构架https服务器
2015-10-01 11:00
489 查看
1、建立httpd服务器(基于编译的方式进行),要求:
提供两个基于名称的虚拟主机:
(a)www1.stuX.com,页面文件目录为/web/vhosts/www1;错误日志为/var/log/httpd/www1.err,访问日志为/var/log/httpd/www1.access;
(b)www2.stuX.com,页面文件目录为/web/vhosts/www2;错误日志为/var/log/httpd/www2.err,访问日志为/var/log/httpd/www2.access;
(c)为两个虚拟主机建立各自的主页文件index.html,内容分别为其对应的主机名;
(d)通过www1.stuX.com/server-status输出httpd工作状态相关信息,且只允许提供帐号密码才能访问(status:status);
2、为上面的第2个虚拟主机提供https服务,使得用户可以通过https安全的访问此web站点;
(1)要求使用证书认证,证书中要求使用的国家(CN)、州(HA)、城市(ZZ)和组织(MageEdu);
(2)设置部门为Ops,主机名为www2.stuX.com,邮件为admin@stuX.com;
步骤:
1、禁用中心主机,并启用基于主机的虚拟主机项
#DocumentRoot "/var/www/html"
NameVirtualHost 172.16.1.110:80
2、添加两个虚拟主机
<VirtualHost 172.16.1.110:80>
ServerAdmin lpw@lpw.com
DirectoryIndex index.html
<VirtualHost 172.16.1.110:80>
ServerAdmin lpw@lpw.com
DirectoryIndex index.html
DocumentRoot "/web/host/www1/"
ServerName www1.stu.com
LogLevel warn
ErrorLog /var/log/httpd/www1.err
<Directory "/">
AllowOverride None
Options None
Order allow,deny
Allow from all
</Directory>
CustomLog /var/log/httpd/www1.access combined
</VirtualHost>
<VirtualHost 172.16.1.110:80>
ServerAdmin lpw@lpw.com
DocumentRoot "/web/host/www2/"
ServerName www2.stu.com
DirectoryIndex index.html
LogLevel warn
ErrorLog /var/log/httpd/www2.err
CustomLog /var/log/httpd/www2.access combined
<Directory "/">
AllowOverride None
Options None
Order allow,deny
Allow from all
</Directory>
</VirtualHost>
3、创建/web/host/www1目录和/web/host/www2并在每个目录下创建用于测试的index.html文件
mkdir -p web/host/www1
mkdir -p web/host/www2
cd /web/host/www2
echo "www1.stu.com" > index.html
cd /web/host/www2
echo "www2..stu.com" > index.html
4、修改/etc/hosts文件,添加下面内容,可以让主机解析到web服务器
172.16.249.236 www1.stu.com
172.16.249.236 www2.stu.com
5测试虚拟主机可用
[root@localhost conf]# curl http://www1.stu.com www1.stu.com
[root@localhost conf]# curl http://www2.stu.com www2.stu.com
6、创建管理员查看server-status页面的用户(lpw)和密码(111111):
[root@localhost httpd]# htpasswd -c httpd_auth_passwd_file lpw
New password:
Re-type new password:
Adding password for user lpw
[root@localhost httpd]#
7、修改配置文件,启动内置的server-status功能并设置基于用户登录的访问控制
