日至服务器的实现
2014-04-25 15:19
120 查看
loganalyzer是一个syslog或其他网络事件的web前端工具,提供简单易用的日志浏览、搜索、分析及图表显示功能,方便网络管理员、运维人员对各种系统日志的统一分析查看。通过它,可以方便的为网络部署专有的日志服务器。
以下部署过程在CentOS 6.4 下,loganalyzer主要搭配rsyslog及mysql使用。
服务器端:
1.[root@host2 ~]# yum install php php-mysql php-gd php-xml mysql mysql-server httpd mod_ssl rsyslog rsyslog-mysql
2 [root@host2 ~]# rpm -ql rsyslog-mysql
/lib/rsyslog/ommysql.so
/usr/share/doc/rsyslog-mysql-5.8.10
/usr/share/doc/rsyslog-mysql-5.8.10/createDB.sql
[[root@host2 ~]# service mysqld restart
Stopping mysqld: [ OK ]
Starting mysqld: [ OK ]
[root@host2 ~]# chkconfig mysqld on
[root@host2 ~]# mysql
root@host2 ~]# mysqladmin -u root -p password '111'
[Enter password:
[root@host2 ~]# mysql -u root -p
Enter password:
[root@host2 ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT icmp -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
关闭防火墙
[root@host2 ~]# service iptables stop
iptables: Setting chains to policy ACCEPT: filter [ OK ]
iptables: Flushing firewall rules: [ OK ]
iptables: Unloading modules: [ OK ]
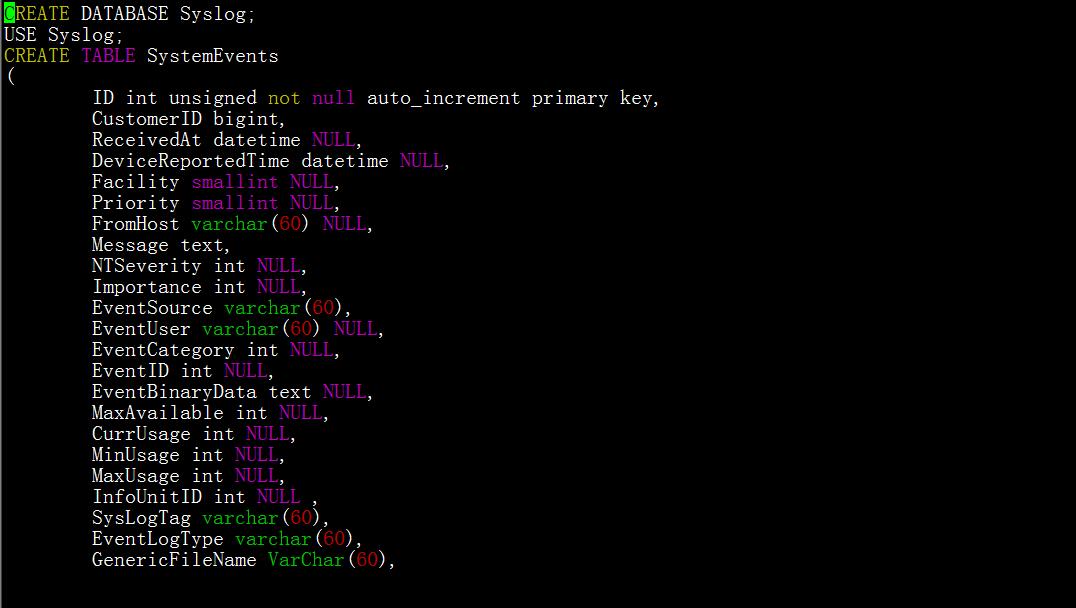
mysql> source /usr/share/doc/rsyslog-mysql-5.8.10/createDB.sql

mysql> show tables;
mysql> grant all privileges on Syslog.* to rsyslog@localhost identified by '111';
Query OK, 0 rows affected (0.00 sec)
mysql> flush privileges;
Query OK, 0 rows affected (0.00 sec)
[root@host2 ~]# vim /etc/rsyslog.conf
12 # Provides UDP syslog reception
13 $ModLoad imudp
14 $UDPServerRun 514
15
16 # Provides TCP syslog reception
17 $ModLoad imtcp
$InputTCPServerRun 514
# rsyslog v5 configuration file
重启rsyslog服务
[root@host2 ~]# service rsyslog restart
Shutting down system logger: [ OK ]
