ZooKeeper 笔记(5) ACL(Access Control List)访问控制列表
2015-09-28 15:17
567 查看
zk做为分布式架构中的重要中间件,通常会在上面以节点的方式存储一些关键信息,默认情况下,所有应用都可以读写任何节点,在复杂的应用中,这不太安全,ZK通过ACL机制来解决访问权限问题,详见官网文档:http://zookeeper.apache.org/doc/r3.4.6/zookeeperProgrammers.html#sc_ZooKeeperAccessControl
总体来说,ZK的节点有5种操作权限:
CREATE、READ、WRITE、DELETE、ADMIN 也就是 增、删、改、查、管理权限,这5种权限简写为crwda(即:每个单词的首字符缩写)
注:这5种权限中,delete是指对子节点的删除权限,其它4种权限指对自身节点的操作权限
身份的认证有4种方式:
world:默认方式,相当于全世界都能访问
auth:代表已经认证通过的用户(cli中可以通过addauth digest user:pwd 来添加当前上下文中的授权用户)
digest:即用户名:密码这种方式认证,这也是业务系统中最常用的
ip:使用Ip地址认证
Cli命令行下可以这样测试:
View Code
然后写一段代码测试一下:
输出结果:
从zkclient的使用结果看,与cli操作效果一样。
最后:关于多级节点之间的ACL,并非继承关系,但是也有些一联系,这是初次接触ACL中比较难理解的地方:

从这张图上可以发现,子节点/a/b的控制权限范围(全世界都能做任何事)可以超出父节点的范围(仅限:user-a:pwd:a具有read/admin权限)
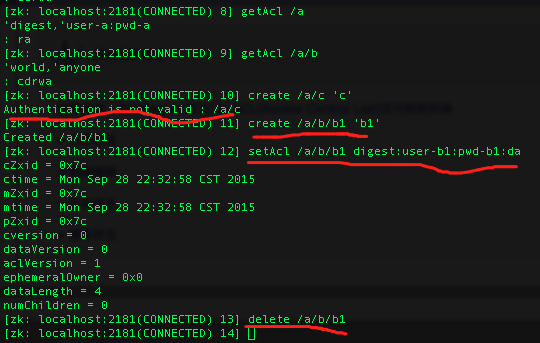
继续,看上面的这4条红线标注的地方,从上向下一个个解释:
红线1:因为/a只有user-a:pwd-a有ra权限,即:没用户具有c(create)权限,所以不能创建子节点
红线2:因为/a/b为world:anyone:cdrwa权限,即无限制,所以在/a/b下创建子节点b1,地球人已经无法阻止,创建成功
红线3:给/a/b/b1指定了user-b1:pwd-b1的da权限(即:delete+admin)
(注:重温下前面提到的setAcl 二种模式,
一种是setAcl /path digest:username:encrypedpwd:crwda 用这种方式时,encrypedpwd用户必须是密文,
另一种方式是先addauth digest:usrname:password 先把授权信息加入上下文,这里password用的是明文,然后再setAcl /path auth:username:password:crdwa
所以如果在cli控制台测试,强烈建议用第二种方式,否则象上图中的方式用错了方式,pwd-b1在zk中被认为是密文,要解密出来几乎不可能,所以设置后,相当于这个节点就废了,因为你不知道密码,要操作该节点时,提供不了正确的认证信息)
红线4:还是刚才的理由,因为/a/b为world:anyone:cdrwa,没有限制,所以删除其下的子节点不受阻挡。

从上图可以看出,无法get父节点的内容,但是可以get子节点的内容,再次说明父、子节点的权限没直接关系,但是做delete时,上面的例子却遇到了麻烦:
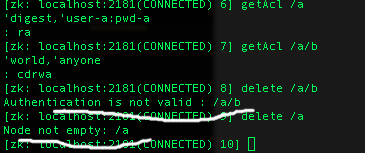
想删除/a/b时,由于父节点/a的ACL列表里,只有ra权限,没有d权限,所以无法删除子节点。想删除/a时,发现下面还有子节点b,节点非空无法删除,所以这个示例就无解了(因为根据前面的操作,密码也还原不出来,也就无法修改ACL属性),而根节点/也无法删除,解决办法,只能到data目录里清空所有数据,再重启zk,但是这样就相当于所有数据全扔了,所以在设计ACL时,对于delete权限,要谨慎规划,在测试zk集群上做好测试,再转到生产环境操作。
最后给一些权限组合的测试结果:
要修改某个节点的ACL属性,必须具有read、admin二种权限
要删除某个节点下的子节点,必须具有对父节点的read权限,以及父节点的delete权限
参考文章:
https://ihong5.wordpress.com/2014/07/10/apache-zookeeper-acl-access-control-list-getting-permission-sets/
https://ihong5.wordpress.com/2014/07/24/apache-zookeeper-setting-acl-in-zookeeper-client/
https://ihong5.wordpress.com/2014/06/24/znode-types-and-how-to-create-read-delete-and-write-in-zookeeper-via-zkclient/
http://zookeeper.apache.org/doc/r3.4.6/zookeeperProgrammers.html#sc_ZooKeeperAccessControl
总体来说,ZK的节点有5种操作权限:
CREATE、READ、WRITE、DELETE、ADMIN 也就是 增、删、改、查、管理权限,这5种权限简写为crwda(即:每个单词的首字符缩写)
注:这5种权限中,delete是指对子节点的删除权限,其它4种权限指对自身节点的操作权限
身份的认证有4种方式:
world:默认方式,相当于全世界都能访问
auth:代表已经认证通过的用户(cli中可以通过addauth digest user:pwd 来添加当前上下文中的授权用户)
digest:即用户名:密码这种方式认证,这也是业务系统中最常用的
ip:使用Ip地址认证
Cli命令行下可以这样测试:
<?xml version="1.0" encoding="UTF-8"?> <project xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 http://maven.apache.org/xsd/maven-4.0.0.xsd"> <modelVersion>4.0.0</modelVersion> <groupId>yjmyzz</groupId> <artifactId>zkclient-demo</artifactId> <version>1.0</version> <dependencies> <dependency> <groupId>org.apache.zookeeper</groupId> <artifactId>zookeeper</artifactId> <version>3.4.6</version> </dependency> <dependency> <groupId>com.101te</groupId> <artifactId>zkclient</artifactId> <version>0.7</version> <classifier>dev</classifier> </dependency> <dependency> <groupId>log4j</groupId> <artifactId>log4j</artifactId> <version>1.2.17</version> </dependency> </dependencies> </project>
View Code
然后写一段代码测试一下:
package yjmyzz.zk;
import org.I0Itec.zkclient.ZkClient;
import org.apache.zookeeper.*;
import org.apache.zookeeper.data.ACL;
import org.apache.zookeeper.data.Id;
import org.apache.zookeeper.data.Stat;
import org.apache.zookeeper.server.auth.DigestAuthenticationProvider;
import java.io.IOException;
import java.security.NoSuchAlgorithmException;
import java.util.ArrayList;
import java.util.List;
import java.util.Map;
public class Main {
private static final String zkAddress = "localhost:2181";
private static final String testNode = "/test";
private static final String readAuth = "read-user:123456";
private static final String writeAuth = "write-user:123456";
private static final String deleteAuth = "delete-user:123456";
private static final String allAuth = "super-user:123456";
private static final String adminAuth = "admin-user:123456";
private static final String digest = "digest";
private static void initNode() throws NoSuchAlgorithmException {
ZkClient zkClient = new ZkClient(zkAddress);
zkClient.addAuthInfo(digest, allAuth.getBytes());
if (zkClient.exists(testNode)) {
zkClient.delete(testNode);
System.out.println("节点删除成功!");
}
List<ACL> acls = new ArrayList<ACL>();
acls.add(new ACL(ZooDefs.Perms.ALL, new Id(digest, DigestAuthenticationProvider.generateDigest(allAuth))));
acls.add(new ACL(ZooDefs.Perms.READ, new Id(digest, DigestAuthenticationProvider.generateDigest(readAuth))));
acls.add(new ACL(ZooDefs.Perms.WRITE, new Id(digest, DigestAuthenticationProvider.generateDigest(writeAuth))));
acls.add(new ACL(ZooDefs.Perms.DELETE, new Id(digest, DigestAuthenticationProvider.generateDigest(deleteAuth))));
acls.add(new ACL(ZooDefs.Perms.ADMIN, new Id(digest, DigestAuthenticationProvider.generateDigest(adminAuth))));
zkClient.createPersistent(testNode, "test-data", acls);
System.out.println(zkClient.readData(testNode));
System.out.println("节点创建成功!");
zkClient.close();
}
private static void readTest() {
ZkClient zkClient = new ZkClient(zkAddress);
try {
System.out.println(zkClient.readData(testNode));//没有认证信息,读取会出错
} catch (Exception e) {
System.err.println(e.getMessage());
}
try {
zkClient.addAuthInfo(digest, adminAuth.getBytes());
System.out.println(zkClient.readData(testNode));//admin权限与read权限不匹配,读取也会出错
} catch (Exception e) {
System.err.println(e.getMessage());
