@ www.linuxidc.com CA]# mkdir certsnewcerts crl 创建3个目录和两个文件
[root@ www.linuxidc.com CA]# touch index.txtserial
[root@ www.linuxidc.com CA]# echo"01">serial 根索引文件
[root@ www.linuxidc.com CA]#openssl genrsa1024 >private/cakey.pem 创建ca的私钥文件
[root@ www.linuxidc.com CA]# chmod 600private/cakey.pem 改变私钥的权限
[root@ www.linuxidc.com CA]#openssl req -new-key private/cakey.pem -days 3650 -x509 -out cacert.pem 为ca产生一份证书
二.为www服务器颁发证书
[root@ www.linuxidc.com ~]# cd /etc/httpd/
[[root@ www.linuxidc.com httpd]# mkdir certs
[root@ www.linuxidc.com httpd]# cd certs/
[root@ www.linuxidc.com certs]#opensslgenrsa 1024 > httpd.key 产生服务器的私钥
[root@ www.linuxidc.com certs]# openssl req -new -key httpd.key -out httpd.csr产生服务器的请求文件
提示输入一系列的参数,
......
Country Name (2 letter code) [AU]: --------国家
State or Province Name (full name) [Some-State]: ---------省份
Locality Name (eg, city) []: --------------地区名字
Organization Name (eg, company) [Internet Widgits Pty Ltd]: ------公司名
Organizational Unit Name (eg, section) []: -----部门
Common Name (eg, YOUR name) []: ----CA主机名
Email Address []: ---------邮箱
.....
注:Common Name必须和httpd.conf中server name必须一致,否则apache不能启动
启动apache时错误提示为:RSA server certificate CommonName (CN) `Koda' does NOT match server name!?
[root@ www.linuxidc.com certs]# openssl ca-in httpd.csr -out httpd.cert 产生服务器的证书文件
用openssl x509 -noout -text -in httpd.cert可以查看证书的内容。证书实际上包含了Public Key.
[root@ www.linuxidc.com certs]#cp/etc/pki/CA/cacert.pem ./ 拷贝ca的证书文件
[root@ www.linuxidc.com certs]#chmod 600 *
[root@ www.linuxidc.com certs]#yum installmod_ssl*改变文件的权限增加安全性
[root@ www.linuxidc.com certs]#vim/etc/httpd/conf.d/ssl.conf 捆绑证书文件和钥匙文件
112 SSLCertificateFile/etc/httpd/certs/httpd.cert
119 SSLCertificateKeyFile/etc/httpd/certs/httpd.key
128 SSLCertificateChainFile/etc/httpd/certs/cacert.pem
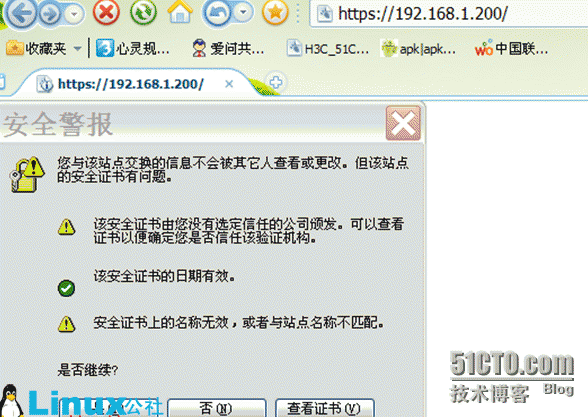
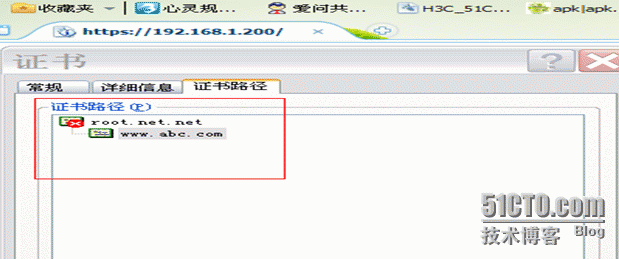
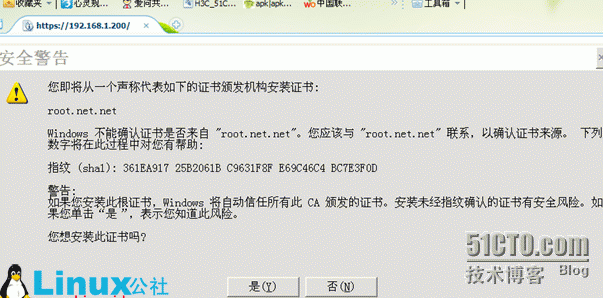
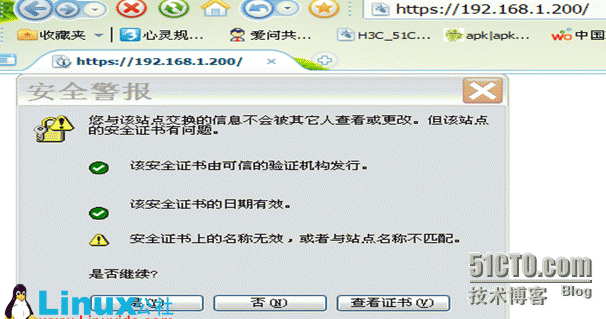
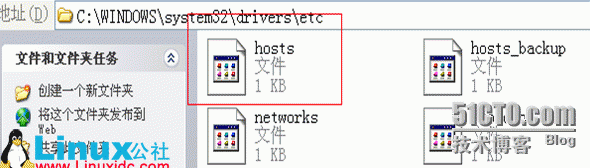
192.168.1.200www.abc.com
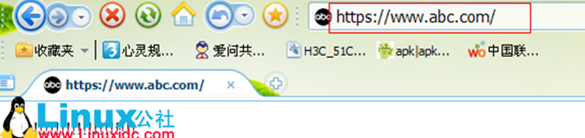
[root@ www.linuxidc.com certs]#netstat -tupln |grep httpd
