进程模块枚举与隐藏
2015-05-11 21:34
288 查看
这附图是我见过关于利用PEB查看模块信息最准确的一幅。
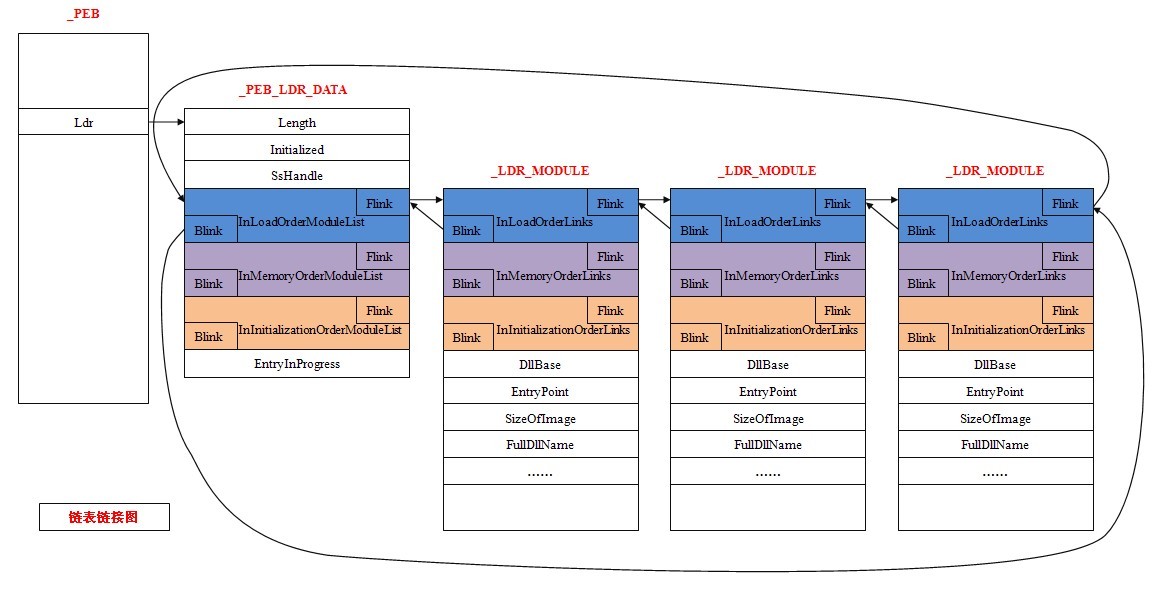
获取TEB
查看PEB
查看ldr(类似头结点)
查看模块结点

获取TEB
lkd> !teb TEB at 7ffdd000 ExceptionList: 00c2976c StackBase: 00c30000 StackLimit: 00c23000 SubSystemTib: 00000000 FiberData: 00001e00 ArbitraryUserPointer: 00000000 Self: 7ffdd000 EnvironmentPointer: 00000000 ClientId: 00000238 . 000003b8 RpcHandle: 00000000 Tls Storage: 00000000 PEB Address: 7ffdf000 *** LastErrorValue: 0 LastStatusValue: c0000139 Count Owned Locks: 0 HardErrorMode: 0
查看PEB
lkd> dt _peb 7ffdf000 nt!_PEB +0x000 InheritedAddressSpace : 0 '' +0x001 ReadImageFileExecOptions : 0 '' +0x002 BeingDebugged : 0 '' +0x003 SpareBool : 0 '' +0x004 Mutant : 0xffffffff Void +0x008 ImageBaseAddress : 0x01000000 Void +0x00c Ldr : 0x00191e90 _PEB_LDR_DATA *** +0x010 ProcessParameters : 0x00020000 _RTL_USER_PROCESS_PARAMETERS +0x014 SubSystemData : (null) +0x018 ProcessHeap : 0x00090000 Void +0x01c FastPebLock : 0x7c99d600 _RTL_CRITICAL_SECTION +0x020 FastPebLockRoutine : 0x7c921000 Void +0x024 FastPebUnlockRoutine : 0x7c9210e0 Void +0x028 EnvironmentUpdateCount : 1 +0x02c KernelCallbackTable : 0x77d12970 Void +0x030 SystemReserved : [1] 0 +0x034 AtlThunkSListPtr32 : 0 +0x038 FreeList : (null) +0x03c TlsExpansionCounter : 0 +0x040 TlsBitmap : 0x7c99d5c0 Void +0x044 TlsBitmapBits : [2] 0x3ffffff
查看ldr(类似头结点)
lkd> dt _peb_ldr_data 191e90 -r1 nt!_PEB_LDR_DATA +0x000 Length : 0x28 +0x004 Initialized : 0x1 '' +0x008 SsHandle : (null) +0x00c InLoadOrderModuleList : _LIST_ENTRY [ 0x191ec0 - 0x194120 ] +0x000 Flink : 0x00191ec0 _LIST_ENTRY [ 0x191f18 - 0x191e9c ] +0x004 Blink : 0x00194120 _LIST_ENTRY [ 0x191e9c - 0x194030 ] +0x014 InMemoryOrderModuleList : _LIST_ENTRY [ 0x191ec8 - 0x194128 ] +0x000 Flink : 0x00191ec8 _LIST_ENTRY [ 0x191f20 - 0x191ea4 ] *** +0x004 Blink : 0x00194128 _LIST_ENTRY [ 0x191ea4 - 0x194038 ] +0x01c InInitializationOrderModuleList : _LIST_ENTRY [ 0x191f28 - 0x194130 ] +0x000 Flink : 0x00191f28 _LIST_ENTRY [ 0x191fd0 - 0x191eac ] +0x004 Blink : 0x00194130 _LIST_ENTRY [ 0x191eac - 0x194040 ] +0x024 EntryInProgress : (null)