Starting system logger: [ OK ]
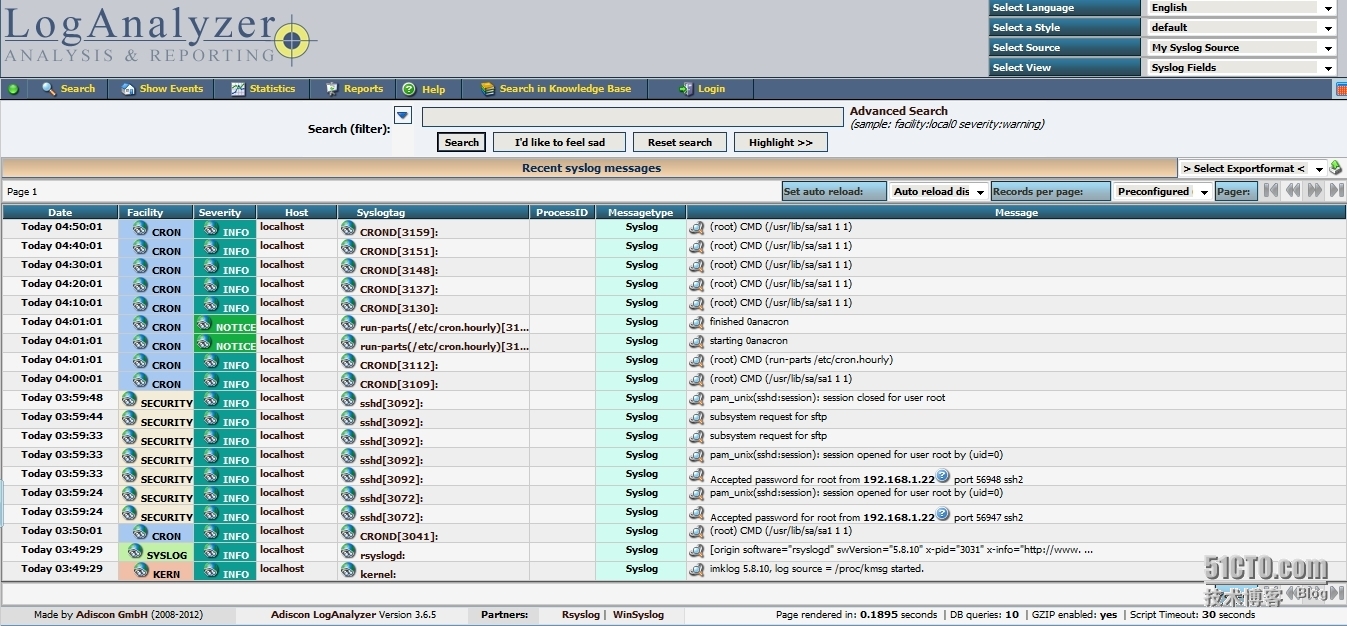
查看日至
[root@host2 ~]# tail -f /var/log/messages
[root@host2 ~]# cd /var/www/html
[root@host2 html]# ls
BitstreamVeraFonts classes details.php images js reportgenerator.php templates
admin convert.php doc include lang reports.php themes
asktheoracle.php cron export.php index.php loganalyzer search.php userchange.php
chartgenerator.php css favicon.ico install.php login.php statistics.php
[root@host2 html]# cd log
loganalyzer/ login.php
[root@host2 html]# cd loganalyzer/
[root@host2 loganalyzer]# ls
BitstreamVeraFonts classes details.php images js reports.php themes
admin convert.php doc include lang search.php userchange.php
asktheoracle.php cron export.php index.php login.php statistics.php
chartgenerator.php css favicon.ico install.php reportgenerator.php templates
[root@host2 loganalyzer]# ls
BitstreamVeraFonts classes css favicon.ico install.php reportgenerator.php templates
admin configure.sh details.php images js reports.php themes
asktheoracle.php convert.php doc include lang search.php userchange.php
chartgenerator.php cron export.php index.php login.php statistics.php
[root@host2 loganalyzer]# chmod a+x *.sh
[root@host2 loganalyzer]# ./configure.sh
[root@host2 loganalyzer]# ls
BitstreamVeraFonts classes cron export.php index.php login.php statistics.php
admin config.php css favicon.ico install.php reportgenerator.php templates
asktheoracle.php configure.sh details.php images js reports.php themes
chartgenerator.php convert.php doc include lang search.php userchange.php
[root@host2 loganalyzer]# vim configure.sh
[root@host2 loganalyzer]# chown -R daemon:daemon .