tcp 0 0:::80 :::* LISTEN 5544/httpd
tcp 0 0:::443 :::* LISTEN 5544/httpd
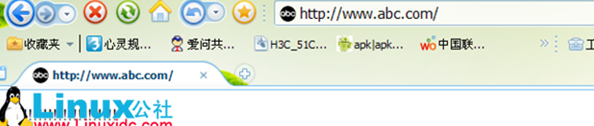
关闭原来的80端口
[root@ www.linuxidc.com certs]# vim/etc/httpd/conf/httpd.conf
134 #Listen 80 注释掉该行
[root@ www.linuxidc.com certs]# servicehttpd restart
Stoppinghttpd: [ OK ]
Startinghttpd: [ OK ]
[root@ www.linuxidc.com certs]# netstat-tupln|grep httpd
tcp 0 0:::443 :::* LISTEN 5483/httpd
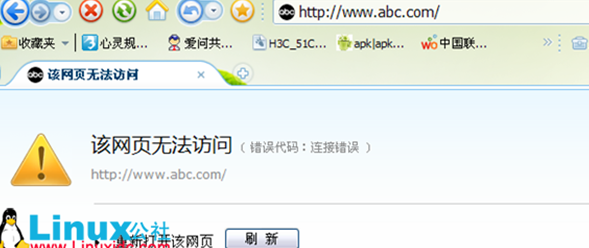
这样www.abc.com就只能够使用https进行访问啦
补充:
一:为www.abc.com 颁发证书192.168.1.200的主机
[root@zzu certs]#vim/etc/httpd/conf.d/ssl.conf
nameVirtualHost 192.168.1.200:443
<VirtualHost 192.168.1.200:443>
DocumentRoot "/var/www/html"
ServerName www.abc.com:443
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLEngine on
SSLProtocol all -SSLv2
SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW
SSLCertificateFile /etc/httpd/certs/httpd.cert
SSLCertificateKeyFile /etc/httpd/certs/httpd.key
SSLCertificateChainFile /etc/pki/CA/cacert.pem
<Files ~ "\.(cgi|shtml|phtml|php3?)$">
SSLOptions +StdEnvVars
</Files>
<Directory "/var/www/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
SetEnvIf User-Agent ".*MSIE.*" \
nokeepalivessl-unclean-shutdown \
downgrade-1.0force-response-1.0
CustomLog logs/ssl_request_log \
"%t %h%{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
二:为 tec.abc.com 颁发证书192.168.1.100的主机
[root@zzu certs]#vim/etc/httpd/conf.d/ssl.conf
<VirtualHost 192.168.1.100:443>
DocumentRoot "/var/www/tec"
ServerName tec.abc.com:443
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLEngine on
SSLProtocol all -SSLv2
SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW
SSLCertificateFile /etc/httpd/certs/httpd1.cert
SSLCertificateKeyFile /etc/httpd/certs/httpd1.key
SSLCertificateChainFile /etc/pki/CA/cacert.pem
<Files ~ "\.(cgi|shtml|phtml|php3?)$">
SSLOptions +StdEnvVars
</Files>
<Directory "/var/www/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
SetEnvIf User-Agent ".*MSIE.*" \
nokeepalivessl-unclean-shutdown \
downgrade-1.0force-response-1.0
CustomLog logs/ssl_request_log \
"%t %h%{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