查看模块结点
lkd> dt _ldr_data_table_entry 191ec8 -r1 nt!_LDR_DATA_TABLE_ENTRY +0x000 InLoadOrderLinks : _LIST_ENTRY [ 0x191f20 - 0x191ea4 ] +0x000 Flink : 0x00191f20 _LIST_ENTRY [ 0x191fc8 - 0x191ec8 ] +0x004 Blink : 0x00191ea4 _LIST_ENTRY [ 0x191ec8 - 0x194248 ] +0x008 InMemoryOrderLinks : _LIST_ENTRY [ 0x0 - 0x0 ] +0x000 Flink : (null) +0x004 Blink : (null) +0x010 InInitializationOrderLinks : _LIST_ENTRY [ 0x1000000 - 0x1058c77 ] +0x000 Flink : 0x01000000 _LIST_ENTRY [ 0x905a4d - 0x3 ] +0x004 Blink : 0x01058c77 _LIST_ENTRY [ 0x896e8 - 0xfdc3e900 ] +0x018 DllBase : 0x00097000 Void +0x01c EntryPoint : 0x007c007a Void +0x020 SizeOfImage : 0x2060c +0x024 FullDllName : _UNICODE_STRING "windbg.exe" +0x000 Length : 0x14 +0x002 MaximumLength : 0x16 +0x004 Buffer : 0x00020672 "windbg.exe" +0x02c BaseDllName : _UNICODE_STRING "--- memory read error at address 0x0000ffff ---" +0x000 Length : 0x5000 +0x002 MaximumLength : 0 +0x004 Buffer : 0x0000ffff "--- memory read error at address 0x0000ffff ---" +0x034 Flags : 0x192fcc +0x038 LoadCount : 0xb310 +0x03a TlsIndex : 0x7c99 +0x03c HashLinks : _LIST_ENTRY [ 0x4b6734c3 - 0x0 ] +0x000 Flink : 0x4b6734c3 _LIST_ENTRY +0x004 Blink : (null) +0x03c SectionPointer : 0x4b6734c3 Void +0x040 CheckSum : 0 +0x044 TimeDateStamp : 0 +0x044 LoadedImports : (null) +0x048 EntryPointActivationContext : 0x000b000b Void +0x04c PatchInformation : 0x00080158 Void
demo
#include <stdio.h>
#include <windows.h>
DWORD* __cdecl getPEB ()
{
__asm{
mov eax,fs:[0x30]
}
}
void EnumModule()
{
DWORD *PEB = NULL,
*ldr = NULL,
*Flink =NULL,
*p = NULL,
*BaseAddr= NULL,
*FULLDllName= NULL;
PEB = getPEB();
ldr =(DWORD*) (*(DWORD *) (PEB+0x3));
Flink=*(DWORD**)((unsigned char *)ldr+0x14);
p = Flink; //header
p=*((DWORD **)p);
while (p !=Flink) //end when p-> first
{
