https的博客作业
2016-07-15 08:49
309 查看
博客作业:分别使用httpd-2.2和httpd-2.4实现
1、建立httpd服务,要求:
(1) 提供两个基于名称的虚拟主机www1, www2;有单独的错误日志和访问日志;
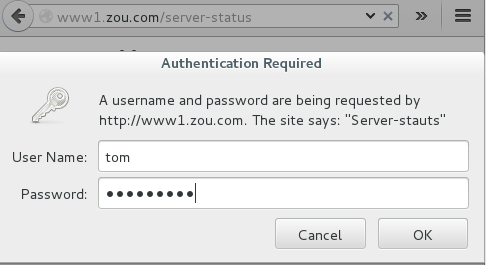
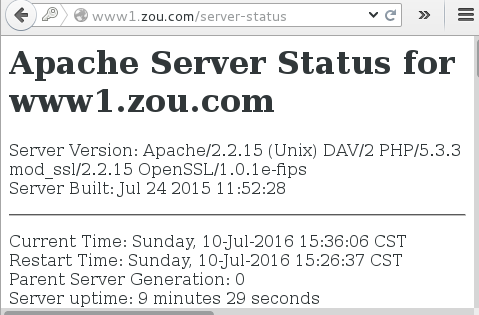
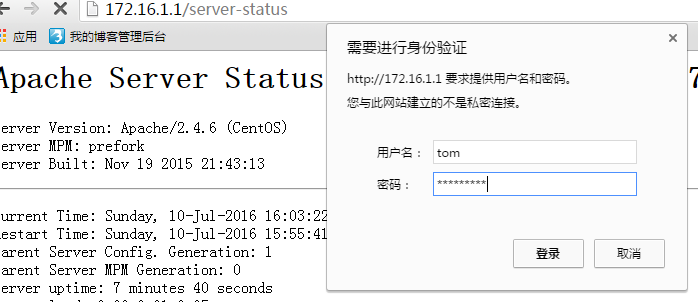
(2) 通过www1的/server-status提供状态信息,且仅允许tom用户访问;
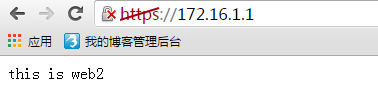
(3) www2不允许192.168.0.0/24网络中任意主机访问;
2、为上面的第2个虚拟主机提供https服务;
前提准备:
172.16.1.1测试httpd-2.4,这是centos7系统
172.16.1.2测试httpd-2.2,这是centos6系统
172.16.1.3作为CA服务器,为其他两个主机派发证书
暂时关闭selinux和iptables
生成私钥CA服务器自己的私钥,准备给自己做个根证书
##因为这里是建立私有CA,同一个机构,国家,省,组织 ,所以为了后续给自己签证方便,这里需要修改
生成自签证书(根CA)
准备好做CA服务器的数据库等文件
httpd2.2基础上面(Centos6)
生成自己的私钥和证书文件,传送给根服务器验证
跟服务器签发证书,并把证书发送回来
修改主配置文件支持基于FQDN的主机名
配置httpd支持ssl
为虚部主机2进程配置设置
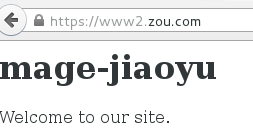
为虚拟主机1进行配置设置
为tom用户认证做准备
重启服务
~]# service httpd restart
httpd2.4(Centos7版本上)
生成自己的私钥和证书文件,传送给根服务器验证
[root@zzy www2]# mkdir /etc/httpd/conf/.ssh[root@zzy www2]# cd /etc/httpd/conf/.ssh[root@zzy .ssh]# (umask 077;openssl genrsa 4096 > http.key)[root@zzy .ssh]# openssl req -new -key http.key -out httpd.csr Common Name (eg, your name or your server's hostname) []:www2.zou.com[root@zzy .ssh]# scp httpd.csr root@172.16.1.3:/mnt跟服务器签发证书,并把证书发送回来
[root@haizei ~]# openssl ca -in /mnt/httpd.csr -out /etc/pki/CA/certs/httpd002.crt[root@haizei ~]# scp /etc/pki/CA/certs/httpd002.crt root@172.16.1.1:/etc/httpd/conf/.ssh回到web服务器上面来
[root@zzy ~]# cd /etc/httpd/conf/.ssh;cp httpd002.crt httpd.crt
安装支持ssl的http模块
[root@zzy ~]# yum install mod_ssl -y
配置虚拟主机1
[root@zzy ~]# vim /etc/httpd/conf.d/ssl.conf
设置www1的虚拟主机
新建认证登录用户tom
[root@zzy vhosts]# htpasswd -c -m /etc/httpd/conf/.htpasswd tom
重新加载服务
[root@zzy .ssh]# systemctl reload httpd
1、建立httpd服务,要求:
(1) 提供两个基于名称的虚拟主机www1, www2;有单独的错误日志和访问日志;
(2) 通过www1的/server-status提供状态信息,且仅允许tom用户访问;
(3) www2不允许192.168.0.0/24网络中任意主机访问;
2、为上面的第2个虚拟主机提供https服务;
前提准备:
172.16.1.1测试httpd-2.4,这是centos7系统
172.16.1.2测试httpd-2.2,这是centos6系统
172.16.1.3作为CA服务器,为其他两个主机派发证书
暂时关闭selinux和iptables
生成私钥CA服务器自己的私钥,准备给自己做个根证书
| [root@haizei ~]# cd /etc/pki/CA[root@haizei CA]# (umask 077;openssl genrsa 2048 > private/cakey.pemcakey.pem为CA服务的自己的私钥 |
| [root@haizei CA]# vim /etc/pki/tls/openssl.cnfcountry Name_default = CNStateOrprovinceName_default = BeijingLocatityName_default = Shangdi0.organizationName_default = M19organizationUnitName = Jishu |
