openssl 升级到OpenSSL 1.0.1g 修复HEARTBEATS漏洞
2014-04-11 15:16
393 查看
CentOS 6.4 64位
查看当前的ssl版本
升级openssl
升级前请关闭selinux
为什么升级openssh,因为用xshell或者SecureCRT等终端连接服务器是用ssh,现在查看ssh所用openssl所用的版本还是这样的
# rpm -qa openssl
openssl-1.0.1e-16.el6_5.14.x86_64
# rpm -q --changelog openssl-1.0.1e | grep CVE-2014-0160
- fix CVE-2014-0160 - information disclosure in TLS heartbeat extension
说明漏洞已经修复
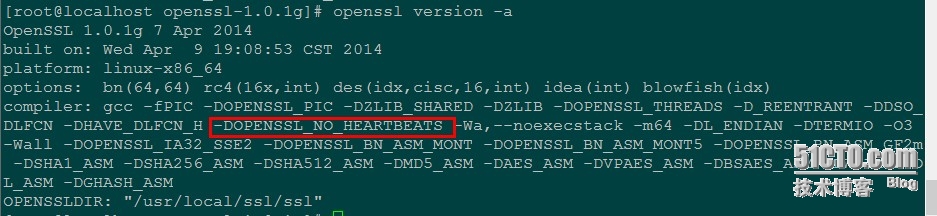
升级 openssh (编译时候请按文章最下面,添加
升级完成
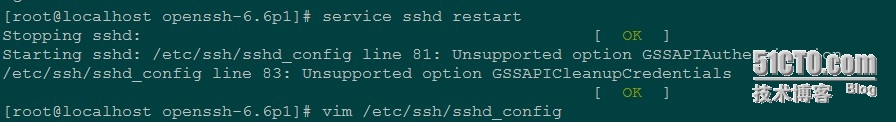
当执行service sshd restart 的时候有错误提示
vim /etc/ssh/sshd_config 把81和83行注释
再执行就没问题了
附:
Unsupported option GSSAPIAuthentication 和 Unsupported option GSSAPICleanupCredentials
这两个认证机制的解决方法:
vim /etc/ssh/sshd_config

上述的代码
升级前关闭selinux升级ssl,sshyum install zlib zlib-devel -y
yum install krb5-devel.x86_64 -y
wget http://www.openssl.org/source/openssl-1.0.1g.tar.gztar -xzf openssl-1.0.1g.tar.gzcd openssl-1.0.1g./config --prefix=/usr/local/ssl shared zlib-dynamic enable-camellia -DOPENSSL_NO_HEARTBEATS makemake installopenssl versionmv /usr/bin/openssl /usr/bin/openssl.oldmv /usr/include/openssl /usr/include/openssloldln -s /usr/local/ssl/bin/openssl /usr/bin/opensslln -s /usr/local/ssl/include/openssl/ /usr/include/opensslecho "/usr/local/ssl/lib/" >>/etc/ld.so.confldconfig -v|grep sslopenssl versioncd ..wget http://mirror.internode.on.net/pub/OpenBSD/OpenSSH/portable/openssh-6.6p1.tar.gzyum install pam* -ytar -xzf openssh-6.6p1.tar.gzcd openssh-6.6p1./configure --prefix=/usr --sysconfdir=/etc/ssh --with-pam --with-zlib --with-ssl-dir=/usr/local/ssl --with-md5-passwords --mandir=/usr/share/man --with-kerberos5=/usr/lib64/libkrb5.somakemake installssh -Vcd ..
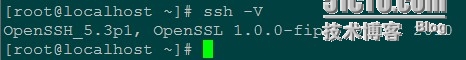
查看当前的ssl版本

[root@localhost ~]# ssh -V OpenSSH_5.3p1, OpenSSL 1.0.0-fips 29 Mar 2010
升级openssl
升级前请关闭selinux
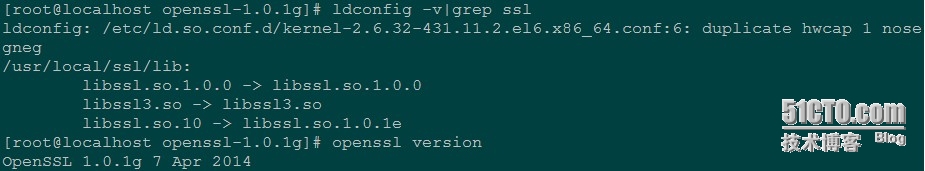
yum install zlib zlib-devel krb5-devel.x86_64 -y wget http://www.openssl.org/source/openssl-1.0.1g.tar.gz tar -xzf openssl-1.0.1g.tar.gz cd openssl-1.0.1g ./config --prefix=/usr/local/ssl shared zlib-dynamic enable-camellia -DOPENSSL_NO_HEARTBEATS #添加 -DOPENSSL_NO_HEARTBEATS 选项 make make install openssl version mv /usr/bin/openssl /usr/bin/openssl.old mv /usr/include/openssl /usr/include/opensslold ln -s /usr/local/ssl/bin/openssl /usr/bin/openssl ln -s /usr/local/ssl/include/openssl/ /usr/include/openssl echo "/usr/local/ssl/lib/" >> /etc/ld.so.conf ldconfig -v|grep ssl openssl version升级后截图