在你常用的浏览器的地址栏输入
http://192.168.10.10/loganalyzer
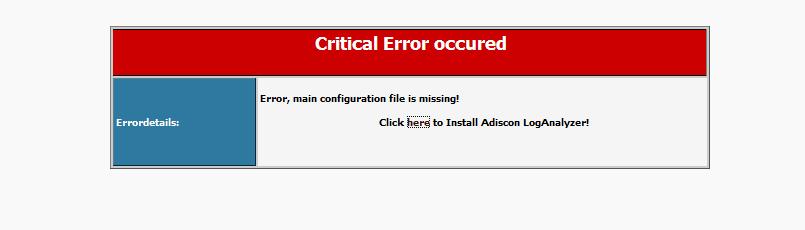
点击图中上完here,
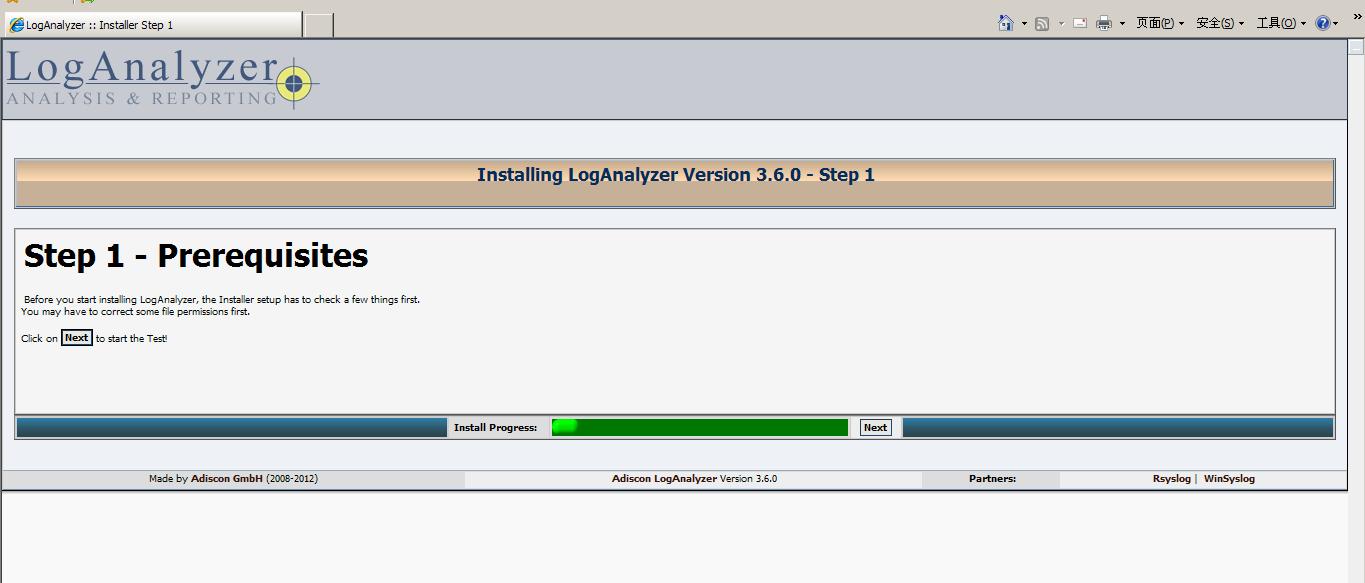
点击next
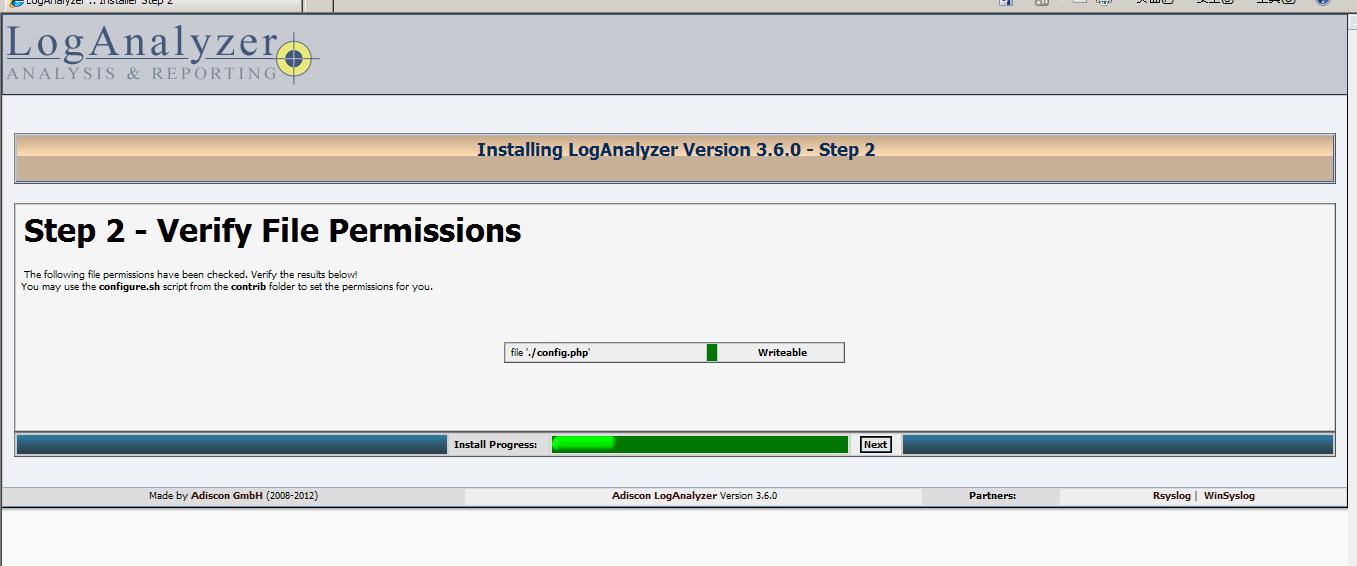
这里检测是否存在config.php文件,和config.php文件是否具有写权限
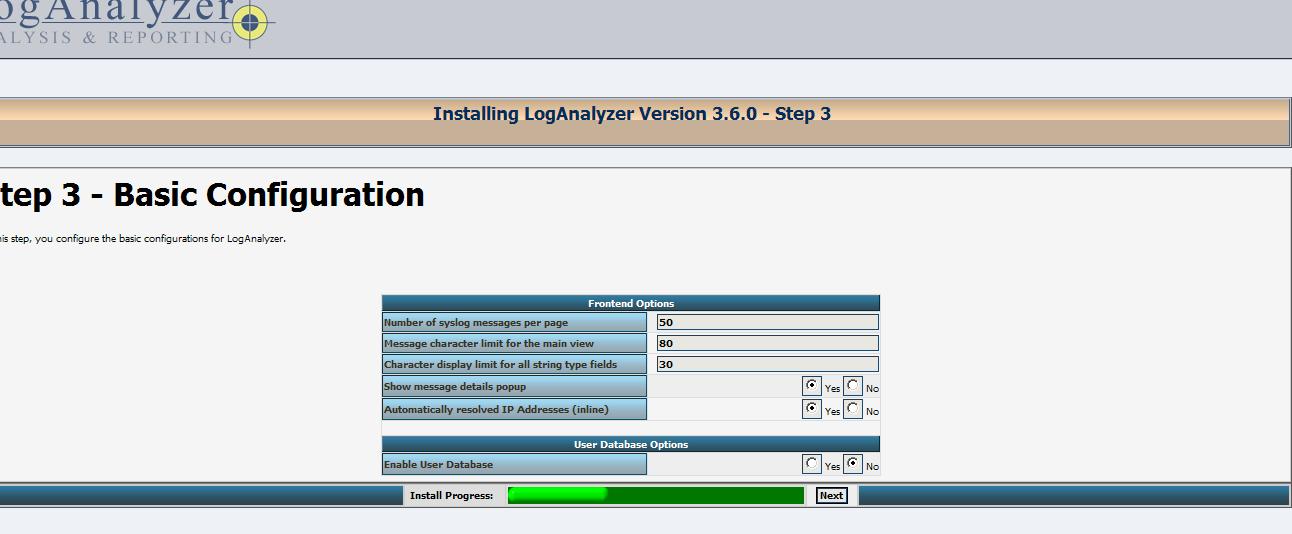
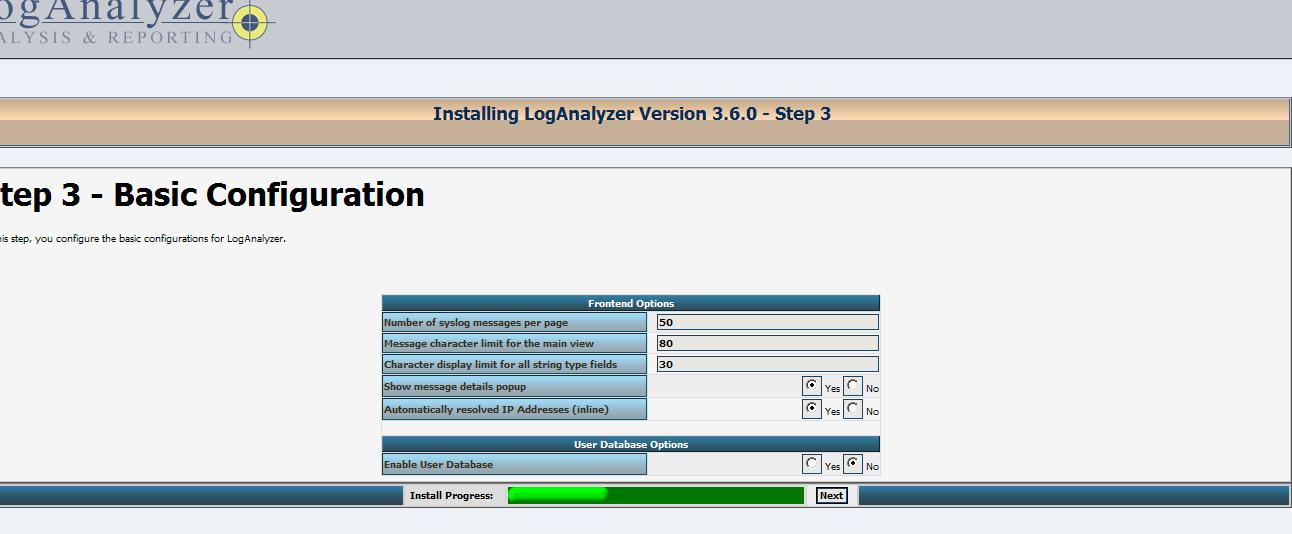
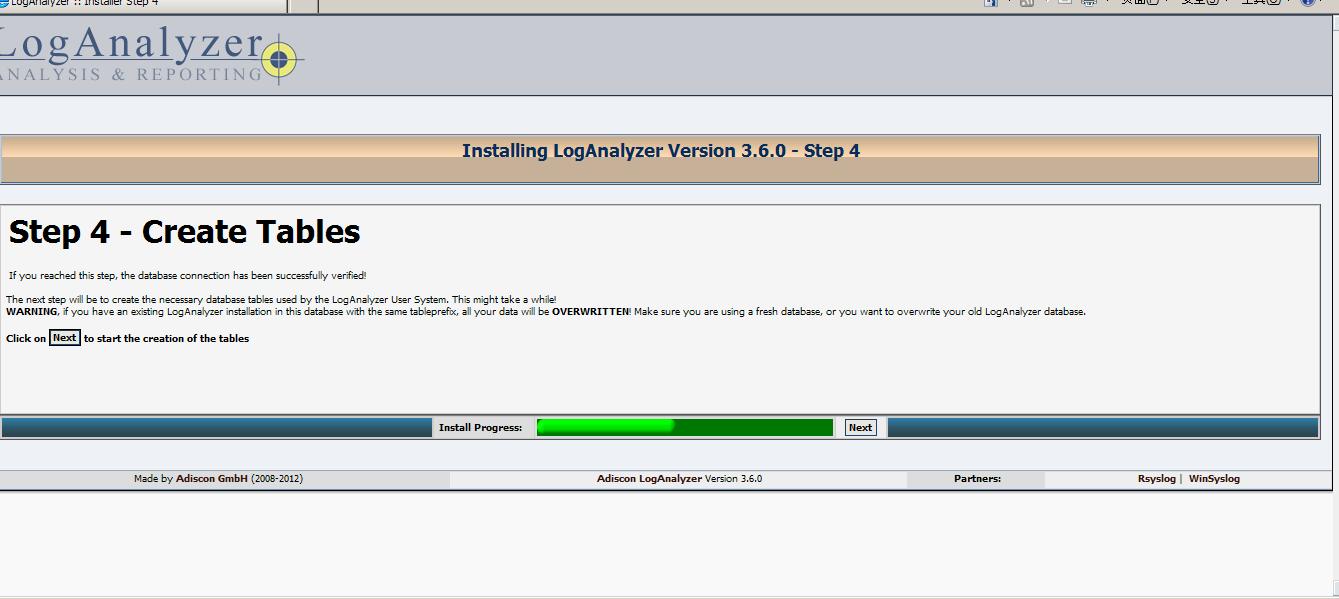
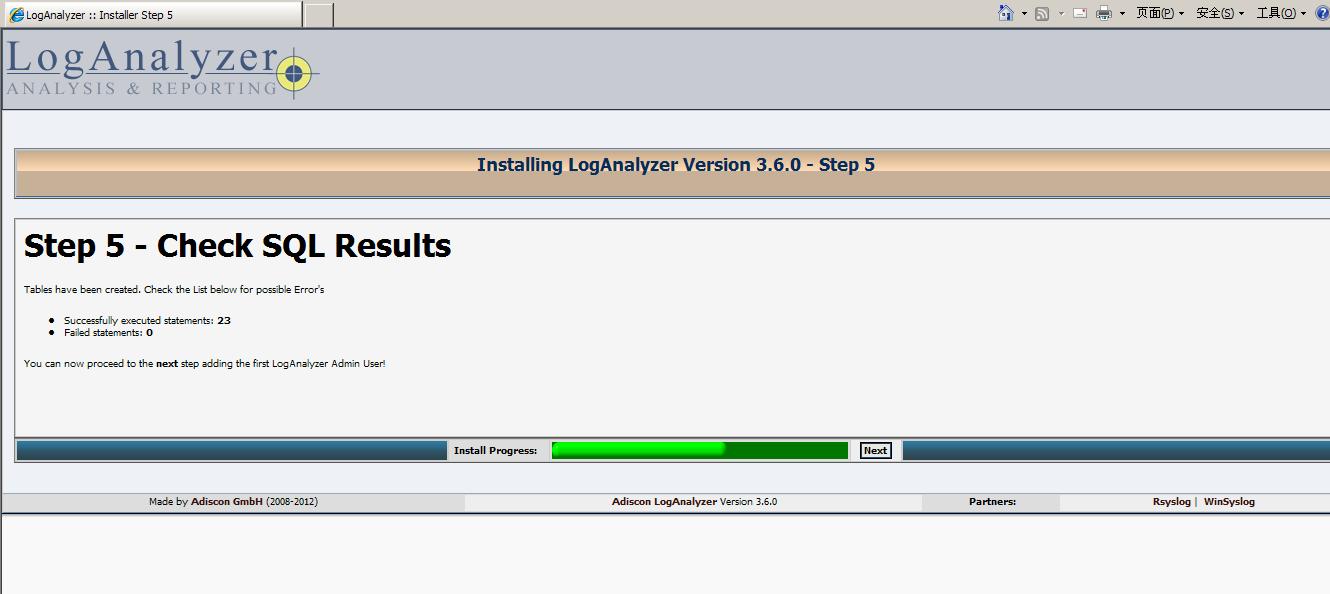
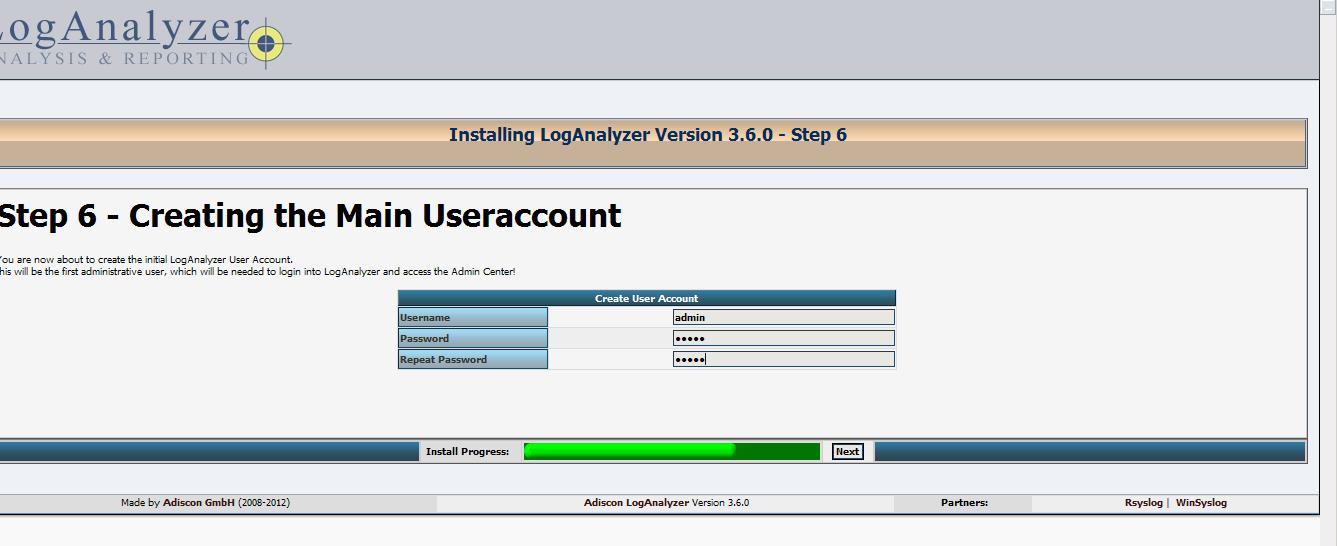
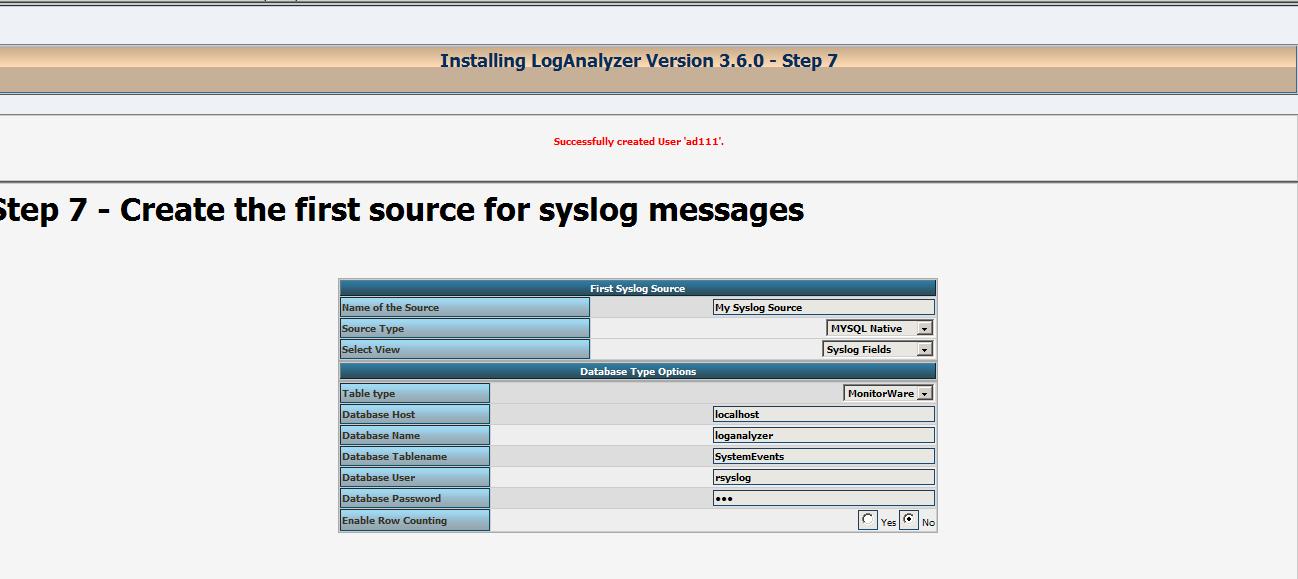
这一步将创建数据来源,指示的数据的存储位置
以下部署过程在CentOS 6.4 下,loganalyzer主要搭配rsyslog及mysql使用。
服务器端:
1.[root@host2 ~]# yum install php php-mysql php-gd php-xml mysql mysql-server httpd mod_ssl rsyslog rsyslog-mysql
2 [root@host2 ~]# rpm -ql rsyslog-mysql
/lib/rsyslog/ommysql.so
/usr/share/doc/rsyslog-mysql-5.8.10
