【Firewall系列一】浅析基于区域的防火墙方案如何监测网络环境中内外流量与程序会话
2012-05-21 21:13
691 查看
【Firewall系列一】浅析基于区域的防火墙方案如何监测网络环境中
内外流量与程序会话
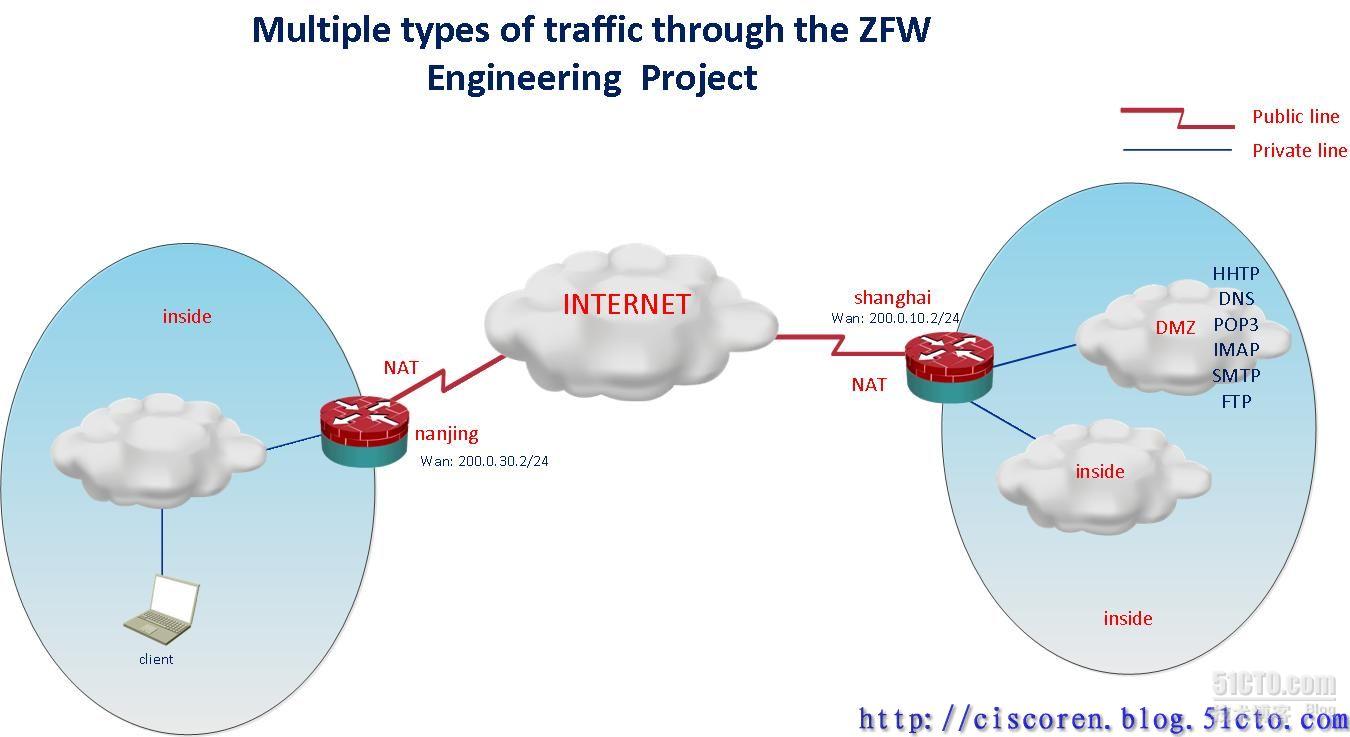
一、.背景描述
1.网络环境配置为中心站点shanghai与分支站点nanjing
2.中心站点拥有三个区域:外网区域、内网区域、DMZ区域
3.DMZ区域拥有企业内部服务器(DNS、WEB、Email、FTP)并且通过SSH和HTTPS加密方式进行远程管理
4.中心站点dmz地址池:172.18.100.0/24
中心站点inside地址池:172.18.101.0/24
二、基于区域的防火墙关键配置
如何放行out访问DMZ的正常访问流量?
