Google breakpad实战
2015-08-13 11:22
495 查看
使用Google breakpad,优点是跨平台,开源。原理图如下:
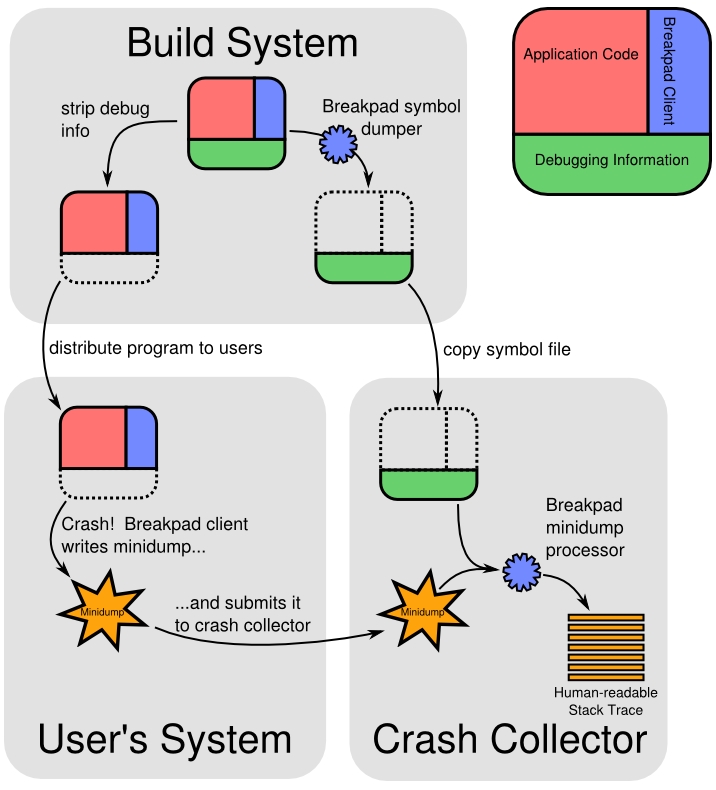
1.下载breakpad源码,build源码:
./configure LDFLAGS=-static-libstdc++
make
2.在App程序中调用异常处理构造函数,示例如下:
vi test.cpp
3.编译App程序时,需要链接breakpad_client.a静态库,而且需要加上-g选项。
g++ -g test.cpp -o test -L./src/client/linux/ -lbreakpad_client -I./src -static-libstdc++ -lpthread
4.使用breakpad的工具dump_syms导出符号信息到文件,并保存到具有特定的目录下:
#./src/tools/linux/dump_syms/dump_syms test > test.sym
#head -n1 test.sym
MODULE Linux x86_64 FDF0EFD5614DA1F9F64B0EBF23C3B4CC0 test
#mkdir -p ./symbols/test/FDF0EFD5614DA1F9F64B0EBF23C3B4CC0
#mv test.sym ./symbols/test/FDF0EFD5614DA1F9F64B0EBF23C3B4CC0
5.发布给用户使用的App程序,需要使用strip命令去掉符号信息:
strip test
6.运行的App如果发生异常,会在设置的目录下生成minidump文件,例如:
/tmp/5a880b31-606f-e4f6-11628802-48254e81.dmp
7.可以将产生的minidump文件发回到服务端,再加上之前产生的符号信息文件,就可以使用breakpad的工具查看堆栈信息了,如下:
[root@localhost google-breakpad]# ./src/processor/minidump_stackwalk /tmp/5a880b31-606f-e4f6-11628802-48254e81.dmp ./symbols/
......