BaseAddr = *( (DWORD **) ( (unsigned char *) p+0x18-0x8));
FULLDllName= *((DWORD **)( (unsigned char *) p+0x28-0x8));
if (BaseAddr == NULL)
{
break;
}
printf("ImageBase=%08x \t\t ModuleName= %S \r\n",BaseAddr,FULLDllName);
p=*((DWORD **)p);
}
}
BOOL deleteNode(DWORD * node)
{
**( (DWORD **)(node + 1) ) = (DWORD*)(*node);
//*(*(*node)+1)=node+1;
*(*(DWORD **)node +1) =*(*(DWORD **)node +1);
return TRUE;
}
void HideModule(const char * ModuleName)
{
DWORD* ldr,flink,p,peb,baseaddr;
HMODULE hMod=GetModuleHandle(ModuleName);
peb = getPEB();
ldr= *(DWORD **)((unsigned char *)peb+0xc);
flink = *(DWORD**)((unsigned char*)ldr+0xc);
p = flink;
do {
baseaddr = (DWORD *) (*(DWORD*)((unsigned char *)p + 0x18 ));
if (baseaddr ==(DWORD *) hMod)
{
deleteNode(p);
break;
}
// p=(DWORD*) (*p);
p =*((DWORD **)p);
} while (p !=flink);
//flink =(DWORD *)((unsigned char *)*ldr +0x14);
flink = *(DWORD**)((unsigned char *)ldr +0x14);
p = flink;
do
{
// baseaddr =(DWORD *)(*((DWORD*)((unsigned char *)p+0x20)));
baseaddr =*(DWORD **)((unsigned char *)p +0x10);
if (baseaddr == (DWORD*) hMod)
{
deleteNode(p);
break;
}
p =*(DWORD **)p;
} while (p !=flink);
//flink = (DWORD*) ((unsigned char *) *ldr +0x1c);
flink = *(DWORD**)((unsigned char *)ldr +0x1c);
p = flink;
do
{
baseaddr=(DWORD *) *(DWORD*)((unsigned char *)p+0x8);
if (baseaddr == (DWORD*) hMod)
{
deleteNode(p);
break;
}
p=*(DWORD **)p;
} while ( p !=flink);
}
int main()
{
EnumModule();
HideModule("kernel32.dll");
EnumModule();
return 0;
}
相关文章推荐
- VB 枚举隐藏进程
- 通过PEB的Ldr枚举进程内所有已加载的模块
- 通过PEB的Ldr枚举进程内所有已加载的模块
- HOOK SwapContext 枚举隐藏进程(学习笔记4)(3)
- 进程中dll模块的隐藏
- 【进程处理】3,MFC枚举当前进程所有模块
- VC++枚举进程与模块
- VC++实现枚举进程与模块
- 暴力枚举进程模块
- VC++实现枚举进程与模块
- 基于visual c++之windows核心编程代码分析(19)枚举进程以及进程加载模块信息
- C# 枚举进程模块
- ZwQueryVirtualMemory枚举进程模块
- 用ZwQueryVirtualMemory枚举进程模块
- 用ZwQueryVirtualMemory枚举进程模块
- 通过PEB枚举进程中所有模块
- 进程中dll模块的隐藏
- HOOK SwapContext 枚举隐藏进程(学习笔记4)
- 用ZwQueryVirtualMemory枚举进程模块
- 枚举PEB获取进程模块列表