| [root@haizei CA]# openssl req -new -x509 /etc/pki/CA/private/cakey.pem -days 3650 -out /etc/pki/CA/cacert.pem Common Name (eg, your name or your server's hostname) []:haizei.zou.com 这里需要自己定义自己的主机名,最好与主机名或者可以解析的域名一致 |
| [root@haizei CA]# mkdir -p /etc/pki/CA/{certs,crl,newcerts} [root@haizei CA]# touch /etc/pki/CA/{serial,index.txt} [root@haizei CA]# echo 001 > /etc/pki/CA/serial |
生成自己的私钥和证书文件,传送给根服务器验证
| [root@zou www2]# mkdir /etc/httpd/conf/.ssh [root@zou www2]# cd /etc/httpd/conf/.ssh [root@zou .ssh]# (umask 077;openssl genrsa 4096 > http.key) [root@zou .ssh]# openssl req -new -key http.key -out httpd.csr |
| [root@haizei~]# openssl ca -in /tmp/httpd.csr -out /etc/pki/CA/certs/httpd.crt -days 365[root@haizei~]# scp /etc/pki/CA/certs/httpd.crt root@172.16.1.2:/etc/httpd/conf/.ssh |
| [root@zou ~]# vim /etc/httpd/conf/httpd.confNameVirtualHost 172.16.1.2:80 |
| ~]# yum -y install mod_ssl |
| [root@zou www2]# vim /etc/httpd/conf/ssl.conf<VirtualHost _default_:443> ServerName www2.zou.com DocumentRoot /data/vhosts/www2 ErrorLog logs/ssl_www2-error_log LogLevel warn TransferLog logs/ssl_www2_access_log SSLCertificateFile /etc/httpd/conf/.ssh/httpd.crt SSLCertificateKeyFile /etc/httpd/conf/.ssh/http.key </VirtualHost> <Directory /data/vhosts/www2> Options None AllowOverride None Order deny,allow Deny from 192.168.0.0/24 </Directory> |

为虚拟主机1进行配置设置
| [root@zou www2]# vim /etc/httpd/conf.d/www1.conf<VirtualHost 172.16.1.2:80> ServerName www1.zou.com DocumentRoot /data/vhosts/www1 ErrorLog logs/www1-error_log LogLevel warn CustomLog logs/www1-access_log combined <Directory /data/vhosts/www1> Options None AllowOverride None Order allow,deny Allow from all </Directory> </VirtualHost> <Location /server-status> SetHandler server-status Order deny,allow Allow from all AuthType Basic AuthName "Server-stauts" AuthBasicProvider file AuthUserFile "/etc/httpd/conf/.htpasswd" Require user tom </Location> |
| [root@zou www2]# htpasswd -c -m /etc/httpd/conf/.htpasswd tom |
~]# service httpd restart


httpd2.4(Centos7版本上)
生成自己的私钥和证书文件,传送给根服务器验证