}
try {
zkClient.addAuthInfo(digest, readAuth.getBytes());
System.out.println(zkClient.readData(testNode));//只有read权限的认证信息,才能正常读取
} catch (Exception e) {
System.err.println(e.getMessage());
}
zkClient.close();
}
private static void writeTest() {
ZkClient zkClient = new ZkClient(zkAddress);
try {
zkClient.writeData(testNode, "new-data");//没有认证信息,写入会失败
} catch (Exception e) {
System.err.println(e.getMessage());
}
try {
zkClient.addAuthInfo(digest, writeAuth.getBytes());
zkClient.writeData(testNode, "new-data");//加入认证信息后,写入正常
} catch (Exception e) {
System.err.println(e.getMessage());
}
try {
zkClient.addAuthInfo(digest, readAuth.getBytes());
System.out.println(zkClient.readData(testNode));//读取新值验证
} catch (Exception e) {
System.err.println(e.getMessage());
}
zkClient.close();
}
private static void deleteTest() {
ZkClient zkClient = new ZkClient(zkAddress);
//zkClient.addAuthInfo(digest, deleteAuth.getBytes());
try {
//System.out.println(zkClient.readData(testNode));
zkClient.delete(testNode);
System.out.println("节点删除成功!");
} catch (Exception e) {
System.err.println(e.getMessage());
}
zkClient.close();
}
// private static void deleteTest2() throws IOException, InterruptedException, KeeperException {
// //使用zookeeper原生的API进行删除(注:delete权限指有没有权限删除子节点)
// ZooKeeper zk = new ZooKeeper(zkAddress, 300000, new DemoWatcher());
// zk.delete(testNode, -1);
// System.out.println("节点删除成功");
// zk.close();
// }
//
// static class DemoWatcher implements Watcher {
// @Override
// public void process(WatchedEvent event) {
// System.out.println("----------->");
// System.out.println("path:" + event.getPath());
// System.out.println("type:" + event.getType());
// System.out.println("stat:" + event.getState());
// System.out.println("<-----------");
// }
// }
private static void changeACLTest() {
ZkClient zkClient = new ZkClient(zkAddress);
//注:zkClient.setAcl方法查看源码可以发现,调用了readData、setAcl二个方法
//所以要修改节点的ACL属性,必须同时具备read、admin二种权限
zkClient.addAuthInfo(digest, adminAuth.getBytes());
zkClient.addAuthInfo(digest, readAuth.getBytes());
try {
List<ACL> acls = new ArrayList<ACL>();
acls.add(new ACL(ZooDefs.Perms.ALL, new Id(digest, DigestAuthenticationProvider.generateDigest(adminAuth))));
zkClient.setAcl(testNode, acls);
Map.Entry<List<ACL>, Stat> aclResult = zkClient.getAcl(testNode);
System.out.println(aclResult.getKey());
} catch (Exception e) {
System.err.println(e.getMessage());
}
zkClient.close();
}
public static void main(String[] args) throws Exception {
initNode();
System.out.println("---------------------");
readTest();
System.out.println("---------------------");
writeTest();
System.out.println("---------------------");
changeACLTest();
System.out.println("---------------------");
deleteTest();
//deleteTest2();
}
}输出结果:
test-data
节点创建成功!