2015-08-13 10:17:07: minidump_processor.cc:301: INFO: Processed /tmp/4e6858c1-bc7f-3d47-36fcaf47-42538c85.dmp
Operating system: Linux
0.0.0 Linux 2.6.18-406.el5 #1 SMP Tue Jun 2 17:25:57 EDT 2015 x86_64
CPU: amd64
family 6 model 60 stepping 3
4 CPUs
Crash reason: SIGSEGV
Crash address: 0x0
Process uptime: not available
Thread 0 (crashed)
0 test!crash [test.cpp : 9 + 0x4]
rax = 0x0000000000000000 rdx = 0x00000000006733e0
rcx = 0x0000000000000000 rbx = 0x000000331fe1cbc0
rsi = 0x0000000000000000 rdi = 0x00000000006733e0
rbp = 0x00007fff3ed76170 rsp = 0x00007fff3ed76170
r8 = 0x0000000000000000 r9 = 0x0000000000000000
r10 = 0x0000000000000000 r11 = 0x0000003320c0a150
r12 = 0x0000000000000000 r13 = 0x00007fff3ed76360
r14 = 0x0000000000000000 r15 = 0x0000000000000000
rip = 0x0000000000405b96
Found by: given as instruction pointer in context
1 test!main [test.cpp : 21 + 0x5]
rbx = 0x000000331fe1cbc0 rbp = 0x00007fff3ed76280
rsp = 0x00007fff3ed76180 r12 = 0x0000000000000000
r13 = 0x00007fff3ed76360 r14 = 0x0000000000000000
r15 = 0x0000000000000000 rip = 0x0000000000405c41
Found by: call frame info
2 libc-2.5.so + 0x1d9f4
rbx = 0x000000331fe1cbc0 rbp = 0x0000000000000000
rsp = 0x00007fff3ed76290 r12 = 0x0000000000000000
r13 = 0x00007fff3ed76360 r14 = 0x0000000000000000
r15 = 0x0000000000000000 rip = 0x000000332001d9f4
Found by: call frame info
3 test!crash [test.cpp : 10 + 0x2]
rsp = 0x00007fff3ed762b0 rip = 0x0000000000405b9e
Found by: stack scanning
4 0x331fe1cbc0
rbp = 0x0000000000405b9e rsp = 0x00007fff3ed762b8
rip = 0x000000331fe1cbc0
Found by: call frame info
Loaded modules:
0x00400000 - 0x0046efff test ??? (main)
0x331fc00000 - 0x331fc1bfff ld-2.5.so ???
0x3320000000 - 0x3320353fff libc-2.5.so ??? (WARNING: No symbols, libc-2.5.so, BF430E6A87B9E3605BB193A215F1C9470)
0x3320800000 - 0x3320a82fff libm-2.5.so ???
0x3320c00000 - 0x3320e17fff libpthread-2.5.so ???
0x3331600000 - 0x333180dfff libgcc_s-4.1.2-20080825.so.1 ???
0x7fff3edfd000 - 0x7fff3edfffff linux-gate.so ???
2015-08-13 10:17:07: minidump.cc:4169: INFO: Minidump closing minidump

1.下载breakpad源码,build源码:
./configure LDFLAGS=-static-libstdc++
make
2.在App程序中调用异常处理构造函数,示例如下:
vi test.cpp
#include "client/linux/handler/exception_handler.h"
#include <cstdlib>
using namespace std;
void crash()
{
volatile int* a = (int*)(NULL);
*a = 1;
}
int main(int argc, char* argv[])
{
google_breakpad::MinidumpDescriptor descriptor("/tmp");
google_breakpad::ExceptionHandler eh(descriptor,
NULL,
NULL,
NULL,
true,
-1);
crash();
return 0;
}3.编译App程序时,需要链接breakpad_client.a静态库,而且需要加上-g选项。
g++ -g test.cpp -o test -L./src/client/linux/ -lbreakpad_client -I./src -static-libstdc++ -lpthread
4.使用breakpad的工具dump_syms导出符号信息到文件,并保存到具有特定的目录下:
#./src/tools/linux/dump_syms/dump_syms test > test.sym
#head -n1 test.sym
MODULE Linux x86_64 FDF0EFD5614DA1F9F64B0EBF23C3B4CC0 test
#mkdir -p ./symbols/test/FDF0EFD5614DA1F9F64B0EBF23C3B4CC0
#mv test.sym ./symbols/test/FDF0EFD5614DA1F9F64B0EBF23C3B4CC0
5.发布给用户使用的App程序,需要使用strip命令去掉符号信息:
strip test
6.运行的App如果发生异常,会在设置的目录下生成minidump文件,例如:
/tmp/5a880b31-606f-e4f6-11628802-48254e81.dmp
7.可以将产生的minidump文件发回到服务端,再加上之前产生的符号信息文件,就可以使用breakpad的工具查看堆栈信息了,如下:
[root@localhost google-breakpad]# ./src/processor/minidump_stackwalk /tmp/5a880b31-606f-e4f6-11628802-48254e81.dmp ./symbols/
......