/usr/share/doc/rsyslog-mysql-5.8.10/createDB.sql

[[root@host2 ~]# service mysqld restart
Stopping mysqld: [ OK ]
Starting mysqld: [ OK ]
[root@host2 ~]# chkconfig mysqld on
[root@host2 ~]# mysql

root@host2 ~]# mysqladmin -u root -p password '111'
[Enter password:
[root@host2 ~]# mysql -u root -p
Enter password:
[root@host2 ~]# iptables -L
Chain INPUT (policy ACCEPT)
target prot opt source destination
ACCEPT all -- anywhere anywhere state RELATED,ESTABLISHED
ACCEPT icmp -- anywhere anywhere
ACCEPT all -- anywhere anywhere
ACCEPT tcp -- anywhere anywhere state NEW tcp dpt:ssh
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain FORWARD (policy ACCEPT)
target prot opt source destination
REJECT all -- anywhere anywhere reject-with icmp-host-prohibited
Chain OUTPUT (policy ACCEPT)
target prot opt source destination
关闭防火墙
[root@host2 ~]# service iptables stop
iptables: Setting chains to policy ACCEPT: filter [ OK ]
iptables: Flushing firewall rules: [ OK ]
iptables: Unloading modules: [ OK ]
mysql> source /usr/share/doc/rsyslog-mysql-5.8.10/createDB.sql


mysql> show tables;
mysql> grant all privileges on Syslog.* to rsyslog@localhost identified by '111';
Query OK, 0 rows affected (0.00 sec)
mysql> flush privileges;
Query OK, 0 rows affected (0.00 sec)
[root@host2 ~]# vim /etc/rsyslog.conf
12 # Provides UDP syslog reception
13 $ModLoad imudp
14 $UDPServerRun 514
15
16 # Provides TCP syslog reception
17 $ModLoad imtcp
$InputTCPServerRun 514
# rsyslog v5 configuration file
重启rsyslog服务
[root@host2 ~]# service rsyslog restart