<Location /server-status>
SetHandler server-status
Order allow,deny
Allow from www1.stu.com
Deny from all
AuthType Basic
AuthName "admin can access"
AuthUserFile "/etc/httpd/httpd_auth_passwd_file"
Require user lpw
</Location>
8、使用elinks测试:
[root@localhost httpd]# elinks http://www1.stu.com/server-status
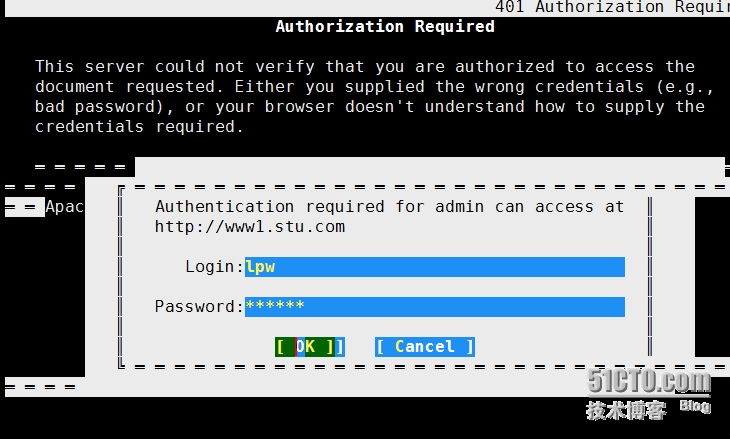
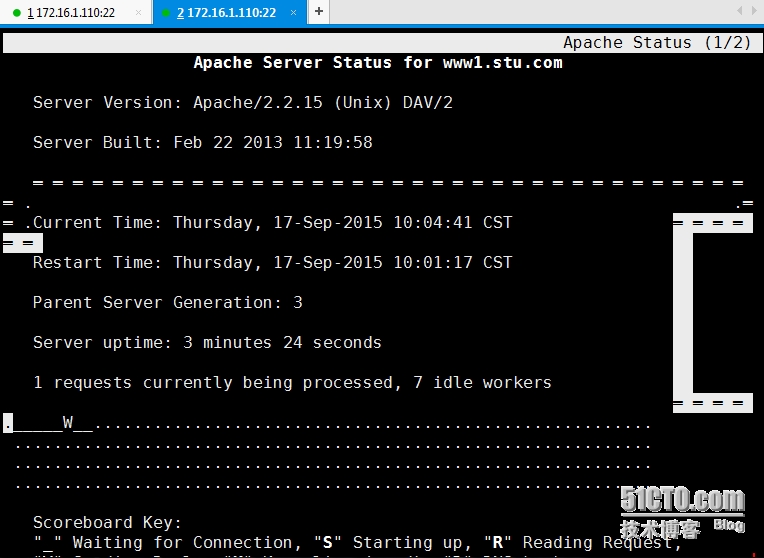
9、设置虚拟主机www2.stu.com可以基于https来访问。
首先,在另外一个主机上建立私有CA,用来完成证书签证和颁发。
[root@localhost CA]# touch index.txt
[root@localhost CA]# echo 01 > serial
创建CA的秘钥对
[root@localhost CA]# (umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
创建CA的自签证书
[root@localhost CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 7300 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CH
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:beijing
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:ops
Common Name (eg, your name or your server's hostname) []:www2.stu.com
Email Address []:lpw@lpw.com
[root@localhost CA]#
创建服务器的秘钥对
[root@localhost httpd]# (umask 077;openssl genrsa -out /etc/httpd/httpd.key 1024)
Generating RSA private key, 1024 bit long modulus
....................++++++
..........++++++
e is 65537 (0x10001)
[root@localhost httpd]#
创建服务器的证书申请签证
[root@localhost httpd]# openssl req -new -key /etc/httpd/httpd.key -days 365 -out /etc/httpd/httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CH
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:beijing
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:ops
Common Name (eg, your name or your server's hostname) []:www2.stu.com
Email Address []:lpw@lpw.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:111111
An optional company name []:
[root@localhost httpd]#
将申请自签证书交给CA签证
[root@localhost CA]# scp root@172.16.1.110:/etc/httpd/httpd.csr ./
The authenticity of host '172.16.1.110 (172.16.1.110)' can't be established.
RSA key fingerprint is 9b:1d:7b:d1:f3:f1:87:52:18:c2:18:6f:dd:57:3c:ec.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.16.1.110' (RSA) to the list of known hosts.