1). 看SSLCertificateFile,SSLCertificateKeyFile两个配置项,所以应该在httpd下建立子目录certs,然后把签署过的证书文件(.cert)和私钥文件(.key)放在相应的目录
2). 看DocumentRoot,ServerName配置项,ServerName修改为任意你想要得域名,注意:前面生成.csr时输入的Common Name必须于这里的ServerName项一致。
这样启动apache后,访问https://www.my.com将访问/var/www/tec目录下的内容。
3). 移除注释行
LoadModule ssl_module modules/mod_ssl.so
[root@ www.linuxidc.com ~]# yum installopenssl*
[root@ www.linuxidc.com ~]# cd /etc/pki/
[root@ www.linuxidc.com pki]# vimtls/openssl.cnf
45dir =/etc/pki/CA
88countryName = optional
89stateOrProvinceName = optional
90organizationName =optional
136countryName_default = CN 一些默认选项
141stateOrProvinceName_default = beijing 一些默认选项
144localityName_default = beijing一些默认选项
[root@ www.linuxidc.com pki]# cd CA
[root@ www.linuxidc.com CA]# mkdir certsnewcerts crl 创建3个目录和两个文件
[root@ www.linuxidc.com CA]# touch index.txtserial
[root@ www.linuxidc.com CA]# echo"01">serial 根索引文件
[root@ www.linuxidc.com CA]#openssl genrsa1024 >private/cakey.pem 创建ca的私钥文件
[root@ www.linuxidc.com CA]# chmod 600private/cakey.pem 改变私钥的权限
[root@ www.linuxidc.com CA]#openssl req -new-key private/cakey.pem -days 3650 -x509 -out cacert.pem 为ca产生一份证书
二.为www服务器颁发证书
[root@ www.linuxidc.com ~]# cd /etc/httpd/
[[root@ www.linuxidc.com httpd]# mkdir certs
[root@ www.linuxidc.com httpd]# cd certs/
[root@ www.linuxidc.com certs]#opensslgenrsa 1024 > httpd.key 产生服务器的私钥
[root@ www.linuxidc.com certs]# openssl req -new -key httpd.key -out httpd.csr产生服务器的请求文件
提示输入一系列的参数,
......
Country Name (2 letter code) [AU]: --------国家
State or Province Name (full name) [Some-State]: ---------省份
Locality Name (eg, city) []: --------------地区名字
Organization Name (eg, company) [Internet Widgits Pty Ltd]: ------公司名
Organizational Unit Name (eg, section) []: -----部门
Common Name (eg, YOUR name) []: ----CA主机名
Email Address []: ---------邮箱
.....
注:Common Name必须和httpd.conf中server name必须一致,否则apache不能启动
启动apache时错误提示为:RSA server certificate CommonName (CN) `Koda' does NOT match server name!?
[root@ www.linuxidc.com certs]# openssl ca-in httpd.csr -out httpd.cert 产生服务器的证书文件
用openssl x509 -noout -text -in httpd.cert可以查看证书的内容。证书实际上包含了Public Key.