2015-08-13 10:17:07: minidump_processor.cc:301: INFO: Processed /tmp/4e6858c1-bc7f-3d47-36fcaf47-42538c85.dmp
Operating system: Linux
0.0.0 Linux 2.6.18-406.el5 #1 SMP Tue Jun 2 17:25:57 EDT 2015 x86_64
CPU: amd64
family 6 model 60 stepping 3
4 CPUs
Crash reason: SIGSEGV
Crash address: 0x0
Process uptime: not available
Thread 0 (crashed)
0 test!crash [test.cpp : 9 + 0x4]
rax = 0x0000000000000000 rdx = 0x00000000006733e0
rcx = 0x0000000000000000 rbx = 0x000000331fe1cbc0
rsi = 0x0000000000000000 rdi = 0x00000000006733e0
rbp = 0x00007fff3ed76170 rsp = 0x00007fff3ed76170
r8 = 0x0000000000000000 r9 = 0x0000000000000000
r10 = 0x0000000000000000 r11 = 0x0000003320c0a150
r12 = 0x0000000000000000 r13 = 0x00007fff3ed76360
r14 = 0x0000000000000000 r15 = 0x0000000000000000
rip = 0x0000000000405b96
Found by: given as instruction pointer in context
1 test!main [test.cpp : 21 + 0x5]
rbx = 0x000000331fe1cbc0 rbp = 0x00007fff3ed76280
rsp = 0x00007fff3ed76180 r12 = 0x0000000000000000
r13 = 0x00007fff3ed76360 r14 = 0x0000000000000000
r15 = 0x0000000000000000 rip = 0x0000000000405c41
Found by: call frame info
2 libc-2.5.so + 0x1d9f4
rbx = 0x000000331fe1cbc0 rbp = 0x0000000000000000
rsp = 0x00007fff3ed76290 r12 = 0x0000000000000000
r13 = 0x00007fff3ed76360 r14 = 0x0000000000000000
r15 = 0x0000000000000000 rip = 0x000000332001d9f4
Found by: call frame info
3 test!crash [test.cpp : 10 + 0x2]
rsp = 0x00007fff3ed762b0 rip = 0x0000000000405b9e
Found by: stack scanning
4 0x331fe1cbc0
rbp = 0x0000000000405b9e rsp = 0x00007fff3ed762b8
rip = 0x000000331fe1cbc0
Found by: call frame info
Loaded modules:
0x00400000 - 0x0046efff test ??? (main)
0x331fc00000 - 0x331fc1bfff ld-2.5.so ???
0x3320000000 - 0x3320353fff libc-2.5.so ??? (WARNING: No symbols, libc-2.5.so, BF430E6A87B9E3605BB193A215F1C9470)
0x3320800000 - 0x3320a82fff libm-2.5.so ???
0x3320c00000 - 0x3320e17fff libpthread-2.5.so ???
0x3331600000 - 0x333180dfff libgcc_s-4.1.2-20080825.so.1 ???
0x7fff3edfd000 - 0x7fff3edfffff linux-gate.so ???
2015-08-13 10:17:07: minidump.cc:4169: INFO: Minidump closing minidump
相关文章推荐
- linux偶发性崩溃的程序该怎么调试 coredump gdb
- google-breakpad在C++ 11下编译错误修改
- 关于coredump文件生成与查看
- coredump生成方法
- 【日志】2014_4_4 breakpad & extern & 图片相似度浅谈
- coredump的生成以及gdb查看
- 调试:coredump和linux下gdb单步调试、传递配置文件路径信息
- 小应用大智慧-Coredump故障分析
- google breakpad使用心得
- GDB实践:一场std::sort引发的coredump
- 详解coredump
- Linux Debugging(三): C++函数调用的参数传递方法总结(通过gdb+反汇编)
- Linux Debugging(五): coredump 分析入门
- 利用coredump查看函数调用
- corefile dump 分析11
- Esxi 主机提示“”未配置任何coredump目标。无法保存主机核心转储“”
- synopsys的license程序在Centos6.8下的问题
- Linux coredump解决流程
- gdb调试复习整理及coredump的设置与解析
- linux下设置coredump文件的开关和路径
