PingingLab传世经典系列《CCNA完全配置宝典》-5.5 自反ACL
2013-08-10 12:23
477 查看
5.5 自反ACL
实验目的:
1、掌握自反ACL的基本编写。
2、理解自反ACL的基本特性。
实验拓扑:
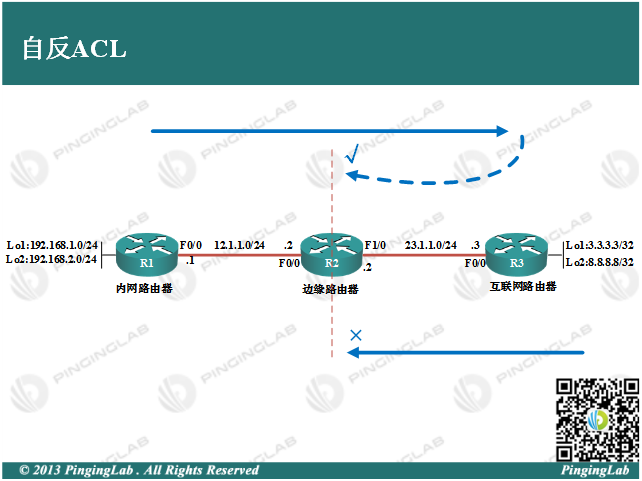
实验步骤:1、依据图中拓扑,配置各个路由器的IP地址,并部署静态路由保证全网连通,配置如下:R1上R1(config)#ip route 23.1.1.0 255.255.255.0 12.1.1.2R1(config)#ip route 3.3.3.3 255.255.255.255 12.1.1.2R1(config)#ip route 8.8.8.8 255.255.255.255 12.1.1.2R2上R2(config)#ip route 192.168.1.0 255.255.255.0 12.1.1.1R2(config)#ip route 192.168.2.0 255.255.255.0 12.1.1.1R2(config)#ip route 3.3.3.3 255.255.255.255 23.1.1.3R2(config)#ip route 8.8.8.8 255.255.255.255 23.1.1.3R3上R3(config)#ip route 12.1.1.0 255.255.255.0 23.1.1.2R3(config)#ip route 192.168.1.0 255.255.255.0 23.1.1.2R3(config)#ip route 192.168.2.0 255.255.255.0 23.1.1.2测试连通性,如下:R1#ping 3.3.3.3 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 40/40/40 msR1#ping 8.8.8.8 source 192.168.2.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:Packet sent with a source address of 192.168.2.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 36/43/56 ms可以看到,内网与外网通信没有问题。2、在R2上部署自反ACL,使得内网所有设备可以访问外网,而外网主动发起的流量都拒绝,配置如下:①允许内网访问外网流量,并执行流量“记录”R2(config)#ip access-list extended OUTBOUNDR2(config-ext-nacl)#permit ip any any reflect PLR2(config-ext-nacl)#exitR2(config)#ip access-list extended INBOUND②拒绝外网访问内网,除了被”记录“的流量R2(config-ext-nacl)#evaluate PLR2(config-ext-nacl)#deny ip any anyR2(config-ext-nacl)#EXIT③接口下调用ACLR2(config)#int f1/0R2(config-if)#ip access-group OUTBOUND outR2(config-if)#ip access-group INBOUND inR2(config-if)#exit3、测试自反ACL,如下:在R2上查看ACL状态R2#show ip access-listsExtended IP access list INBOUND 10 evaluate PL 20 deny ip any anyExtended IP access list OUTBOUND 10 permit ip any any reflect PLReflexive IP access list PL让R1访问外网R1#ping 8.8.8.8 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 60/63/64 ms再次在R2上查看ACL状态R2#show ip access-listsExtended IP access list INBOUND 10 evaluate PL 20 deny ip any anyExtended IP access list OUTBOUND 10 permit ip any any reflect PL (10 matches)Reflexive IP access list PL permit icmp host 8.8.8.8 host 192.168.1.1 (20 matches) (time left 298)从上面可以看出,当内网访问外网时,由于实现了流量“记录”,自反ACL自动生成一条反向ACL,用于放开内网到外网的返回流量。而没有被记录的或者外网主动发起的流量,则被拒绝,如下:R3#ping 192.168.1.1 source 3.3.3.3Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:Packet sent with a source address of 3.3.3.3UUUUUSuccess rate is 0 percent (0/5)通过这个实验可以看到,自反ACL可以实现更加安全的访问控制,某种程度上可以充当防火墙。此实验完成。==========================================PingingLab·高品质IT教育提供商CCIE 实验室·IT项目实战·高端人才定制深圳拼客信息科技有限公司·广州大学城外环西路站新浪微博:@拼客科技PingingLab @PingingLab-陈鑫杰PingingLab微信公众号:pinginglab PingingLab技术交流群:240920680

本文出自 “陈鑫杰讲网络” 博客,请务必保留此出处http://chenxinjie.blog.51cto.com/7749507/1274477
实验目的:
1、掌握自反ACL的基本编写。
2、理解自反ACL的基本特性。
实验拓扑:

实验步骤:1、依据图中拓扑,配置各个路由器的IP地址,并部署静态路由保证全网连通,配置如下:R1上R1(config)#ip route 23.1.1.0 255.255.255.0 12.1.1.2R1(config)#ip route 3.3.3.3 255.255.255.255 12.1.1.2R1(config)#ip route 8.8.8.8 255.255.255.255 12.1.1.2R2上R2(config)#ip route 192.168.1.0 255.255.255.0 12.1.1.1R2(config)#ip route 192.168.2.0 255.255.255.0 12.1.1.1R2(config)#ip route 3.3.3.3 255.255.255.255 23.1.1.3R2(config)#ip route 8.8.8.8 255.255.255.255 23.1.1.3R3上R3(config)#ip route 12.1.1.0 255.255.255.0 23.1.1.2R3(config)#ip route 192.168.1.0 255.255.255.0 23.1.1.2R3(config)#ip route 192.168.2.0 255.255.255.0 23.1.1.2测试连通性,如下:R1#ping 3.3.3.3 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 3.3.3.3, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 40/40/40 msR1#ping 8.8.8.8 source 192.168.2.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:Packet sent with a source address of 192.168.2.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 36/43/56 ms可以看到,内网与外网通信没有问题。2、在R2上部署自反ACL,使得内网所有设备可以访问外网,而外网主动发起的流量都拒绝,配置如下:①允许内网访问外网流量,并执行流量“记录”R2(config)#ip access-list extended OUTBOUNDR2(config-ext-nacl)#permit ip any any reflect PLR2(config-ext-nacl)#exitR2(config)#ip access-list extended INBOUND②拒绝外网访问内网,除了被”记录“的流量R2(config-ext-nacl)#evaluate PLR2(config-ext-nacl)#deny ip any anyR2(config-ext-nacl)#EXIT③接口下调用ACLR2(config)#int f1/0R2(config-if)#ip access-group OUTBOUND outR2(config-if)#ip access-group INBOUND inR2(config-if)#exit3、测试自反ACL,如下:在R2上查看ACL状态R2#show ip access-listsExtended IP access list INBOUND 10 evaluate PL 20 deny ip any anyExtended IP access list OUTBOUND 10 permit ip any any reflect PLReflexive IP access list PL让R1访问外网R1#ping 8.8.8.8 source 192.168.1.1Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:Packet sent with a source address of 192.168.1.1!!!!!Success rate is 100 percent (5/5), round-trip min/avg/max = 60/63/64 ms再次在R2上查看ACL状态R2#show ip access-listsExtended IP access list INBOUND 10 evaluate PL 20 deny ip any anyExtended IP access list OUTBOUND 10 permit ip any any reflect PL (10 matches)Reflexive IP access list PL permit icmp host 8.8.8.8 host 192.168.1.1 (20 matches) (time left 298)从上面可以看出,当内网访问外网时,由于实现了流量“记录”,自反ACL自动生成一条反向ACL,用于放开内网到外网的返回流量。而没有被记录的或者外网主动发起的流量,则被拒绝,如下:R3#ping 192.168.1.1 source 3.3.3.3Type escape sequence to abort.Sending 5, 100-byte ICMP Echos to 192.168.1.1, timeout is 2 seconds:Packet sent with a source address of 3.3.3.3UUUUUSuccess rate is 0 percent (0/5)通过这个实验可以看到,自反ACL可以实现更加安全的访问控制,某种程度上可以充当防火墙。此实验完成。==========================================PingingLab·高品质IT教育提供商CCIE 实验室·IT项目实战·高端人才定制深圳拼客信息科技有限公司·广州大学城外环西路站新浪微博:@拼客科技PingingLab @PingingLab-陈鑫杰PingingLab微信公众号:pinginglab PingingLab技术交流群:240920680

本文出自 “陈鑫杰讲网络” 博客,请务必保留此出处http://chenxinjie.blog.51cto.com/7749507/1274477
相关文章推荐
- PingingLab传世经典系列《CCNA完全配置宝典》-1.5 配置管理
- PingingLab传世经典系列《CCNA完全配置宝典》-4.9 Frame-Relay&EIGRP
- PingingLab传世经典系列《CCNA完全配置宝典》-1.6 密码管理
- PingingLab传世经典系列《CCNA完全配置宝典》-2.7 EIGRP基本配置
- PingingLab传世经典系列《CCNA完全配置宝典》-4.2 PPP基本配置
- PingingLab传世经典系列《CCNA完全配置宝典》-5.1 编号标准ACL
- PingingLab传世经典系列《CCNA完全配置宝典》-2.3 浮动路由
- PingingLab传世经典系列《CCNA完全配置宝典》-2.8 EIGRP路由汇总
- PingingLab传世经典系列《CCNA完全配置宝典》-5.2 编号拓展ACL
- PingingLab传世经典系列《CCNA完全配置宝典》-1.7 密码恢复
- PingingLab传世经典系列《CCNA完全配置宝典》-2.4 RIPv1基本配置
- PingingLab传世经典系列《CCNA完全配置宝典》-3.10 PVST基本配置
- PingingLab传世经典系列《CCNA完全配置宝典》-4.3 PPP PAP认证
- PingingLab传世经典系列《CCNA完全配置宝典》-5.3 命名ACL
- PingingLab传世经典系列《CCNA完全配置宝典》-4.4 PPP CHAP认证
- PingingLab传世经典系列《CCNA完全配置宝典》-5.4 时间ACL
- PingingLab传世经典系列《CCNA完全配置宝典》-3.3 Trunk基础配置
- PingingLab传世经典系列《CCNA完全配置宝典》-3.11 单臂路由
- PingingLab传世经典系列《CCNA完全配置宝典》-4.5 PPP Multilink
- PingingLab传世经典系列《CCNA完全配置宝典》-2.5 RIPv2基本配置