Address 172.16.1.110 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
root@172.16.1.110's password:
httpd.csr 100% 720 0.7KB/s 00:00
[root@localhost CA]#
CA签署证书
[root@localhost CA]# openssl ca -in ./httpd.csr -out ./httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Sep 16 14:03:24 2015 GMT
Not After : Sep 15 14:03:24 2016 GMT
Subject:
countryName = CH
stateOrProvinceName = beijing
organizationName = magedu
organizationalUnitName = ops
commonName = www2.stu.com
emailAddress = lpw@lpw.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
A9:FB:5C:9C:BE:35:ED:4E:B3:EF:94:B7:2A:0A:D2:67:5A:2C:A2:9E
X509v3 Authority Key Identifier:
keyid:C1:CB:14:D8:CF:4B:C3:01:45:75:29:11:38:53:17:9E:C4:F4:31:7C
Certificate is to be certified until Sep 15 14:03:24 2016 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@localhost CA]#
服务器获取证书
[root@localhost httpd]# scp root@172.16.1.112:/etc/pki/CA/httpd.crt ./
[root@localhost httpd]# ls
conf httpd_auth_passwd_file httpd.csr logs run
conf.d httpd.crt httpd.key modules
然后就可以配置http服务器使用ssl功能
确保服务器上有mod_ssl模块(没有的话可以yum install mod_ssl 安装)
[root@localhost httpd]# rpm -q mod_ssl
mod_ssl-2.2.15-26.el6.centos.x86_64
修改/etc/httpd/conf/ssl,conf配置文件
DocumentRoot "/web/host/www2/" #服务器的根路径
ServerName www2.stu.com:443 #服务器的监听地址
SSLCertificateFile /etc/httpd/httpd.crt #服务器的证书
SSLCertificateKeyFile /etc/httpd/httpd.key #服务器的私钥对位置
测试:
[root@localhost CA]# openssl s_client -connect www2.stu.com:443 -CAfile /etc/pki/CA/cacert.pem
CONNECTED(00000003)
depth=1 C = CH, ST = beijing, L = beijing, O = magedu, OU = ops, CN = www2.stu.com, emailAddress = lpw@lpw.com
verify return:1
depth=0 C = CH, ST = beijing, O = magedu, OU = ops, CN = www2.stu.com, emailAddress = lpw@lpw.com
verify return:1
。。。。。。
。。。。。。
---
GET / HTTP/1.1
Host:www2.stu.com
HTTP/1.1 200 OK
Date: Thu, 17 Sep 2015 03:02:14 GMT
Server: Apache/2.2.15 (CentOS)
Last-Modified: Thu, 17 Sep 2015 01:21:05 GMT
ETag: "1fc06-d-51fe73aac4085"
Accept-Ranges: bytes
Content-Length: 13
Content-Type: text/html; charset=UTF-8
www2.stu.com
closed
[root@localhost CA]#
提供两个基于名称的虚拟主机:
(a)www1.stuX.com,页面文件目录为/web/vhosts/www1;错误日志为/var/log/httpd/www1.err,访问日志为/var/log/httpd/www1.access;
(b)www2.stuX.com,页面文件目录为/web/vhosts/www2;错误日志为/var/log/httpd/www2.err,访问日志为/var/log/httpd/www2.access;
(c)为两个虚拟主机建立各自的主页文件index.html,内容分别为其对应的主机名;
(d)通过www1.stuX.com/server-status输出httpd工作状态相关信息,且只允许提供帐号密码才能访问(status:status);
2、为上面的第2个虚拟主机提供https服务,使得用户可以通过https安全的访问此web站点;
(1)要求使用证书认证,证书中要求使用的国家(CN)、州(HA)、城市(ZZ)和组织(MageEdu);
(2)设置部门为Ops,主机名为www2.stuX.com,邮件为admin@stuX.com;
步骤:
1、禁用中心主机,并启用基于主机的虚拟主机项
#DocumentRoot "/var/www/html"
NameVirtualHost 172.16.1.110:80
2、添加两个虚拟主机
<VirtualHost 172.16.1.110:80>
ServerAdmin lpw@lpw.com
DirectoryIndex index.html
<VirtualHost 172.16.1.110:80>
ServerAdmin lpw@lpw.com
DirectoryIndex index.html
DocumentRoot "/web/host/www1/"
ServerName www1.stu.com
LogLevel warn
ErrorLog /var/log/httpd/www1.err
<Directory "/">
AllowOverride None
Options None
Order allow,deny
Allow from all
</Directory>
CustomLog /var/log/httpd/www1.access combined
</VirtualHost>
<VirtualHost 172.16.1.110:80>