关键在于如何定义什么是正常的访问流量。
DMZ内部部署有企业的服务器(DNS、WEB、Email、FTP)并且通过SSH和HTTPS加密方式进行远程管理,那么这些流量就是正常的流量,表示为:
http 80
https 443
ftp 20/21
pop3 110
imap 143
imap over ssl 993
ssh 22
smtp 25
命令表示为:
流量map匹配规则:
注意match-any与match-all的差异
配置policy-map,设定符合规则的流量将如何处置:
符合就放行,并进行检测会话
不符合就默认丢弃
三、配置NAT
只要是连接外网的网络设备,一般都要设定NAT,ip地址有限,都是money,性能与费用是要权衡的噢。。
根据DMZ提供的服务,配置如下:
关键服务都是必须设定为静态映射,其他内部访问外网使用动态映射即可。
看服务,看端口,这个要熟悉。
四、结果显示
好了,我们来看看详情
先看nat 转换
内部client ping 分支站点,成功启用动态映射
分支站点ssh管理,dzm区域设备,成功登陆
分支站点成功访问web服务器
分支站点成功通过https访问加密服务
现在来看防火墙监测的流量与程序会话数目
结语
1.基于区域的防火墙,默认是各区域之间各不相通的,所以必须明确配置策略用以放行所需流量,这是状态化防火墙,只要被监控放行流量,那么他也会放回流量。
2.本拓扑包含三个方向策略:
inside ——》DMZ
outside——》DMZ
DMZ——》outside
一般来说还得有inside——》outside
但是如果企业对于员工上网管理很严的话,那么这也是一个精细配置工作。
3.配置前一定要理清思路,哪些流量要放行,哪些流量要drop,NAT配置要精准,TCP还是udp,要查清楚,还有就是ftp,存在多个端口的服务
4.设定默认路由条目,必备的,你不可能对外网配个动态路由协议,与ISP起邻居,那样的话,神了^_^
5.最好配个syslog服务器,记录log,以备差错或排故。
本文出自 “server & security” 博客,请务必保留此出处http://ciscoskys.blog.51cto.com/1066670/871788
内外流量与程序会话

一、.背景描述
1.网络环境配置为中心站点shanghai与分支站点nanjing
2.中心站点拥有三个区域:外网区域、内网区域、DMZ区域
3.DMZ区域拥有企业内部服务器(DNS、WEB、Email、FTP)并且通过SSH和HTTPS加密方式进行远程管理
4.中心站点dmz地址池:172.18.100.0/24
中心站点inside地址池:172.18.101.0/24
二、基于区域的防火墙关键配置
如何放行out访问DMZ的正常访问流量?
关键在于如何定义什么是正常的访问流量。
DMZ内部部署有企业的服务器(DNS、WEB、Email、FTP)并且通过SSH和HTTPS加密方式进行远程管理,那么这些流量就是正常的流量,表示为:
http 80
https 443
ftp 20/21
pop3 110
imap 143
imap over ssl 993
ssh 22
smtp 25
命令表示为:
流量map匹配规则:
注意match-any与match-all的差异
| class-map type inspect match-any dns.traffic.any.class match protocol dns match protocol http match protocol https match protocol icmp class-map type inspect match-any multi.traffic.any.class match protocol dns match protocol http match protocol https match protocol smtp match protocol pop3 match protocol imap match protocol imap3 match protocol ssh match protocol icmp class-map type inspect match-all multi.traffic.all.class match access-group name multi.traffic.acl match class-map multi.traffic.any.class class-map type inspect match-all dns.traffic.all.class match access-group name dns match class-map dns.traffic.any.class class-map type inspect match-any app.inspect.class match protocol ssh match protocol ftp match protocol pop3 match protocol imap3 match protocol smtp match protocol http match protocol https match protocol icmp |
符合就放行,并进行检测会话
不符合就默认丢弃
| policy-map type inspect out.dmz.policy class type inspect multi.traffic.all.class inspect class class-default drop policy-map type inspect dmz.out.policy class type inspect dns.traffic.all.class inspect class class-default drop policy-map type inspect in.dmz.policy class type inspect app.inspect.class inspect class class-default drop |
只要是连接外网的网络设备,一般都要设定NAT,ip地址有限,都是money,性能与费用是要权衡的噢。。
根据DMZ提供的服务,配置如下:
关键服务都是必须设定为静态映射,其他内部访问外网使用动态映射即可。
看服务,看端口,这个要熟悉。