Shutting down system logger: [ OK ]
Starting system logger: [ OK ]
查看日至
[root@host2 ~]# tail -f /var/log/messages
[root@host2 ~]# cd /var/www/html
[root@host2 html]# ls
BitstreamVeraFonts classes details.php images js reportgenerator.php templates
admin convert.php doc include lang reports.php themes
asktheoracle.php cron export.php index.php loganalyzer search.php userchange.php
chartgenerator.php css favicon.ico install.php login.php statistics.php
[root@host2 html]# cd log
loganalyzer/ login.php
[root@host2 html]# cd loganalyzer/
[root@host2 loganalyzer]# ls
BitstreamVeraFonts classes details.php images js reports.php themes
admin convert.php doc include lang search.php userchange.php
asktheoracle.php cron export.php index.php login.php statistics.php
chartgenerator.php css favicon.ico install.php reportgenerator.php templates
[root@host2 loganalyzer]# ls
BitstreamVeraFonts classes css favicon.ico install.php reportgenerator.php templates
admin configure.sh details.php images js reports.php themes
asktheoracle.php convert.php doc include lang search.php userchange.php
chartgenerator.php cron export.php index.php login.php statistics.php
[root@host2 loganalyzer]# chmod a+x *.sh
[root@host2 loganalyzer]# ./configure.sh
[root@host2 loganalyzer]# ls
BitstreamVeraFonts classes cron export.php index.php login.php statistics.php
admin config.php css favicon.ico install.php reportgenerator.php templates
asktheoracle.php configure.sh details.php images js reports.php themes