[root@zzy www2]# mkdir /etc/httpd/conf/.ssh[root@zzy www2]# cd /etc/httpd/conf/.ssh[root@zzy .ssh]# (umask 077;openssl genrsa 4096 > http.key)[root@zzy .ssh]# openssl req -new -key http.key -out httpd.csr Common Name (eg, your name or your server's hostname) []:www2.zou.com[root@zzy .ssh]# scp httpd.csr root@172.16.1.3:/mnt跟服务器签发证书,并把证书发送回来
[root@haizei ~]# openssl ca -in /mnt/httpd.csr -out /etc/pki/CA/certs/httpd002.crt[root@haizei ~]# scp /etc/pki/CA/certs/httpd002.crt root@172.16.1.1:/etc/httpd/conf/.ssh回到web服务器上面来
[root@zzy ~]# cd /etc/httpd/conf/.ssh;cp httpd002.crt httpd.crt
安装支持ssl的http模块
[root@zzy ~]# yum install mod_ssl -y
配置虚拟主机1
[root@zzy ~]# vim /etc/httpd/conf.d/ssl.conf
| <VirtualHost _default_:443> ServerName www2.zou.com DocumentRoot /data/vhosts/www2 ErrorLog logs/ssl_www2-error_log LogLevel warn TransferLog logs/ssl_www2_access_log SSLCertificateFile /etc/httpd/conf/.ssh/httpd.crt SSLCertificateKeyFile /etc/httpd/conf/.ssh/http.key</VirtualHost><Directory /data/vhosts/www2> <RequireAll> Require all granted Require not ip 192.168.0.0/24 </RequireAll></Directory> |

设置www1的虚拟主机
| [root@zzy ~]# vim /etc/httpd/conf.d/www1.conf <VirtualHost 172.16.1.1:80> ServerName www1.zou.com DocumentRoot /data/vhosts/www1 ErrorLog logs/www1-error_log LogLevel warn CustomLog logs/www1-access_log combined <Directory /data/vhosts/www1> <RequireAll> Require all granted </RequireAll> </Directory> </VirtualHost> <Location /server-status> SetHandler server-status <RequireAll> Require all granted AuthType Basic AuthName "Server-stauts" AuthBasicProvider file AuthUserFile "/etc/httpd/conf/.htpasswd" Require user tom </RequireAll> </Location> |
[root@zzy vhosts]# htpasswd -c -m /etc/httpd/conf/.htpasswd tom
重新加载服务
[root@zzy .ssh]# systemctl reload httpd

相关文章推荐
- Linux实现https方式访问站点
- HTTPS科普扫盲帖
- HTTPS的七个误解
- Centos 5下配置https服务器的方法
- apache https配置详细步骤讲解
- php使用curl打开https网站的方法
- win2003 https 网站的图文配置教程
- IIS7/IIS7.5 URL 重写 HTTP 重定向到 HTTPS的方法
- 安卓APP测试之使用Burp Suite实现HTTPS抓包方法
- android教程使用webview访问https的url处理sslerror示例
- PHP简单实现HTTP和HTTPS跨域共享session解决办法
- php之curl实现http与https请求的方法
- ASP.NET Core 1.0 部署 HTTPS(.NET Core 1.0)
- asp.net5中用户认证与授权(2)
- apache中使用mod_gnutls模块实现多个SSL站点配置(多个HTTPS协议的虚拟主机)
- Apache mod_rewrite实现HTTP和HTTPS重定向跳转
- 浅析Android系统中HTTPS通信的实现
- 在服务器上配置仅使用HTTPS通信的教程
- php curl 获取https请求的2种方法
