基于openssl的https服务的配置
2016-08-06 21:32
393 查看
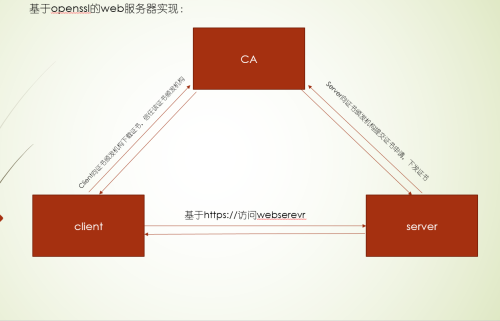
openssl实现私有CA,并配置基于openssl的https服务的配置,原理如下图
在CA服务器上实现私有CA步骤如下;1、生成一对密钥2.生成自签证书基本的配置如下代码;
将CA服务器上的cakey.pem文件下载到windows客户端上,修改文件名后缀为crt(cakey.crt),双击此文件,安装信任该证书颁发机构,具体步骤;
安装证书-->下一步-->选择将证书放入下列存储-->浏览-->选择受信任的根证书颁发机构-->完成;
通过web页面访问,效果如下;
部署完成。

在CA服务器上实现私有CA步骤如下;1、生成一对密钥2.生成自签证书基本的配置如下代码;
[root@CA CA]# pwd /etc/pki/CA [root@CA CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) [root@CA CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [NEIMENGGU]: Locality Name (eg, city) [Huhhot]: Organization Name (eg, company) [EDU]: Organizational Unit Name (eg, section) [Tech]: Common Name (eg, your name or your server's hostname) []:ca.edu.cn Email Address []:caadmin@edu.cn [root@CA CA]# touch index.txt [root@CA CA]# touch serial [root@CA CA]# echo 01 > serial [root@CA CA]# ls cacert.pem certs crl index.txt newcerts private serialwebserver服务器上的证书生成步骤;
[root@www ~]# cd /etc/httpd/ [root@www httpd]# mkdir ssl [root@www httpd]# cd ssl/ [root@www ssl]# pwd /etc/httpd/ssl [root@www ssl]# (umask 077; openssl genrsa -out httpd.key 1024) Generating RSA private key, 1024 bit long modulus ..........................++++++ .......++++++ e is 65537 (0x10001) [root@www ssl]# ll total 4 -rw-------. 1 root root 887 Aug 6 23:46 httpd.keywebserver生成证书签署请求;
[root@www ssl]# openssl req -new -key httpd.key -out httpd.csr You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter '.', the field will be left blank. ----- Country Name (2 letter code) [XX]:CN State or Province Name (full name) []:NEIMENGGU Locality Name (eg, city) [Default City]:Huhhot Organization Name (eg, company) [Default Company Ltd]:EDU Organizational Unit Name (eg, section) []:Tech Common Name (eg, your name or your server's hostname) []:www.edu.cn Email Address []: Please enter the following 'extra' attributes to be sent with your certificate request A challenge password []: An optional company name []:将申请证书发送打CA服务器上,让CA服务器来完成证书的签署
[root@CA CA]# scp root@192.168.0.107:/etc/httpd/ssl/httpd.csr ./certs/ root@192.168.0.107's password: httpd.csr 100% 647 0.6KB/s 00:00 [root@CA CA]# ll ./certs/ total 4 -rw-r--r-- 1 root root 647 Aug 5 21:39 httpd.csrCA服务器来完成证书的签署
[root@CA CA]# openssl ca -in ./certs/httpd.csr -out ./certs/httpd.crt -days 365 Using configuration from /etc/pki/tls/openssl.cnf Check that the request matches the signature Signature ok Certificate Details: Serial Number: 1 (0x1) Validity Not Before: Aug 5 13:45:06 2016 GMT Not After : Aug 5 13:45:06 2017 GMT Subject: countryName = CN stateOrProvinceName = NEIMENGGU organizationName = EDU organizationalUnitName = Tech commonName = www.edu.cn X509v3 extensions: X509v3 Basic Constraints: CA:FALSE Netscape Comment: OpenSSL Generated Certificate X509v3 Subject Key Identifier: 12:2C:ED:3F:F1:FA:54:FB:71:03:79:03:81:77:2D:A6:33:EF:8E:8F X509v3 Authority Key Identifier: keyid:1B:1E:92:D1:DD:79:A6:68:19:91:5F:08:04:FF:7C:25:73:E4:BC:82 Certificate is to be certified until Aug 5 13:45:06 2017 GMT (365 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated [root@CA CA]# ll ./certs/ total 4 -rw-r--r-- 1 root root 0 Aug 5 21:43 httpd.crt -rw-r--r-- 1 root root 647 Aug 5 21:39 httpd.csr将证书文件发送给请求端;
[root@CA CA]# scp ./certs/httpd.crt root@192.168.0.107:/etc/httpd/ssl/ root@192.168.0.107's password: httpd.crt 100% 3754 3.7KB/s 00:00在webserver服务器上安装支持ssl的模块;
# yum install -y mod_ssl配置ssl.conf配置文件,修改如下行;
[root@www ssl]# vim /etc/httpd/conf.d/ssl.conf 107 SSLCertificateFile /etc/httpd/ssl/httpd.crt 114 SSLCertificateKeyFile /etc/httpd/ssl/httpd.key启动apache服务
[root@www ssl]# service httpd start在windows客户端通过如下方式安装信任CA证书颁发机构;
将CA服务器上的cakey.pem文件下载到windows客户端上,修改文件名后缀为crt(cakey.crt),双击此文件,安装信任该证书颁发机构,具体步骤;
安装证书-->下一步-->选择将证书放入下列存储-->浏览-->选择受信任的根证书颁发机构-->完成;
通过web页面访问,效果如下;

部署完成。
相关文章推荐
- 基于openssl的https服务配置
- 基于openssl 的https服务配置
- 基于openssl的https服务的配置
- Linux 基于openssl的https服务配置
- 基于openssl的https服务配置
- 基于openssl的https服务配置
- 安装基于openssl的https服务配置
- 基于openssl搭建https服务
- RedHat 学习笔记 基于ssl的httpd服务配置 (openssl创建CA)
- Nginx + Tomcat + Openssl 配置https的web服务
- 基于IIS配置Https服务
- nginx系列-05-基于openSSL配置HTTPS
- Openssl:构建CA的过程并实现web服务基于https访问的网络架构
- rhel5.5_Apache配置openssl支持https服务
- httpd系列-04-基于openSSL配置HTTPS
- Openssl:构建CA的过程并实现web服务基于https访问的网络架构
- 基于windows sever 2008系统平台配置DNS服务--配置委派
- 在windows下配置基于apache的svn(带openssl0.9.8)
- xp下使用Openssl来制作证书,在IIS中配置Https笔记