ServerAdmin lpw@lpw.com
DocumentRoot "/web/host/www2/"
ServerName www2.stu.com
DirectoryIndex index.html
LogLevel warn
ErrorLog /var/log/httpd/www2.err
CustomLog /var/log/httpd/www2.access combined
<Directory "/">
AllowOverride None
Options None
Order allow,deny
Allow from all
</Directory>
</VirtualHost>
3、创建/web/host/www1目录和/web/host/www2并在每个目录下创建用于测试的index.html文件
mkdir -p web/host/www1
mkdir -p web/host/www2
cd /web/host/www2
echo "www1.stu.com" > index.html
cd /web/host/www2
echo "www2..stu.com" > index.html
4、修改/etc/hosts文件,添加下面内容,可以让主机解析到web服务器
172.16.249.236 www1.stu.com
172.16.249.236 www2.stu.com
5测试虚拟主机可用
[root@localhost conf]# curl http://www1.stu.com www1.stu.com
[root@localhost conf]# curl http://www2.stu.com www2.stu.com
6、创建管理员查看server-status页面的用户(lpw)和密码(111111):
[root@localhost httpd]# htpasswd -c httpd_auth_passwd_file lpw
New password:
Re-type new password:
Adding password for user lpw
[root@localhost httpd]#
7、修改配置文件,启动内置的server-status功能并设置基于用户登录的访问控制
<Location /server-status>
SetHandler server-status
Order allow,deny
Allow from www1.stu.com
Deny from all
AuthType Basic
AuthName "admin can access"
AuthUserFile "/etc/httpd/httpd_auth_passwd_file"
Require user lpw
</Location>
8、使用elinks测试:
[root@localhost httpd]# elinks http://www1.stu.com/server-status


9、设置虚拟主机www2.stu.com可以基于https来访问。
首先,在另外一个主机上建立私有CA,用来完成证书签证和颁发。
[root@localhost CA]# touch index.txt
[root@localhost CA]# echo 01 > serial
创建CA的秘钥对
[root@localhost CA]# (umask 077;openssl genrsa -out /etc/pki/CA/private/cakey.pem 2048)
创建CA的自签证书
[root@localhost CA]# openssl req -new -x509 -key /etc/pki/CA/private/cakey.pem -days 7300 -out /etc/pki/CA/cacert.pem
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CH
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:beijing
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:ops
Common Name (eg, your name or your server's hostname) []:www2.stu.com
Email Address []:lpw@lpw.com
[root@localhost CA]#
创建服务器的秘钥对
[root@localhost httpd]# (umask 077;openssl genrsa -out /etc/httpd/httpd.key 1024)
Generating RSA private key, 1024 bit long modulus
....................++++++
..........++++++
e is 65537 (0x10001)
[root@localhost httpd]#
创建服务器的证书申请签证
[root@localhost httpd]# openssl req -new -key /etc/httpd/httpd.key -days 365 -out /etc/httpd/httpd.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CH
State or Province Name (full name) []:beijing
Locality Name (eg, city) [Default City]:beijing
Organization Name (eg, company) [Default Company Ltd]:magedu
Organizational Unit Name (eg, section) []:ops
Common Name (eg, your name or your server's hostname) []:www2.stu.com
Email Address []:lpw@lpw.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:111111
An optional company name []:
[root@localhost httpd]#
将申请自签证书交给CA签证
[root@localhost CA]# scp root@172.16.1.110:/etc/httpd/httpd.csr ./
The authenticity of host '172.16.1.110 (172.16.1.110)' can't be established.
RSA key fingerprint is 9b:1d:7b:d1:f3:f1:87:52:18:c2:18:6f:dd:57:3c:ec.
Are you sure you want to continue connecting (yes/no)? yes
Warning: Permanently added '172.16.1.110' (RSA) to the list of known hosts.