---------------------
org.apache.zookeeper.KeeperException$NoAuthException: KeeperErrorCode = NoAuth for /test
org.apache.zookeeper.KeeperException$NoAuthException: KeeperErrorCode = NoAuth for /test
test-data
---------------------
org.apache.zookeeper.KeeperException$NoAuthException: KeeperErrorCode = NoAuth for /test
new-data
---------------------
[31,s{'digest,'admin-user:mAlW21Phn07yOvWnKJYq2sCMoZw=}
]
---------------------
节点删除成功!从zkclient的使用结果看,与cli操作效果一样。
最后:关于多级节点之间的ACL,并非继承关系,但是也有些一联系,这是初次接触ACL中比较难理解的地方:

从这张图上可以发现,子节点/a/b的控制权限范围(全世界都能做任何事)可以超出父节点的范围(仅限:user-a:pwd:a具有read/admin权限)

继续,看上面的这4条红线标注的地方,从上向下一个个解释:
红线1:因为/a只有user-a:pwd-a有ra权限,即:没用户具有c(create)权限,所以不能创建子节点
红线2:因为/a/b为world:anyone:cdrwa权限,即无限制,所以在/a/b下创建子节点b1,地球人已经无法阻止,创建成功
红线3:给/a/b/b1指定了user-b1:pwd-b1的da权限(即:delete+admin)
(注:重温下前面提到的setAcl 二种模式,
一种是setAcl /path digest:username:encrypedpwd:crwda 用这种方式时,encrypedpwd用户必须是密文,
另一种方式是先addauth digest:usrname:password 先把授权信息加入上下文,这里password用的是明文,然后再setAcl /path auth:username:password:crdwa
所以如果在cli控制台测试,强烈建议用第二种方式,否则象上图中的方式用错了方式,pwd-b1在zk中被认为是密文,要解密出来几乎不可能,所以设置后,相当于这个节点就废了,因为你不知道密码,要操作该节点时,提供不了正确的认证信息)
红线4:还是刚才的理由,因为/a/b为world:anyone:cdrwa,没有限制,所以删除其下的子节点不受阻挡。

从上图可以看出,无法get父节点的内容,但是可以get子节点的内容,再次说明父、子节点的权限没直接关系,但是做delete时,上面的例子却遇到了麻烦:

想删除/a/b时,由于父节点/a的ACL列表里,只有ra权限,没有d权限,所以无法删除子节点。想删除/a时,发现下面还有子节点b,节点非空无法删除,所以这个示例就无解了(因为根据前面的操作,密码也还原不出来,也就无法修改ACL属性),而根节点/也无法删除,解决办法,只能到data目录里清空所有数据,再重启zk,但是这样就相当于所有数据全扔了,所以在设计ACL时,对于delete权限,要谨慎规划,在测试zk集群上做好测试,再转到生产环境操作。
最后给一些权限组合的测试结果:
要修改某个节点的ACL属性,必须具有read、admin二种权限
要删除某个节点下的子节点,必须具有对父节点的read权限,以及父节点的delete权限
参考文章:
https://ihong5.wordpress.com/2014/07/10/apache-zookeeper-acl-access-control-list-getting-permission-sets/
https://ihong5.wordpress.com/2014/07/24/apache-zookeeper-setting-acl-in-zookeeper-client/
https://ihong5.wordpress.com/2014/06/24/znode-types-and-how-to-create-read-delete-and-write-in-zookeeper-via-zkclient/
http://zookeeper.apache.org/doc/r3.4.6/zookeeperProgrammers.html#sc_ZooKeeperAccessControl
相关文章推荐
- 代码静态分析工具
- PHP操作数据库
- php 二维数据的排重和排序
- Android 电容屏和电阻屏
- HDU 5480 Conturbatio (象棋_找规律)
- 回家前的随笔
- OnScrollListener回调分析
- 错误和异常(Errors and Exceptions)
- 虚函数
- BA--干球温度、露点温度和湿球温度--概念
- 二叉树中和为某一值的路径
- HTTP制作代理服务器
- MPLS 标签模式/分发行为/保留模式/标签空间
- Android下抓包工具
- Eclipse设置默认文件的打开程序
- 给网址结尾加上反斜杠
- 子集合(算法)
- Linux下安装Yii2.0
- 输入输出(Input and Output)
- 搭建一个免费的,无限流量的Blog----github Pages和Jekyll入门