chartgenerator.php convert.php doc include lang search.php userchange.php
[root@host2 loganalyzer]# vim configure.sh
[root@host2 loganalyzer]# chown -R daemon:daemon .
在你常用的浏览器的地址栏输入
http://192.168.10.10/loganalyzer

点击图中上完here,

点击next

这里检测是否存在config.php文件,和config.php文件是否具有写权限







这一步将创建数据来源,指示的数据的存储位置


相关文章推荐
- javaWeb服务器实现
- rSync服务器实现不同平台下备份数据
- Go语言异步服务器框架原理和实现
- 在linux开发板上实现一个音频服务器
- LINUX服务器的几种实现模型
- FTP服务器如何实现安全性
- Memcached 集群,客户端自动Hash到不同服务器的实现
- tftp--实现服务器与客户端的下载与上传
- juqery 实现 防止当前页面重复点击,以减轻服务器压力
- Select I/O模型来实现一个并发处理多个客户端的TCP服务器
- Ajax与服务器异步通信通信代码的实现
- 从服务器上边下载文件到客户机的实现.
- Windows 上静态编译 Libevent 2.0.10 并实现一个简单 HTTP 服务器
- php mailer类调用远程SMTP服务器发送邮件实现方法
- Sping+SpringMvc+Mybatis+OAuth2.0服务器与客户端实现(一)
- python用c/s实现服务器简单管理
- Netty实现服务器
- 内网穿透 Ngrok 不用买云服务器 虚拟主机也能实现个人服务器让外网访问