openssl version -a

为什么升级openssh,因为用xshell或者SecureCRT等终端连接服务器是用ssh,现在查看ssh所用openssl所用的版本还是这样的
[root@localhost ~]# ssh -V OpenSSH_5.3p1, OpenSSL 1.0.0-fips 29 Mar 2010验证:
# rpm -qa openssl
openssl-1.0.1e-16.el6_5.14.x86_64
# rpm -q --changelog openssl-1.0.1e | grep CVE-2014-0160
- fix CVE-2014-0160 - information disclosure in TLS heartbeat extension
说明漏洞已经修复
升级 openssh (编译时候请按文章最下面,添加
--
with
-kerberos5=/usr/lib64/libkrb5.so参数编译,不然会出现下面的问题)
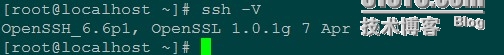
wget http://mirror.internode.on.net/pub/OpenBSD/OpenSSH/portable/openssh-6.6p1.tar.gz yum install pam* tar -xzf openssh-6.6p1.tar.gz cd openssh-6.6p1 ./configure --prefix=/usr --sysconfdir=/etc/ssh --with-pam --with-zlib --with-ssl-dir=/usr/local/ssl --with-md5-passwords --mandir=/usr/share/man make make install ssh -V OpenSSH_6.6p1, OpenSSL 1.0.1g 7 Apr 2014 service sshd restart 停止 sshd: [确定] 正在启动 sshd: [确定]升级完成后打开新的终端连接

升级完成
当执行service sshd restart 的时候有错误提示

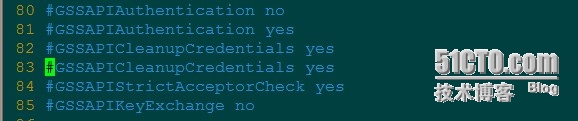
vim /etc/ssh/sshd_config 把81和83行注释

再执行就没问题了
service sshd restart Stopping sshd: [ OK ] Starting sshd: [ OK ]
附:
Unsupported option GSSAPIAuthentication 和 Unsupported option GSSAPICleanupCredentials
这两个认证机制的解决方法:
service sshd restart Stopping sshd: [ OK ] Starting sshd: /etc/ssh/sshd_config line 81: Unsupported option GSSAPIAuthentication /etc/ssh/sshd_config line 83: Unsupported option GSSAPICleanupCredentials [ OK ]在编译
openssh-
6
.6p1的时候把kerberos5的选项指定,即添加选项--[code]with
-kerberos5=/usr/lib64/libkrb5.so就不会出现问题[/code]
[root@localhost openssh-6.6p1]# ./configure --prefix=/usr --sysconfdir=/etc/ssh --with-pam --with-zlib --with-ssl-dir=/usr/local/ssl --with-md5-passwords --mandir=/usr/share/man --with-kerberos5=/usr/lib64/libkrb5.so下面是sshd_config的配置文件,认证不受影响的,重启sshd服务也没问题
vim /etc/ssh/sshd_config

上述的代码
升级前关闭selinux升级ssl,sshyum install zlib zlib-devel -y
yum install krb5-devel.x86_64 -y
wget http://www.openssl.org/source/openssl-1.0.1g.tar.gztar -xzf openssl-1.0.1g.tar.gzcd openssl-1.0.1g./config --prefix=/usr/local/ssl shared zlib-dynamic enable-camellia -DOPENSSL_NO_HEARTBEATS makemake installopenssl versionmv /usr/bin/openssl /usr/bin/openssl.oldmv /usr/include/openssl /usr/include/openssloldln -s /usr/local/ssl/bin/openssl /usr/bin/opensslln -s /usr/local/ssl/include/openssl/ /usr/include/opensslecho "/usr/local/ssl/lib/" >>/etc/ld.so.confldconfig -v|grep sslopenssl versioncd ..wget http://mirror.internode.on.net/pub/OpenBSD/OpenSSH/portable/openssh-6.6p1.tar.gzyum install pam* -ytar -xzf openssh-6.6p1.tar.gzcd openssh-6.6p1./configure --prefix=/usr --sysconfdir=/etc/ssh --with-pam --with-zlib --with-ssl-dir=/usr/local/ssl --with-md5-passwords --mandir=/usr/share/man --with-kerberos5=/usr/lib64/libkrb5.somakemake installssh -Vcd ..
相关文章推荐
- OpenSSL漏洞升级修复
- Openssl漏洞问题升级为1.0.1g(OpenSSL 漏洞版本v1.0.1到1.0.1f)
- 升级openssl包,修复心脏出血漏洞 推荐
- 升级openssl版本修复高危漏洞——“OpenSSL红色警戒”漏洞
- 记服务器升级openssl-1.0.1g之安全漏洞Heartbleed
- 本周最大的狗血事件是升级openssl 0.9.8v然后又说这个版本没修复漏洞要升级到到到到0.9.8w.
- 升级你的OpenSSL吧 (“heartbleed”漏洞修复方案)
- 修复Strtus远程命令执行漏洞 : Strtus 2.2.3 升级到 Strtus 2.3.24
- openssl 升级到1.0.1g
- Debian7离线升级bash漏洞—再修复方法
- 汉澳sinox不受openssl心血漏洞影响并分析修复其漏洞代码
- openssl 升级为1.0.1g
- 【openssl】openssl 升级到1.0.1g
- OpenSSL漏洞波及电商和网银 专家提醒及时修复
- struts修复GetShell漏洞,将2.1.8.1升级至2.3.28
- 升级OpenSSL修复高危漏洞
- 关于centos7和centos6中平滑升级nginx到新版本v1.12.1修复nginx最新漏洞CVE-2017-7529的解决方案
- openssl升级到1.0.1g的过程