Address 172.16.1.110 maps to localhost, but this does not map back to the address - POSSIBLE BREAK-IN ATTEMPT!
root@172.16.1.110's password:
httpd.csr 100% 720 0.7KB/s 00:00
[root@localhost CA]#
CA签署证书
[root@localhost CA]# openssl ca -in ./httpd.csr -out ./httpd.crt -days 365
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: Sep 16 14:03:24 2015 GMT
Not After : Sep 15 14:03:24 2016 GMT
Subject:
countryName = CH
stateOrProvinceName = beijing
organizationName = magedu
organizationalUnitName = ops
commonName = www2.stu.com
emailAddress = lpw@lpw.com
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
A9:FB:5C:9C:BE:35:ED:4E:B3:EF:94:B7:2A:0A:D2:67:5A:2C:A2:9E
X509v3 Authority Key Identifier:
keyid:C1:CB:14:D8:CF:4B:C3:01:45:75:29:11:38:53:17:9E:C4:F4:31:7C
Certificate is to be certified until Sep 15 14:03:24 2016 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@localhost CA]#
服务器获取证书
[root@localhost httpd]# scp root@172.16.1.112:/etc/pki/CA/httpd.crt ./
[root@localhost httpd]# ls
conf httpd_auth_passwd_file httpd.csr logs run
conf.d httpd.crt httpd.key modules
然后就可以配置http服务器使用ssl功能
确保服务器上有mod_ssl模块(没有的话可以yum install mod_ssl 安装)
[root@localhost httpd]# rpm -q mod_ssl
mod_ssl-2.2.15-26.el6.centos.x86_64
修改/etc/httpd/conf/ssl,conf配置文件
DocumentRoot "/web/host/www2/" #服务器的根路径
ServerName www2.stu.com:443 #服务器的监听地址
SSLCertificateFile /etc/httpd/httpd.crt #服务器的证书
SSLCertificateKeyFile /etc/httpd/httpd.key #服务器的私钥对位置
测试:
[root@localhost CA]# openssl s_client -connect www2.stu.com:443 -CAfile /etc/pki/CA/cacert.pem
CONNECTED(00000003)
depth=1 C = CH, ST = beijing, L = beijing, O = magedu, OU = ops, CN = www2.stu.com, emailAddress = lpw@lpw.com
verify return:1
depth=0 C = CH, ST = beijing, O = magedu, OU = ops, CN = www2.stu.com, emailAddress = lpw@lpw.com
verify return:1
。。。。。。
。。。。。。
---
GET / HTTP/1.1
Host:www2.stu.com
HTTP/1.1 200 OK
Date: Thu, 17 Sep 2015 03:02:14 GMT
Server: Apache/2.2.15 (CentOS)
Last-Modified: Thu, 17 Sep 2015 01:21:05 GMT
ETag: "1fc06-d-51fe73aac4085"
Accept-Ranges: bytes
Content-Length: 13
Content-Type: text/html; charset=UTF-8
www2.stu.com
closed
[root@localhost CA]#
相关文章推荐
- http header 详解
- zeromq源码分析–TCP连接处理流程
- 网络流模板
- 网络编程--IO模型示例
- C++实现网络编程 服务端与客户端原代码
- CentOS首次安装,网络环境配置
- angular 使用$http.jsonp进行跨域访问以及修改目标JSON
- http://code.662p.com/view/5141.html
- The superclass "javax.servlet.http.HttpServlet" was not found on the Java Build Path
- Delphi IDHTTP用法详解(六种用法)
- 《深入理解Linux网络技术内幕》阅读笔记(七)
- [网络和多线程]5、线程通信
- [网络和多线程]4、线程同步
- [网络和多线程]2、pThread 的基本使用方法(不推荐使用)
- 浏览器的工作原理:新式网络浏览器幕后揭秘
- HDU 5490 Simple Matrix (2015合肥站网络赛1007 数学题)
- 《深入理解Linux网络技术内幕》阅读笔记(六)
- Httpd学习笔记
- JavaHTTP下载视频
- ACM学习-破坏行动-最大网络流