| ip nat inside source static tcp 172.18.100.14 80 interface Serial1/0 80 ip nat inside source static tcp 172.18.100.12 443 interface Serial1/0 443 ip nat inside source static tcp 172.18.100.13 22 interface Serial1/0 22 ip nat inside source static udp 172.18.100.2 53 interface Serial1/0 53 ip nat inside source static tcp 172.18.100.2 110 interface Serial1/0 110 ip nat inside source static tcp 172.18.100.2 143 interface Serial1/0 143 ip nat inside source static tcp 172.18.100.2 993 interface Serial1/0 993 ip nat inside source static tcp 172.18.100.2 20 interface Serial1/0 20 ip nat inside source static tcp 172.18.100.2 21 interface Serial1/0 21 ip nat inside source static tcp 172.18.100.2 25 interface Serial1/0 25 ip nat inside source list nat-i-o interface Serial1/0 overload |
好了,我们来看看详情
先看nat 转换
内部client ping 分支站点,成功启用动态映射
分支站点ssh管理,dzm区域设备,成功登陆
分支站点成功访问web服务器
分支站点成功通过https访问加密服务
| shanghai#show ip nat tr Pro Inside global Inside local Outside local Outside global icmp 200.0.10.2:2 172.18.100.2:2 200.0.30.2:2 200.0.30.2:2 tcp 200.0.10.2:20 172.18.100.2:20 --- --- tcp 200.0.10.2:21 172.18.100.2:21 --- --- tcp 200.0.10.2:22 172.18.100.13:22 172.18.103.3:49392 172.18.103.3:49392 tcp 200.0.10.2:22 172.18.100.13:22 200.0.30.2:17648 200.0.30.2:17648 tcp 200.0.10.2:22 172.18.100.13:22 --- --- tcp 200.0.10.2:25 172.18.100.2:25 --- --- udp 200.0.10.2:53 172.18.100.2:53 --- --- tcp 200.0.10.2:80 172.18.100.14:80 172.18.103.3:49480 172.18.103.3:49480 tcp 200.0.10.2:80 172.18.100.14:80 172.18.103.3:49481 172.18.103.3:49481 tcp 200.0.10.2:80 172.18.100.14:80 172.18.103.3:49482 172.18.103.3:49482 tcp 200.0.10.2:80 172.18.100.14:80 --- --- tcp 200.0.10.2:110 172.18.100.2:110 --- --- tcp 200.0.10.2:143 172.18.100.2:143 --- --- tcp 200.0.10.2:443 172.18.100.12:443 172.18.103.3:49476 172.18.103.3:49476 tcp 200.0.10.2:443 172.18.100.12:443 172.18.103.3:49477 172.18.103.3:49477 tcp 200.0.10.2:443 172.18.100.12:443 172.18.103.3:49478 172.18.103.3:49478 tcp 200.0.10.2:443 172.18.100.12:443 172.18.103.3:49479 172.18.103.3:49479 tcp 200.0.10.2:443 172.18.100.12:443 --- --- tcp 200.0.10.2:993 172.18.100.2:993 --- --- tcp 200.0.10.2:18018 172.18.100.2:18018 172.18.103.3:80 172.18.103.3:80 |
| shanghai#show policy-map ty in zone-pair se policy exists on zp in2dmz Zone-pair: in2dmz Service-policy inspect : in.dmz.policy Class-map: app.inspect.class (match-any) Match: protocol ssh 2 packets, 48 bytes 30 second rate 0 bps Match: protocol ftp 0 packets, 0 bytes 30 second rate 0 bps Match: protocol pop3 0 packets, 0 bytes 30 second rate 0 bps Match: protocol imap3 0 packets, 0 bytes 30 second rate 0 bps Match: protocol smtp 0 packets, 0 bytes 30 second rate 0 bps Match: protocol http 0 packets, 0 bytes 30 second rate 0 bps Match: protocol https 0 packets, 0 bytes 30 second rate 0 bps Match: protocol icmp 0 packets, 0 bytes 30 second rate 0 bps Inspect Number of Established Sessions = 1 Established Sessions Session 68A2ED20 (172.18.101.2:55222)=>(172.18.100.13:22) ssh:tcp SIS_OPEN/TCP_ESTAB Created 00:01:45, Last heard 00:01:40 Bytes sent (initiator:responder) [936:1164] Class-map: class-default (match-any) Match: any Drop 4 packets, 96 bytes policy exists on zp out2dmz Zone-pair: out2dmz Service-policy inspect : out.dmz.policy Class-map: multi.traffic.all.class (match-all) Match: access-group name multi.traffic.acl Match: class-map match-any multi.traffic.any.class Match: protocol dns 0 packets, 0 bytes 30 second rate 0 bps Match: protocol http 0 packets, 0 bytes 30 second rate 0 bps Match: protocol https 0 packets, 0 bytes 30 second rate 0 bps Match: protocol smtp 0 packets, 0 bytes 30 second rate 0 bps Match: protocol pop3 0 packets, 0 bytes 30 second rate 0 bps Match: protocol imap 0 packets, 0 bytes 30 second rate 0 bps Match: protocol imap3 0 packets, 0 bytes 30 second rate 0 bps Match: protocol ssh 0 packets, 0 bytes 30 second rate 0 bps Match: protocol icmp 0 packets, 0 bytes 30 second rate 0 bps Inspect Number of Established Sessions = 2 Established Sessions Session 68A2E620 (172.18.103.3:49392)=>(172.18.100.13:22) ssh:tcp SIS_OPEN/TCP_ESTAB Created 00:06:11, Last heard 00:05:51 Bytes sent (initiator:responder) [3433:3004] Session 68A2E9A0 (200.0.30.2:17648)=>(172.18.100.13:22) ssh:tcp SIS_OPEN/TCP_ESTAB Created 00:03:17, Last heard 00:01:25 Bytes sent (initiator:responder) [1832:3160] Class-map: class-default (match-any) Match: any Drop 4 packets, 96 bytes policy exists on zp dmz2out Zone-pair: dmz2out Service-policy inspect : dmz.out.policy Class-map: dns.traffic.all.class (match-all) Match: access-group name dns Match: class-map match-any dns.traffic.any.class Match: protocol dns 0 packets, 0 bytes 30 second rate 0 bps Match: protocol http 0 packets, 0 bytes 30 second rate 0 bps Match: protocol https 0 packets, 0 bytes 30 second rate 0 bps Match: protocol icmp 0 packets, 0 bytes 30 second rate 0 bps Inspect Number of Established Sessions = 1 Established Sessions Session 68A2D120 (172.18.100.14:62666)=>(172.18.103.3:80) http:tcp SIS_OPEN/TCP_ESTAB Created 00:25:14, Last heard 00:25:13 Bytes sent (initiator:responder) [0:0] Class-map: class-default (match-any) Match: any Drop 0 packets, 0 bytes |
1.基于区域的防火墙,默认是各区域之间各不相通的,所以必须明确配置策略用以放行所需流量,这是状态化防火墙,只要被监控放行流量,那么他也会放回流量。
2.本拓扑包含三个方向策略:
inside ——》DMZ
outside——》DMZ
DMZ——》outside
一般来说还得有inside——》outside
但是如果企业对于员工上网管理很严的话,那么这也是一个精细配置工作。
3.配置前一定要理清思路,哪些流量要放行,哪些流量要drop,NAT配置要精准,TCP还是udp,要查清楚,还有就是ftp,存在多个端口的服务
4.设定默认路由条目,必备的,你不可能对外网配个动态路由协议,与ISP起邻居,那样的话,神了^_^
5.最好配个syslog服务器,记录log,以备差错或排故。
本文出自 “server & security” 博客,请务必保留此出处http://ciscoskys.blog.51cto.com/1066670/871788
相关文章推荐
- 【Firewall系列二】解析基于区域的防火墙方案如何过滤内网用户web访问
- linux_如何在Linux上配置基于Web的网络流量监控系统
- Linux环境下基于条件约束的HTTP/TCP透明代理和流量牵引方案
- RMI网络编程开发之二 如何搭建基于JDK1.5的分布式JAVA RMI 程序
- 如何在Linux上配置基于Web的网络流量监控系统
- 如何配置防火墙和 Windows Media Services 9 系列的网络地址转换 (NAT)
- 如何在Linux上配置基于Web的网络流量监控系统
- 网络采集软件核心技术剖析系列(7)---如何使用C#语言搭建程序框架(经典Winform界面,顶部菜单栏,工具栏,左边树形列表,右边多Tab界面)
- RMI网络编程开发之二 如何搭建基于JDK1.5的分布式JAVA RMI 程序
- 基于网络环境的程序设计综合实验报告
- VC++如何使用Mschart 实例-------网络流量监控程序
- VC++如何使用Mschart 实例-------网络流量监控程序
- Cacti 是一套基于PHP,MySQL,SNMP及RRDTool开发的网络流量监测图形分析工具
- Windows 网络服务架构系列课程详解(八) --windows域环境多区域间访问
- RMI网络编程开发之二 如何搭建基于JDK1.5的分布式JAVA RMI 程序
- 【疑难杂症系列】如何通过流量控制来防止网络攻击