[root@ www.linuxidc.com certs]#cp/etc/pki/CA/cacert.pem ./ 拷贝ca的证书文件
[root@ www.linuxidc.com certs]#chmod 600 *
[root@ www.linuxidc.com certs]#yum installmod_ssl*改变文件的权限增加安全性
[root@ www.linuxidc.com certs]#vim/etc/httpd/conf.d/ssl.conf 捆绑证书文件和钥匙文件
112 SSLCertificateFile/etc/httpd/certs/httpd.cert
119 SSLCertificateKeyFile/etc/httpd/certs/httpd.key
128 SSLCertificateChainFile/etc/httpd/certs/cacert.pem





192.168.1.200www.abc.com

[root@ www.linuxidc.com certs]#netstat -tupln |grep httpd
tcp 0 0:::80 :::* LISTEN 5544/httpd
tcp 0 0:::443 :::* LISTEN 5544/httpd

关闭原来的80端口
[root@ www.linuxidc.com certs]# vim/etc/httpd/conf/httpd.conf
134 #Listen 80 注释掉该行
[root@ www.linuxidc.com certs]# servicehttpd restart
Stoppinghttpd: [ OK ]
Startinghttpd: [ OK ]
[root@ www.linuxidc.com certs]# netstat-tupln|grep httpd
tcp 0 0:::443 :::* LISTEN 5483/httpd


这样www.abc.com就只能够使用https进行访问啦
补充:
一:为www.abc.com 颁发证书192.168.1.200的主机
[root@zzu certs]#vim/etc/httpd/conf.d/ssl.conf
nameVirtualHost 192.168.1.200:443
<VirtualHost 192.168.1.200:443>
DocumentRoot "/var/www/html"
ServerName www.abc.com:443
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLEngine on
SSLProtocol all -SSLv2
SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW
SSLCertificateFile /etc/httpd/certs/httpd.cert
SSLCertificateKeyFile /etc/httpd/certs/httpd.key
SSLCertificateChainFile /etc/pki/CA/cacert.pem
<Files ~ "\.(cgi|shtml|phtml|php3?)$">
SSLOptions +StdEnvVars
</Files>
<Directory "/var/www/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
SetEnvIf User-Agent ".*MSIE.*" \
nokeepalivessl-unclean-shutdown \
downgrade-1.0force-response-1.0
CustomLog logs/ssl_request_log \
"%t %h%{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
二:为 tec.abc.com 颁发证书192.168.1.100的主机
[root@zzu certs]#vim/etc/httpd/conf.d/ssl.conf
<VirtualHost 192.168.1.100:443>
DocumentRoot "/var/www/tec"
ServerName tec.abc.com:443
ErrorLog logs/ssl_error_log
TransferLog logs/ssl_access_log
LogLevel warn
SSLEngine on
SSLProtocol all -SSLv2
SSLCipherSuite ALL:!ADH:!EXPORT:!SSLv2:RC4+RSA:+HIGH:+MEDIUM:+LOW
SSLCertificateFile /etc/httpd/certs/httpd1.cert
SSLCertificateKeyFile /etc/httpd/certs/httpd1.key
SSLCertificateChainFile /etc/pki/CA/cacert.pem
<Files ~ "\.(cgi|shtml|phtml|php3?)$">
SSLOptions +StdEnvVars
</Files>
<Directory "/var/www/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
SetEnvIf User-Agent ".*MSIE.*" \
nokeepalivessl-unclean-shutdown \
downgrade-1.0force-response-1.0
CustomLog logs/ssl_request_log \
"%t %h%{SSL_PROTOCOL}x %{SSL_CIPHER}x \"%r\" %b"
</VirtualHost>
1). 看SSLCertificateFile,SSLCertificateKeyFile两个配置项,所以应该在httpd下建立子目录certs,然后把签署过的证书文件(.cert)和私钥文件(.key)放在相应的目录
2). 看DocumentRoot,ServerName配置项,ServerName修改为任意你想要得域名,注意:前面生成.csr时输入的Common Name必须于这里的ServerName项一致。
这样启动apache后,访问https://www.my.com将访问/var/www/tec目录下的内容。
3). 移除注释行
LoadModule ssl_module modules/mod_ssl.so
相关文章推荐
- 逆向分析网络协议 iOS 篇
- 第四天 网络 handler
- HTTP返回码总结
- P2P网络中DHT算法分析
- HTTP权威指南 第五章 Web服务器
- 通信协议:HTTP、TCP、UDP
- Golang加头和尾部来解决tcp粘包问题.代码片段示例
- Android编程判断网络是否可用及调用系统设置项的方法
- VirtualBox linux 网络设置 Bridged Adapter模式
- 神经元模型和网络结构
- RHEL7概述systemd网络及防火墙GRUB2#破解密码
- GIS+=地理信息+数据库技术——[网络公开课]Oracle技术分享
- HDU 2435 There is a war (网络流-最小割)
- HTTP中Get与Post的区别
- 前端性能优化--合并压缩js,减少http请求次数
- ISO/OSI参考模型,7层网络模型总结
- http://stuf.ro/calling-c-code-from-java-using-jni
- [游戏开发]关于手游客户端网络带宽压力的一点思考
- 多尺度无序池化卷积神经网络——MOP-CNN(MultiScale Orderless Pooling)
- 【网络基本功能七】细说IP地址与子网
